Very High
CVE-2021-41675
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2021-41675
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
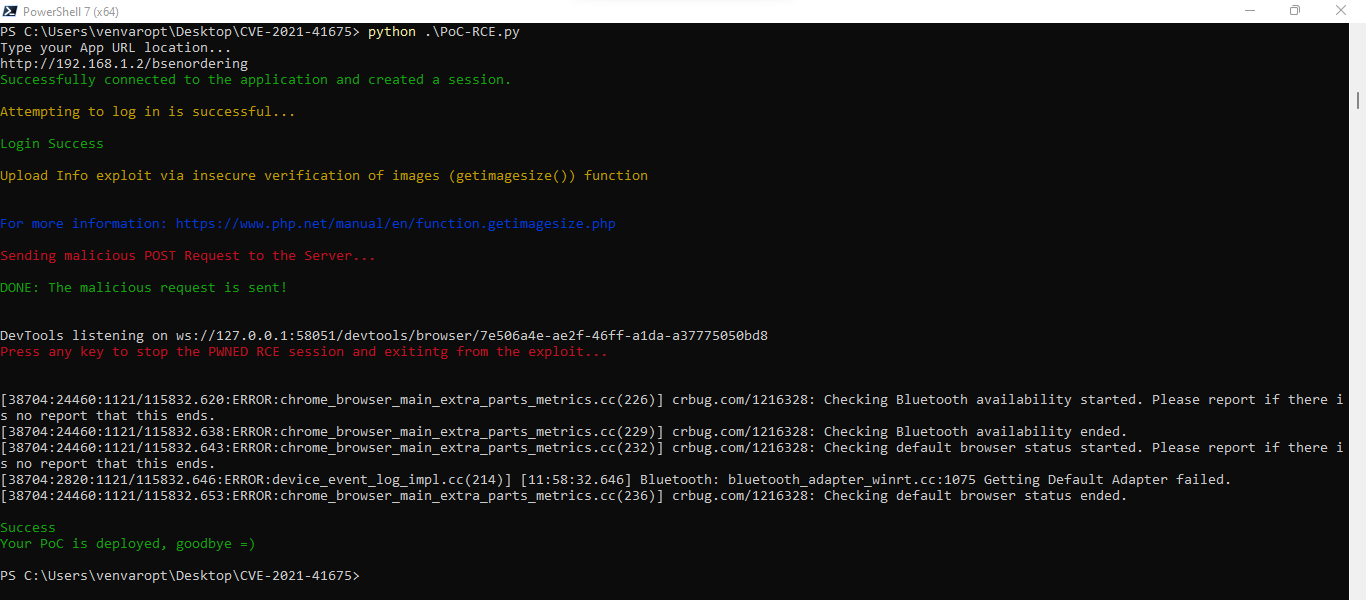
A Remote Code Execution (RCE) vulnerabilty exists in Sourcecodester E-Negosyo System 1.0 in /admin/produts/controller.php via the doInsert function, which validates images with getImageSizei. .
Add Assessment
Ratings
-
Attacker ValueVery High
-
ExploitabilityVery High
Technical Analysis
CVE-2021-41675
Vendor
Author and redevelopment of the PoC
nu11secur1ty
First cool ;) Idea:
- Thank you, dear friend!
Janik Wehrli
Description:
A Remote Code Execution (RCE) vulnerability exists in Sourcecodester E-Negosyo System 1.0 in /admin/produts/controller.php via the do Insert function, which validates images with getImageSizei… More about the function: https://www.php.net/manual/en/function.getimagesize.php The attacker can deploy malicious RCE files bypassing this function, and after that, he can use the directory traversal method, to navigate to the /uploaded_photos/ directory which is another and actual problem of this system. After the problem, which is – no sanitizing of the function “(getimagesize())” on this system, the attacker can execute the malicious RCE code, and then he can retrieve all sensitive information about the App on this server, and all architecture of this server. CONCLUSION: There is no proper disinfection of “(getimagesize())” function, and correctly protecting the directory /uploaded_photos/.
Reproduce:
Proof and exploit:
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
- e-negosyo system project
Products
- e-negosyo system 1.0
References
Additional Info
Technical Analysis
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
