Very High
CVE-2020-35665
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2020-35665
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
An unauthenticated command-execution vulnerability exists in TerraMaster TOS through 4.2.06 via shell metacharacters in the Event parameter in include/makecvs.php during CSV creation.
Add Assessment
Ratings
-
Attacker ValueVery High
-
ExploitabilityVery High
Technical Analysis
Last two weeks, I spent some time on a TerraMaster F2-221 NAS server that I got from an old friend running TerraMaster Operating System (TOS) 4.x.
Research on the Internet shows that this server is full with vulnerabilities up to TOS 4.2.29. Surprisingly, no Metasploit modules were made to exploit these NAS servers and there are still plenty of vulnerable NAS servers connected to the Internet.
So I took the liberty to write three nice modules that exploits these NAS servers targeting different vulnerabilities.
This article is covering the first of three modules, called TerrorMaster 1 like we do with “good” movies released in the cinema. You can find the articles on TerrorMaster 2 here and TerrorMaster 3 here.
In December 2020, the IHTeam reported multiple vulnerabilities on TerraMaster NAS devices running TOS version 4.2.06 or lower.
You can read their analysis/advisory here.
TerrorMaster 1 is exploiting a vulnerability described in CVE-2020-35665 or CVE-2020-28188 that allows an unauthenticated attacker to create /upload a webshell via shell metacharacters in the Event parameter using the vulnerable endpoint include/makecvs.php during the CSV creation process.
You can find the module here in my local repository or as PR 18063 at the Metasploit Github development.
Mitigation
Please update your TOS version up to the latest supported TOS 4.2.x version or TOS 5.x version to be protected against all known vulnerabilities.
I strongly advice NOT to expose your TerraMaster NAS devices directly to the Internet, because you could end-up in a situation depicted below where your server has become a victim of ransomware.
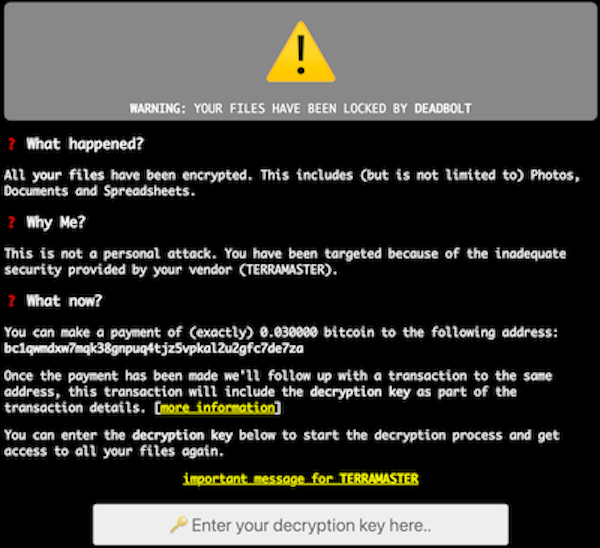 .
.
References
IHTeam advisory
TerrorMaster 1 – h00die-gr3y Metasploit local repository
TerrorMaster 1 – Metasploit PR 18063
TerrorMaster 2
TerrorMaster 3
Credits
IHTeam
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Exploited in the Wild
- Vendor Advisory (https://forum.terra-master.com/en/viewtopic.php?f=6&t=3031)
- News Article or Blog (https://thehackernews.com/2022/03/critical-bugs-in-terramaster-tos-could.html)
Would you like to delete this Exploited in the Wild Report?
Yes, delete this reportReferences
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
