Moderate
CVE-2024-52052
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
Moderate
(1 user assessed)Very High
(1 user assessed)Unknown
Unknown
Unknown
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
Wowza Streaming Engine below 4.9.1 permits an authenticated Streaming Engine Manager administrator to define a custom application property and poison a stream target for high-privilege remote code execution.
Add Assessment
Ratings
-
Attacker ValueMedium
-
ExploitabilityVery High
Technical Analysis
Wowza Streaming Engine below v4.9.1 on Windows and Linux is vulnerable to high-privilege remote code execution via the Manager HTTP service (port 8088). An authenticated Wowza Streaming Engine administrator can define a custom application property and poison a stream target for remote code execution as root on the host system. Notably, this vulnerability can be chained with CVE-2024-52053 by an unauthenticated attacker to automatically trigger arbitrary code execution on the server when an admin views the dashboard.
Target Software
Wowza Streaming Engine is media server software used by many organizations for livestream broadcasts, video on-demand, closed captioning, and media system interoperability. The Wowza Streaming Engine Manager component is a web application, and it’s used to manage and monitor Wowza Media Server instances. At the time of publication, approximately 18,500 Wowza Streaming Engine servers are exposed to the public internet, and many of those systems also expose the Manager web application. The testing target was Wowza Streaming Engine v4.8.27+5, the latest version available at the time of research.
Analysis
Wowza Streaming Engine administrators can create new video applications from the Streaming Engine Manager web dashboard. In addition to a variety of default application properties, custom properties can be assigned as key-value entries in video application settings.
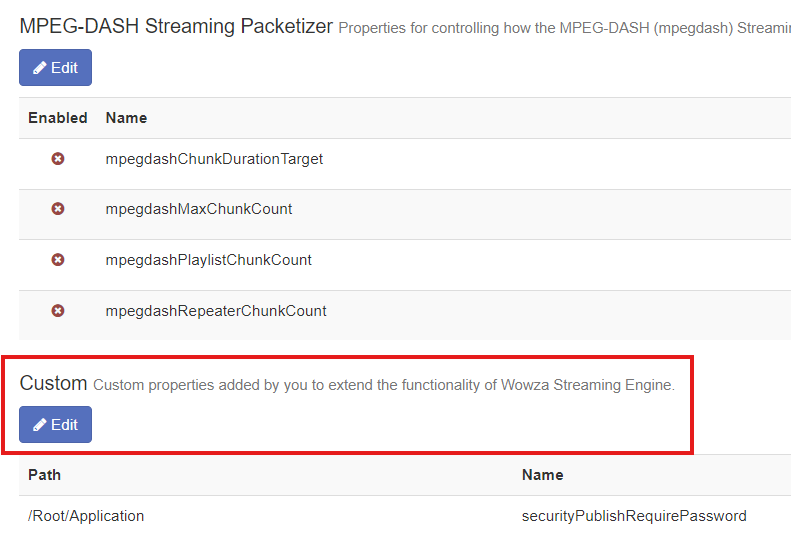
Furthermore, Wowza Streaming Engine features the ability to configure video applications to distribute live streams to CDNs. As outlined in the documentation, the custom application property pushPublishMapPath can be set to assign a JSON map file for stream targets. The recommended value is ${com.wowza.wms.context.VHostConfigHome}/conf/${com.wowza.wms.context.Application}/PushPublishMap.txt. An example of one such newly generated empty PushPublishMap.txt file is below.
# This file has been upgraded for use by the Wowza Streaming Engine REST API. Please avoid hand-editing.
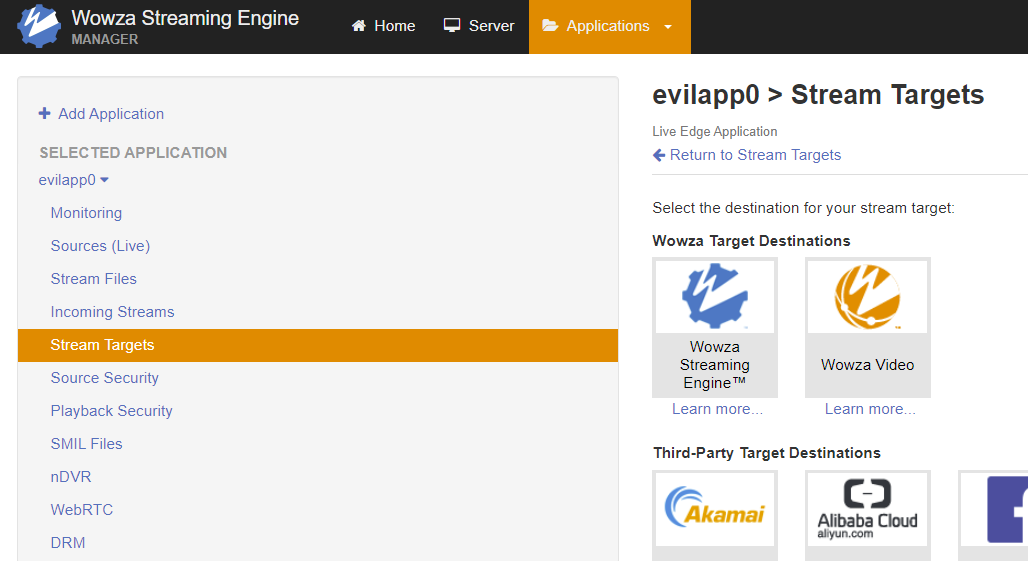
Though the file is empty by default, Stream Targets can be configured to populate the file. The screenshots below depict this taking place for an ‘evilapp0’ Live Edge application. Placeholder data is submitted in form fields.
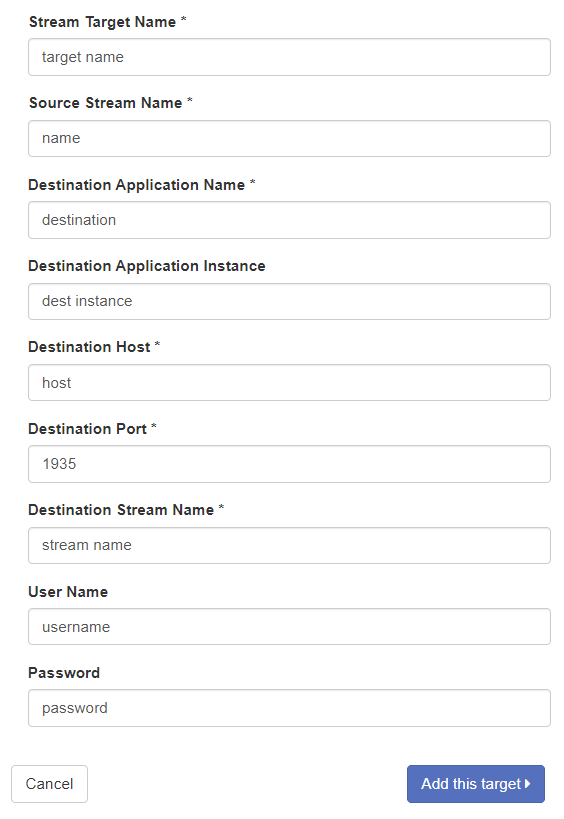
After clicking “Add this target”, a JSON string is added on a new line in the PushPublishMap.txt file.
# This file has been upgraded for use by the Wowza Streaming Engine REST API. Please avoid hand-editing. name={"entryName":"target name", "profile":"rtmp", "wowzaVideoTranscoder.height":"0", "userName":"username", "streamName":"stream name", "wowzaVideoTranscoder.width":"0", "password":"password", "application":"destination", "destinationName":"wowzastreamingengine", "host":"host", "appInstance":"dest instance"}
Crucially, the expected “.txt” extension for the previously mentioned pushPublishMapPath property value is not validated. As a result, the file name, path, and extension for the above PushPublishMap file can be arbitrarily specified to facilitate remote code execution. In the context of a JSP web application, files in the web root with a “.jsp” extension will be treated as executable files.
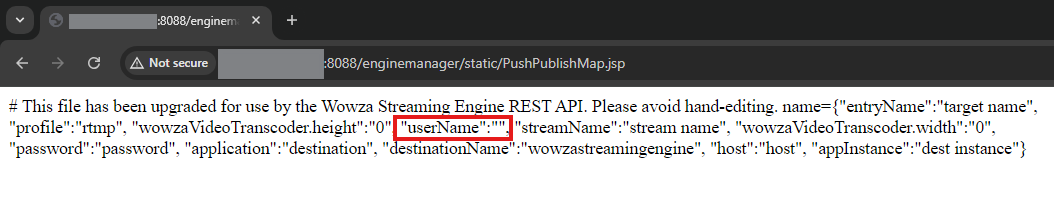
An authenticated attacker can forego the recommended file path and name in favor of ${com.wowza.wms.context.VHostConfigHome}/manager/temp/webapps/enginemanager/static/PushPublishMap.jsp , which results in a file written in the web root directory with an executable JSP extension. As we’ve established, tainted data is included in the PushPublishMap file within JSON rows. Because of this, arbitrary JSP code can be injected into our executable file via the ‘userName’ JSON key value to gain remote code execution on the server.
Notably, in this JSON context, double quotes and commas are “bad characters” for Stream Target data; if bad characters are submitted in the Stream Targets fields, the resulting JSON data is truncated with a ‘null’ row. An example of this is shown below.
# This file has been upgraded for use by the Wowza Streaming Engine REST API. Please avoid hand-editing. null={"entryName":"StreamTarget-1721859230601", "profile":"unknown", }
Now, we’ll show an example of arbitrary remote code execution via JSP injection within the ‘userName’ JSON key value. The StringBuilder class is used in our proof-of-concept exploit, since single quotes work for char definitions and double quotes can’t be used for string definitions. Multiple directive attributes are used for imports to avoid comma bad characters. When the malicious JSP file is accessed from a web browser, the code will execute and a new file called “rce” will be created in the /tmp folder on the host. This payload is shown below.
<%@ page import='java.io.*' %><%@ page import='java.util.*' %><% StringBuilder filePath = new StringBuilder(); filePath.append('/').append('t').append('m').append('p').append('/').append('r').append('c').append('e'); String concatFile = filePath.toString(); File file = new File(concatFile); file.createNewFile(); %>
After injecting the payload into the JSON via userName, browsing to the newly-written PushPublishMap.jsp file reveals that the file is in the expected location. The JSP scripts injected into the userName value are not visible, indicating that they’ve been processed by the Java web server. Since the page returns a “200” status, the code appears to have been executed successfully.
This is confirmed by viewing the /tmp directory on the host, where a root-owned file called “rce” has been created. This indicates remote code execution on the host has been achieved.
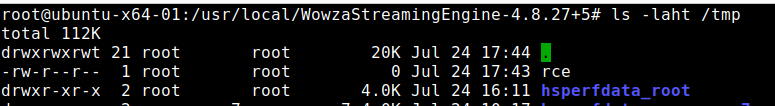
Per Wowza documentation, the code execution context is privileged – root on Linux, LocalSystem on Windows. The AttackerKB entry for CVE-2024-52053 contains an exploit payload that chains an unauthenticated injection vulnerability with CVE-2024-52052 for unauthenticated root RCE with passive user interaction.
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportGeneral Information
Vendors
- Wowza
Products
- Streaming Engine
References
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
