Getting Started
- Join the AttackerKB Community
- View the Home Page
- Search for Vulnerabilities
- Create an Assessment
- Upvote, Downvote, or Comment on Other Users' Assessments
- Visit Your Profile Page
- View the Leaderboard
- Subscribe to RSS feeds
Frequently Asked Questions
Getting Started
Join the AttackerKB Community
You can sign into AttackerKB using your GitHub credentials. AttackerKB uses GitHub as an OAuth provider. The site does not store any user data that is not already public on GitHub.
Once you are signed into AttackerKB, you can:
View the Home Page
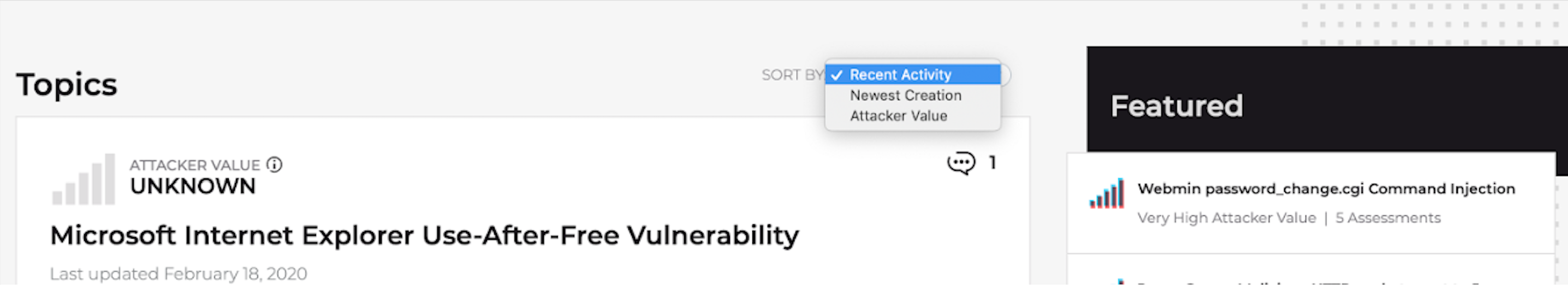
You can view topics and vulnerabilities based on Recent Activity, Newest Creation, and Attacker Value. AttackerKB administrators will also select specific topics for the “Featured” section. Criteria for Featured Topics will vary. These can be topics that have been in the news recently, have gotten a lot of attention from AttackerKB users, or just vulnerabilities that we’d like AttackerKB users to assess.
Search for Vulnerabilities
You can search by CVE or keyword. New vulnerabilities are automatically imported from public data sources hourly.
Create an Assessment
Click “Add Assessment” at the top of a vulnerability or topic page.
Rate vulnerabilities based on how important or useful you think they are to attackers and how easy the vulnerability is to exploit.
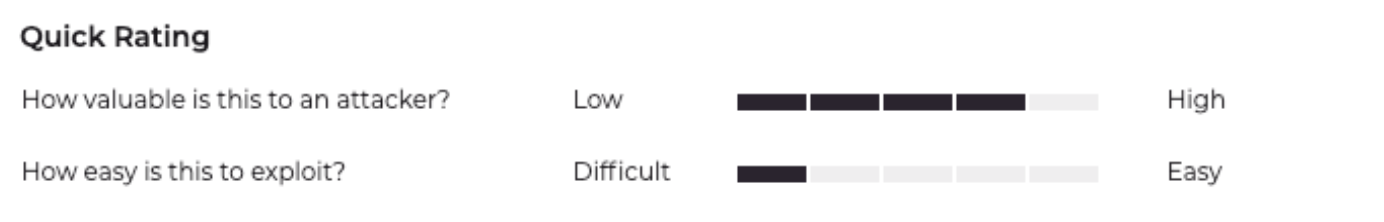
- Attacker Value Definition: How valuable is this vulnerability to an attacker? How likely is it that exploitation of this vulnerability could be used by an attacker to access valuable data, network, or computing resources?
- Exploitability Value Definition: How easily exploitable is this vulnerability in real environments? Is there practical exploit code available that is proven to work against real targets? Is the attack easy to execute successfully, or is it only executable in contrived lab settings?
You can also select pre-populated characteristics commonly associated with high-value and low-value vulnerabilities. We provided some examples to help you get started, but understand this isn’t a complete list. If you feel there are other characteristics that help justify your attacker value rating, please document them in your technical assessment.
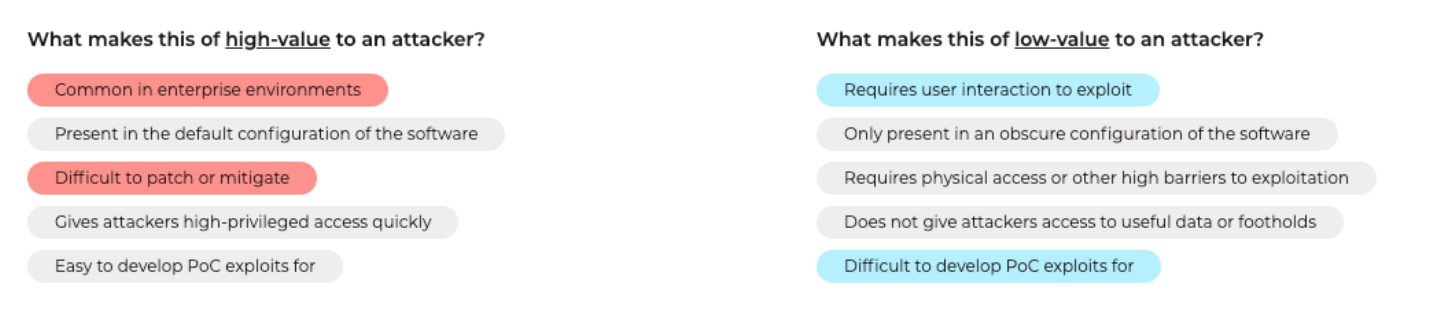
We encourage all users to add their own commentary and notes to each vulnerability they rate. The analysis portion is meant to guide other security professionals and help them understand the true risk and urgency within their own environment in a way that a ranking or score cannot provide on its own.

Tips for Writing a Quality Technical Analysis
- Use Markdown for formatting
- Long blocks of text can be boring, no matter how great the content. Better formatting can help other users consume the information and usually yields more community responses.
- Explain how the vulnerability can be used by attackers
- Defend your Attacker Value rating
- Why is this vulnerability high or low value to an attacker?
- What would an attacker be able to accomplish or access?
- Is there a POC or module available?
- Are there any conditions that would need to be satisfied first before that could happen?
- For example: "An attacker would need to be on the local area network" or "This could only be accomplished if the default value for the encryption key was left unchanged..."
- Provide mitigation advice
-
- Are there other things an organization can do to mitigate risk other than just apply a path?
- Are some organizations more at risk than others?
Scores of each vulnerability are displayed in aggregate at the top of the page.

Upvote, Downvote, or Comment on Other Users' Assessments
We all have a variety of experiences and opinions, so we encourage users to vote based on quality of content.
Think someone made a compelling case for their Attacker Value rating and provided a lot of valuable information? Upvote it.
Did someone provide an assessment that didn’t really contribute to the conversation or was off topic? Downvote it.
Think someone is missing information that might change their analysis? Comment on their assessment to provide feedback or ask a question.
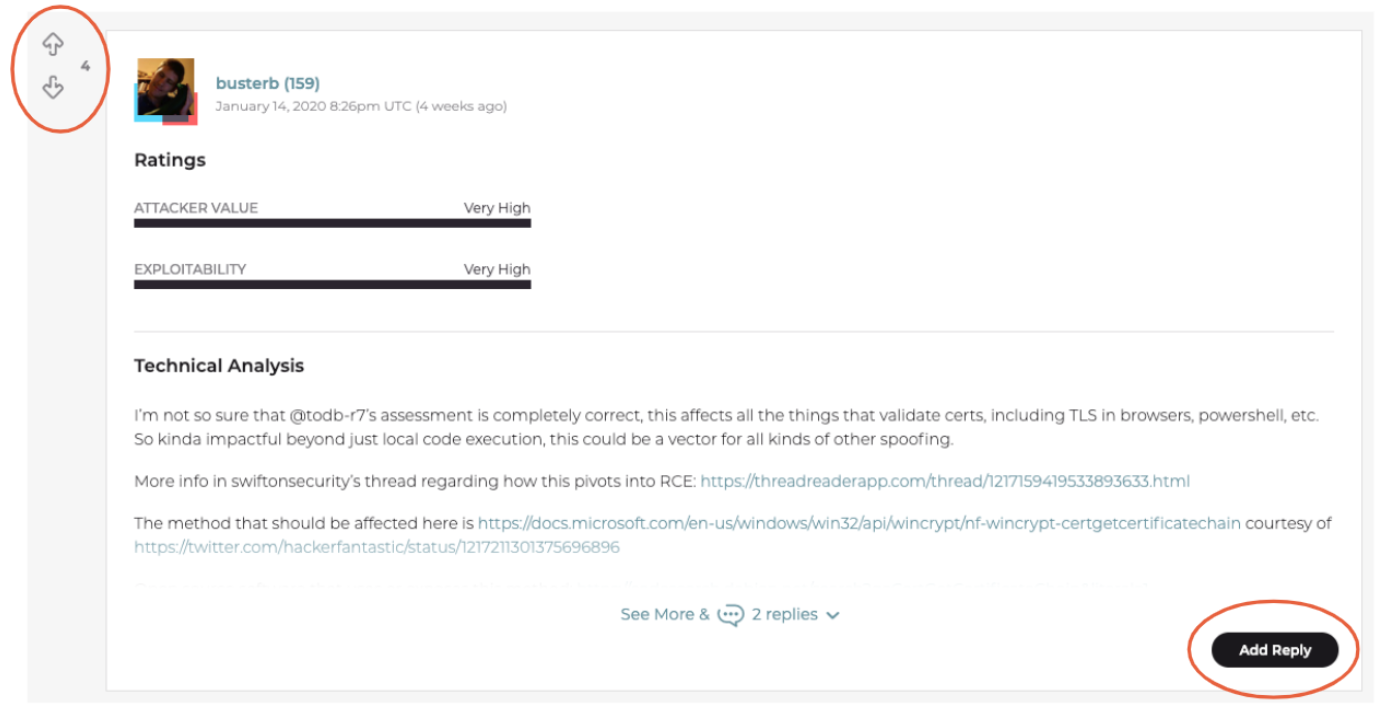
Visit Your Profile Page
You can see what you've assessed or commented on in the past and your user score. For more information on how your user score is calculated, see “How do I score user profile points?” in the FAQs section.

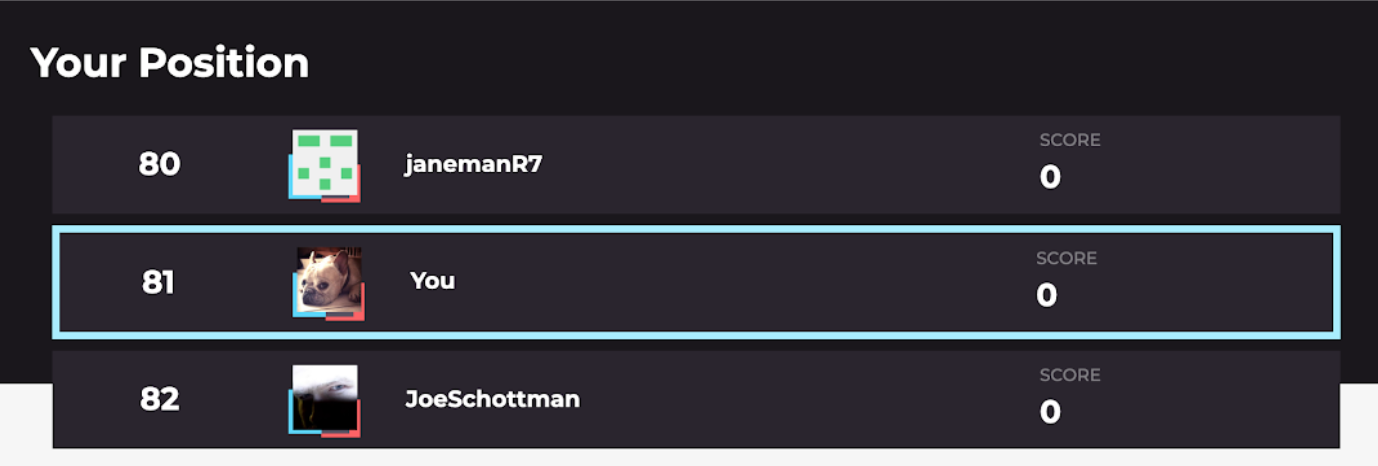
View the Leaderboard
The leaderboard will highlight the top ten contributors to AttackerKB and show your individual rank.
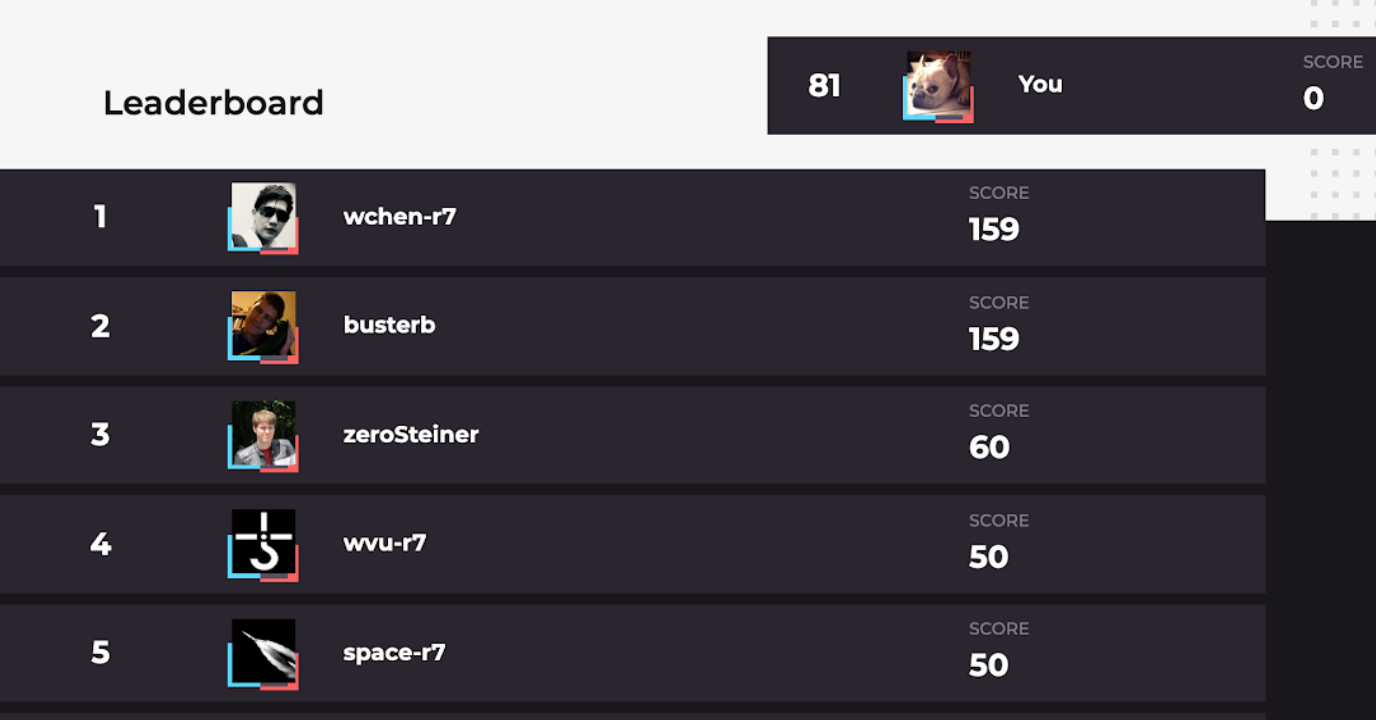
You can also see the scores of the community members above and below you on the leaderboard.This will allow you to calculate how many points you need to advance in rank.
Frequently Asked Questions
How do I create a new topic?
Search for the CVE identifier, keyword, or term related to the topic you would like to view. If the search does not return a result, you will be given the option to create a new topic.
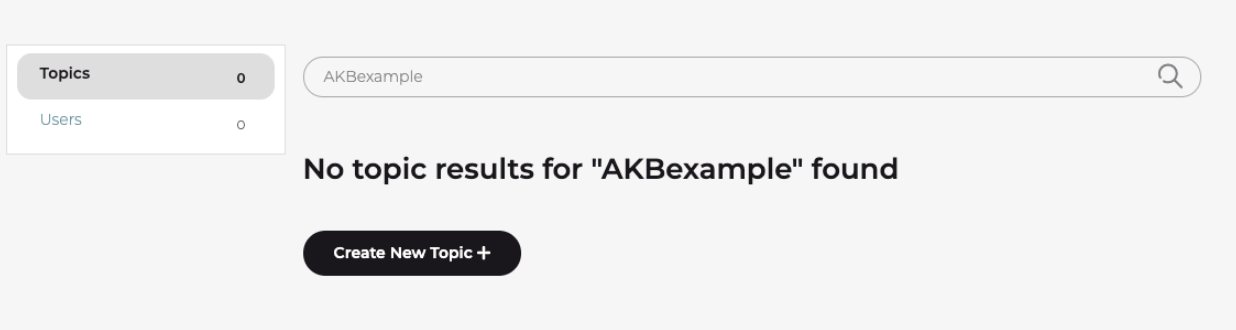
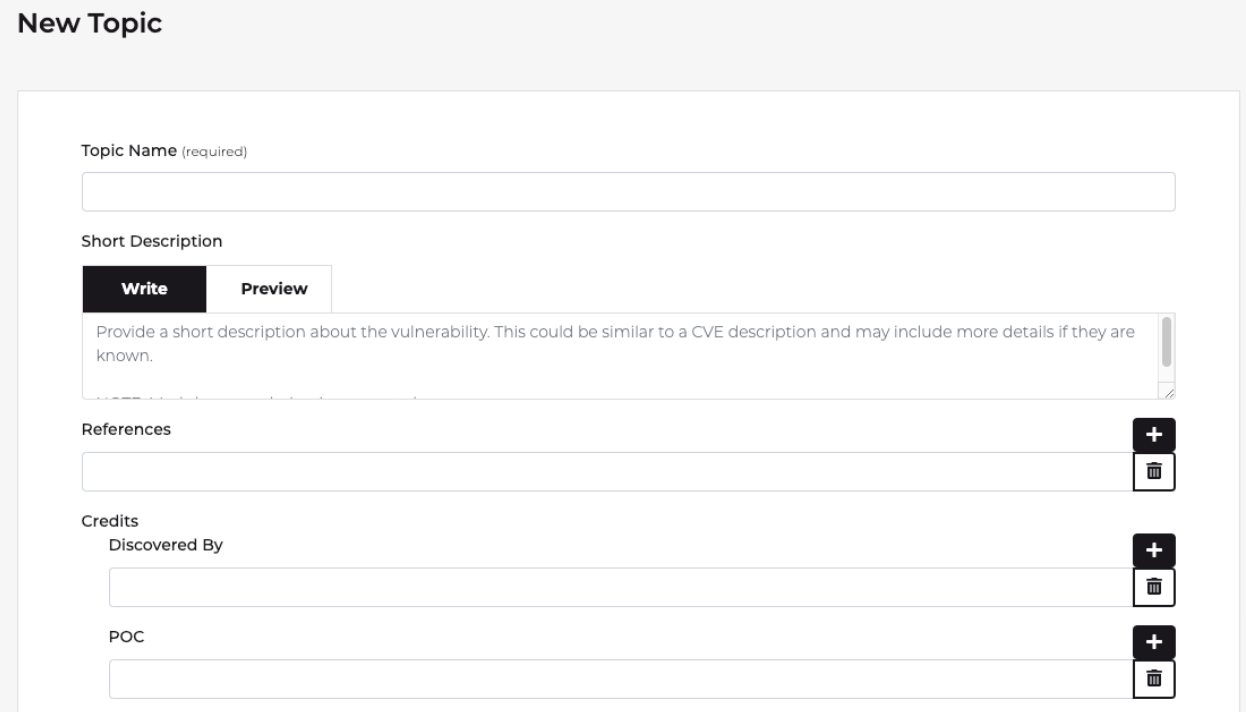
Select the “Create New Topic” button, provide a topic name, and fill out all known fields in the new topic form.
How do I add an image to an assessment?
AttackerKB supports Markdown text. You will need to host the image first and then link to it. Add an exclamation mark (!) followed by alt text in brackets ([ ]) and the path or URL in parentheses.
| Markdown: | ![Logo] (https://www.metasploit.com/includes/images/metasploit-og.png) |
| Output: |  |
How do I score user profile points?
User profile scores are calculated by the number of assessments you’ve created, plus the number of upvotes or downvotes.
Example: User A has created the two assessments below for a total of 9 points.
- Assessment #1 - 5 upvotes
- 1 point for the assessment + 5 points for upvotes = 6
- Assessment #2 - 3 upvotes, 1 downvote
- 1 point for the assessment + 3 points for upvotes - 1 point for downvote = 3
We consider the user profile score still a work in progress. If you have suggestions on a better way to calculate user profile scores, please share them with us! You can provide feedback though the feedback feature on the AttackerKB site, or in the AttackerKB Slack workspace.
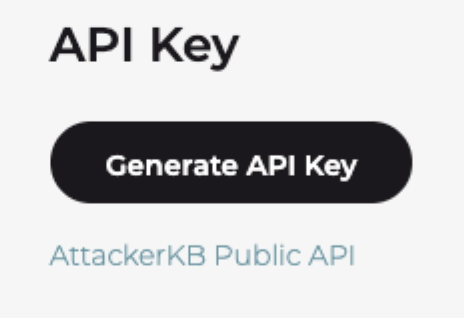
Is there an API?
Yes! Navigate to your profile page and select the “Settings” tab under your username. Under the API Key section, you can generate your own API key. There is also a link to all our AttackerKB Public API documentation.
How do I submit feedback?
There are two ways to submit potential issues, bugs, enhancements, or feature ideas. The first is through the blue Submit Feedback button in the lower left-hand corner of each page.
The second is through the AttackerKB Slack workspace. You can talk to the AttackerKB team directly, learn about the latest updates and features to the site, and collaborate with other AttackerKB community members.
How will AttackerKB respond to my feedback?
While the AttackerKB team might not be able to respond directly to each feedback submission, we find all feedback extremely useful -- so keep it coming! The AttackerKB team regularly monitors activity in both the attackerkb GitHub repository and in the AttackerKB Slack workspace. All feedback is reviewed and taken into consideration when planning the AttackerKB roadmap.
Our team will occasionally share new AttackerKB features and improvements in Slack, so please join our slack workspace to stay up-to-date with our progress.
How do I format my assessments using Markdown?
You can find several Markdown guides online , but here are some of the more common formatting options used by AttackerKB community members:
| Markdown: |
I want to insert a block quote here: > Text > Text > More Text |
| Output: |
I want to insert a block quote here:Text |
| Markdown: | **bold text** |
| Output: | bold text |
| Markdown: |
Insert bulleted list here: - Bullet 1 - Bullet 2 - Bullet 3 |
| Output: |
Insert bulleted list here:
|
Code
To denote content in a sentence as code, enclose with a backtick `
| Markdown: | `code` |
| Output: |
code
|
Code Blocks
You can create fenced code blocks by using triple backticks ``` before and after your code.
| Markdown: |
I want to insert a code block here ``` Insert code here ``` |
| Output: |
I want to insert a code block hereInsert code here
|
| Markdown: |
Text *** Text |
| Output: |
Text
Text |
| Markdown: | *italicized text* |
| Output: | italicized text |
| Markdown: | For more information, visit [AttackerKB] (https://attackerkb.com) |
| Output: | For more information, visit AttackerKB |