Very High
CVE-2022-21906
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
Very High
(1 user assessed)Very High
(1 user assessed)Unknown
Unknown
Unknown
CVE-2022-21906
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
Windows Defender Application Control Security Feature Bypass Vulnerability
Add Assessment
Ratings
-
Attacker ValueVery High
-
ExploitabilityVery High
Technical Analysis
CVE-2022-21906
Microsoft
Vendor

Description
Windows Defender Application Control Security Feature Bypass Vulnerability.
The attacker can execute extremely dangerous apps by using different scenarios,
directly from the user profile, without any reaction from the side of the Windows Defender.
Read more: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-21906
The latest version of Windows 10 Pro, plus the latest update!
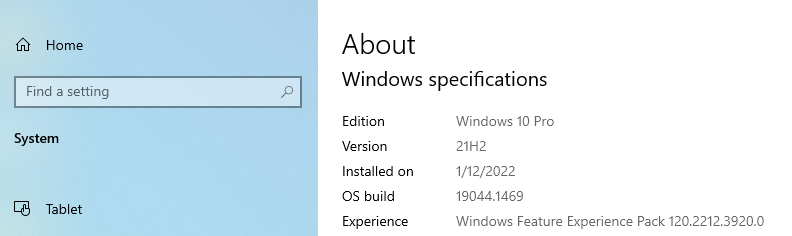
Reproduce:
Proof and Exploit
BugCheck after the exploit, the reaction of the kernel:
BSOD.exe
1: kd> !analyze ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* Unknown bugcheck code (c0000022) Unknown bugcheck description Arguments: Arg1: 0000000000000000 Arg2: 0000000000000000 Arg3: 0000000000000000 Arg4: 0000000000000000 Debugging Details: ------------------ ERROR_CODE: (NTSTATUS) 0xc0000022 - {Access Denied} A process has requested access to an object, but has not been granted those access rights. BUGCHECK_CODE: c0000022 BUGCHECK_P1: 0 BUGCHECK_P2: 0 BUGCHECK_P3: 0 BUGCHECK_P4: 0 PROCESS_NAME: BSOD.exe SYMBOL_NAME: nt!PopTransitionSystemPowerStateEx+1217 MODULE_NAME: nt IMAGE_NAME: ntkrnlmp.exe FAILURE_BUCKET_ID: STATUS_ACCESS_DENIED_nt!PopTransitionSystemPowerStateEx FAILURE_ID_HASH: {7fcb0a96-b639-2e09-82d6-2eef48bdcdea} Followup: MachineOwner ---------
malicious.exe
0: kd> !analyze ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* Unknown bugcheck code (c0000022) Unknown bugcheck description Arguments: Arg1: 0000000000000000 Arg2: 0000000000000000 Arg3: 0000000000000000 Arg4: 0000000000000000 Debugging Details: ------------------ ERROR_CODE: (NTSTATUS) 0xc0000022 - {Access Denied} A process has requested access to an object, but has not been granted those access rights. BUGCHECK_CODE: c0000022 BUGCHECK_P1: 0 BUGCHECK_P2: 0 BUGCHECK_P3: 0 BUGCHECK_P4: 0 PROCESS_NAME: malicious.exe SYMBOL_NAME: nt!PopTransitionSystemPowerStateEx+1217 MODULE_NAME: nt IMAGE_NAME: ntkrnlmp.exe FAILURE_BUCKET_ID: STATUS_ACCESS_DENIED_nt!PopTransitionSystemPowerStateEx FAILURE_ID_HASH: {7fcb0a96-b639-2e09-82d6-2eef48bdcdea} Followup: MachineOwner ---------
BR
nu11secur1ty
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
References
Miscellaneous
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
