Very High
CVE-2024-3094
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2024-3094
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
Malicious code was discovered in the upstream tarballs of xz, starting with version 5.6.0.
Through a series of complex obfuscations, the liblzma build process extracts a prebuilt object file from a disguised test file existing in the source code, which is then used to modify specific functions in the liblzma code. This results in a modified liblzma library that can be used by any software linked against this library, intercepting and modifying the data interaction with this library.
Add Assessment
Ratings
-
Attacker ValueVery High
-
ExploitabilityVery Low
Technical Analysis
The backdoor is present in versions 5.6.0 and 5.6.1.
This one has gained significant attention over the past few days. To date, there is has been observation that this backdoor was ever leveraged, and it will be unlikely to do so now, given the attention that it has received.
From a Technical perspective, this one was difficult to detect and prevent since the payload was loaded and executed in memory (as part of the SSHD process). The backdoor allowed remote code to be executed via the SSH process, making it even harder to detect.
This backdoor was only discovered by chance, by a Microsoft developer at Microsoft, Andres Freund. Andres was investigating a performance issue in SSH (which was caused by the backdoor), and then stumbled upon the backdoor. Details of which can be found on their post: https://www.openwall.com/lists/oss-security/2024/03/29/4. Also worth noting that the backdoor was not introduced into the code of xz, but rather the binaries. This means if you built the binaries from source, you did not include the backdoor.
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportRatings
-
Attacker ValueVery High
-
ExploitabilityVery Low
Technical Analysis
xz backdoor leads to authentication bypass on OpenSSH. So this remote account takeover on vulnerable systems.
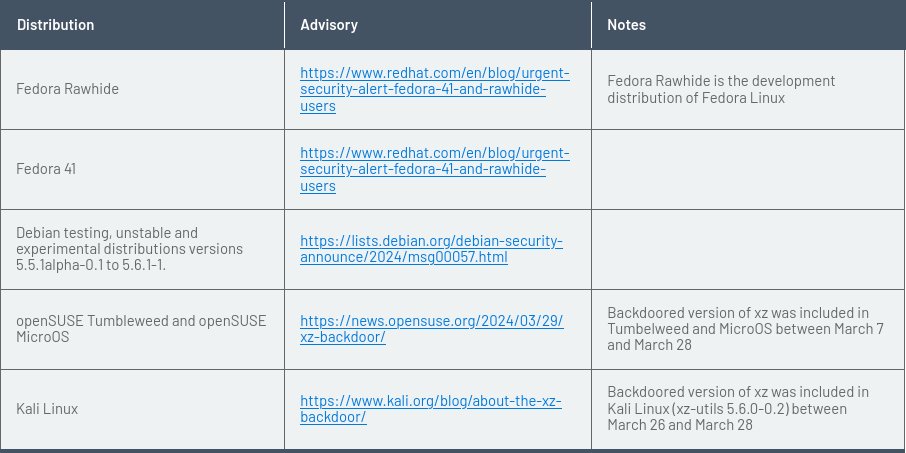
Many linux distributions were not impacted because of various reasons:
- they were packing older version of xz where the backdoor was not introduced yet (e.g. Debian stable)
- they were building from source
- they didn’t patched OpenSSH to use liblzma (e.g. ArchLinux: news, advisory)
- they don’t even use xz (e.g. Amazon Linux)
Unaffected distribution examples:
Affected distribution examples (which are mostly unstable version of major distros + Kali):
A Nessus plugin is available for detection (n° 192708):
- https://www.tenable.com/plugins/nessus/192708
- more plugins for xz backdoor: https://www.tenable.com/cve/CVE-2024-3094/plugins
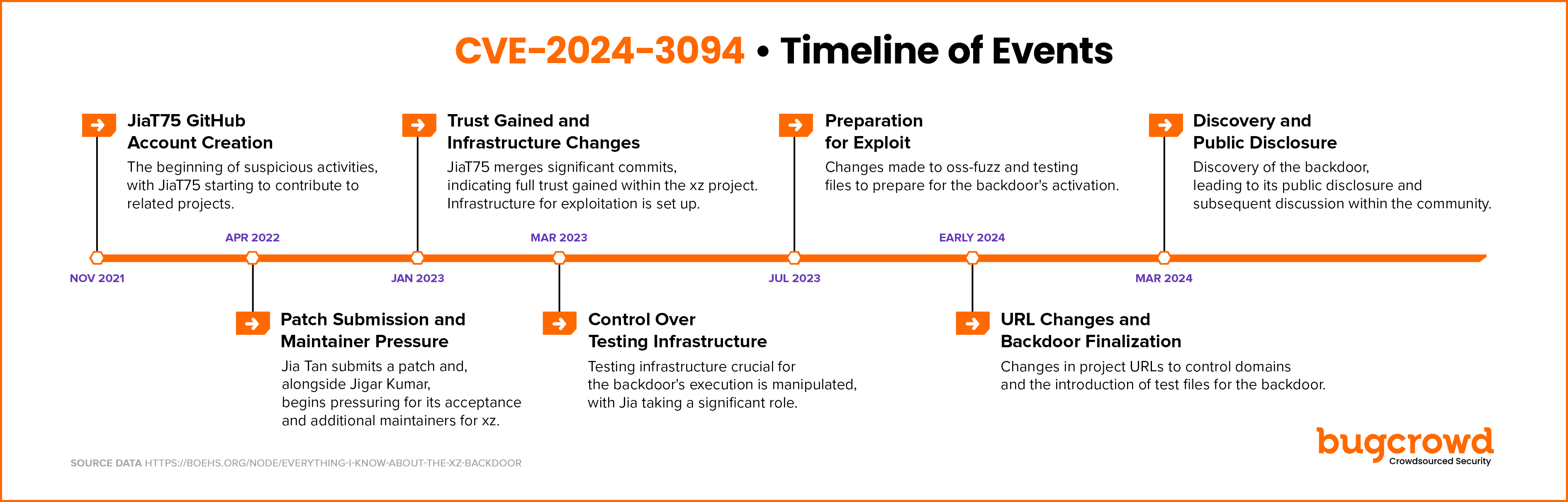
@fr0gger_ published an outbreak visual of the whole backdoor chain:
Timeline summary:
Analysis:
- smx – xz backdoor analysis and symbol mapping
- gynvael – xz/liblzma: Bash-stage Obfuscation Explained
- FAQ
- boehs – timeline
- openwall
- Wiz -Backdoor in XZ Utils allows RCE: everything you need to know
- binarly – XZ Utils Supply Chain Puzzle: Binarly Ships Free Scanner for CVE-2024-3094 Backdoor
- Microsoft – FAQ and guidance for XZ Utils backdoor
Potential nuclei templates (PR not merged yet):
- https://github.com/projectdiscovery/nuclei-templates/pull/9458/files
- https://github.com/projectdiscovery/nuclei-templates/pull/9464/files
YARA rules:
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportRatings
Technical Analysis
On the one hand, it’s backdoored software, so “exploitation” could arguably have already occurred (in the form of an already executed supply chain attack). On the other hand, it’s not immediately clear that anyone has used this backdoor to do specific Bad Things™, so “exploited in the wild” doesn’t sound quite right either. Developers probably most at risk here rather than production systems, but it would appear this got caught pretty quickly.
Bad:
- Backdoor!
- In a popular command-line tool
- Made it into unstable branches/bleeding-edge releases of some distros (Kali, Arch, etc)
- “Open source is unsafe” commentary (c’mon, y’all)
- Salacious! Speculation runs rife! xz is drowning out Kate Middleton conspiracy theories in my timelines!
Good:
- Didn’t make it into prod systems, stable branches unaffected
- Not a simple attack
- Not clear that anyone is actively using this backdoor for badness — private SSH key still hasn’t shown up
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Exploited in the Wild
Would you like to delete this Exploited in the Wild Report?
Yes, delete this reportReferences
Exploit
A PoC added here by the AKB Worker must have at least 2 GitHub stars.
Miscellaneous
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below: