Moderate
CVE-2022-21970
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
Moderate
(1 user assessed)Moderate
(1 user assessed)Unknown
Unknown
Unknown
CVE-2022-21970
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
Add Assessment
Ratings
-
Attacker ValueMedium
-
ExploitabilityMedium
Technical Analysis
CVE-2022-21970
Description
Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability.
This vulnerability allows an attacker to execute javascript code on every host without permission, also an attacker can steal local system files, and also he can manipulate the actions against the machine and result in changing internal developer settings in Microsoft Edge.
- NOTE: In this example, Microsoft Edge executes a malicious script without problems.
This is just a malicious .bat file that reboots the infected machine, and it’s only for testing!
The attacker can create a malicious file that can take a privileges escalation, malware, spyware, or kernel exploit file and harm seriously your device!
Not correctly sanitizing and checking for that what users download on their machines by using a MsEdge!
NOTE after the exploit: A malicious user, or whatever user can execute directly malicious .bat files which are created – generated from this javascript exploit by using MsEdge. 😁
According to Edge, this file is safe to run and open. 😁
FAQ
What is the version information for this release?
Microsoft Edge Version Date Released Based on Chromium Version
97.0.1072.55 | 1/6/2022 | 97.0.4692.71
STATUS:
- Patched and fixed on!

The next test is checking if this is fully patched! 🤫 😛 😎
Proof and simple browser test MsEdge: Edge is blocking .sys files because they can harm your device:
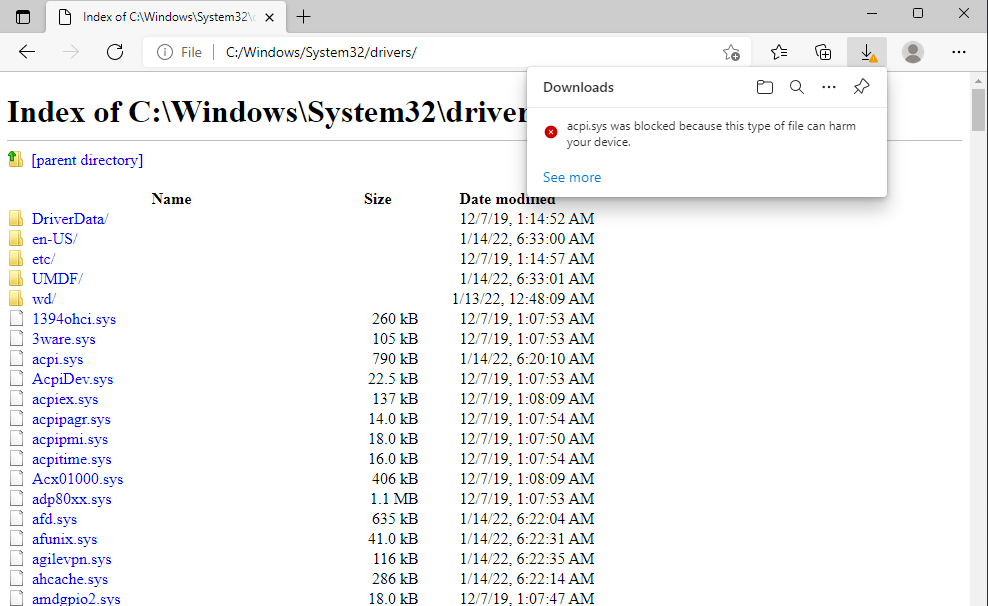
This proof of concept is shown as to how the MsEdge browser NOT blocking .bat files, and this is a problem.
NOTE: A malicious user, or whatever user can execute directly malicious
.batfiles which are created – generated by using exactly MsEdge and thisjavascript exploit.
This is ridiculous and incorrect sanitizing!😁
According to Edge, this file is safe to run and open. 😁
Screenshot, example:
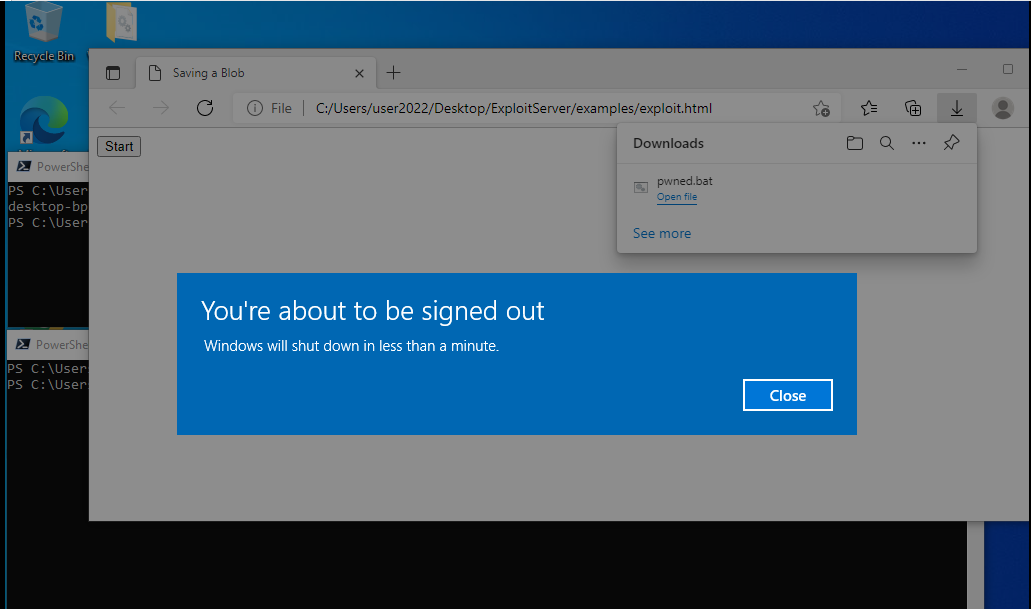
In Action:
download the PoC
extracted somewhere
Execute
start msedge C:\Users\user2022\Desktop\ExploitServer\examples\exploit.html
Example from the function():
$start.onclick = () => { const blob = new Blob(['shutdown /r']) const fileStream = streamSaver.createWriteStream('pwned.bat', { size: blob.size // Makes the percentage visiable in the download })
Reproduce:
Proof and Exploit:
- BR nu11secur1ty
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
References
Exploit
A PoC added here by the AKB Worker must have at least 2 GitHub stars.
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
